- Vulnerable U
- Posts
- 🎓️ Vulnerable U | #125
🎓️ Vulnerable U | #125
Hackers using AI in new ways, Soldier pleads guilty to hacking and extortion, Salt Typhoon undetected in gov network for 9 months, and more!
Read Time: 8 minutes

Brought to you by:
Howdy friends!
Who’s ready for Vegas? Enough of you said you wanted to do a meetup, I’ll grab us some space for lunch one day. What day would you like?
What day would you want to do a lunch meetup?Nights are already booked, lets hang for some food and coffee |
A few of you have upgraded to Vuln U Premium which I appreciate more that you know. I’m still working on some of the content for the first few premium editions that will go out over the next few months. And as promised, I’ll launch a private community once we get critical mass.
If you’re looking to support the newsletter and looking for some premium content/community:
ICYMI
🖊️ Something I wrote: This run through of some new macOS malware disguised as a Zoom update.
🎧️ Something I heard: This great rundown of the recent vulnerability in ‘sudo’ by LowLevel.
🎤 Something I said: What the hell is going on with all these apps/extensions turning into malware?
🔖 Something I read: Google has just used AI and threat intel to foil a zeroday before it could launch
Vulnerable News
I’m always watching for any threat actors using AI, since we haven’t seen a ton, and it’s mostly been on social engineering level up. Ukraine's CERT-UA caught APT28 (aka Fancy Bear) using this Python-based nasty that hooks into Hugging Face's API to generate Windows commands on the fly using Alibaba's Qwen 2.5-Coder LLM. Instead of hardcoding commands that signature-based detection might catch, it's basically asking an AI "hey, how do I steal files from this Windows box?" and getting fresh answers every time.
It's the first publicly documented malware to use LLMs for operational tasks rather than just social engineering. The malware can adapt its tactics mid-compromise without needing new payloads, and using Hugging Face infrastructure for C2 communication is a smart way to blend in with legitimate AI traffic. They're spreading it through the usual spear-phishing emails targeting Ukrainian government officials, but the real story here is how this could change the malware landscape if other groups start copying the approach. (read more)
Join top fraud and cybersecurity leaders to hear how automation is reshaping financial cyber crime and what you can do about it.
🗓️ Thursday, July 31
⏰ 2 PM ET / 11 AM PT
🎙️ Featuring experts:
Allison Miller – Led fraud and cyber teams at Reddit, Google, PayPal, Visa, Bank of America, EA
Kitboga – Scam-baiting improv artist (3.7M+ YouTube subscribers)
Jerry Tylman – Led Fraud Red Teaming for top banks
Brian Silverstein – CEO, MirrorTab; former CTO & Co-founder of Honey (acquired by PayPal)
*Sponsored
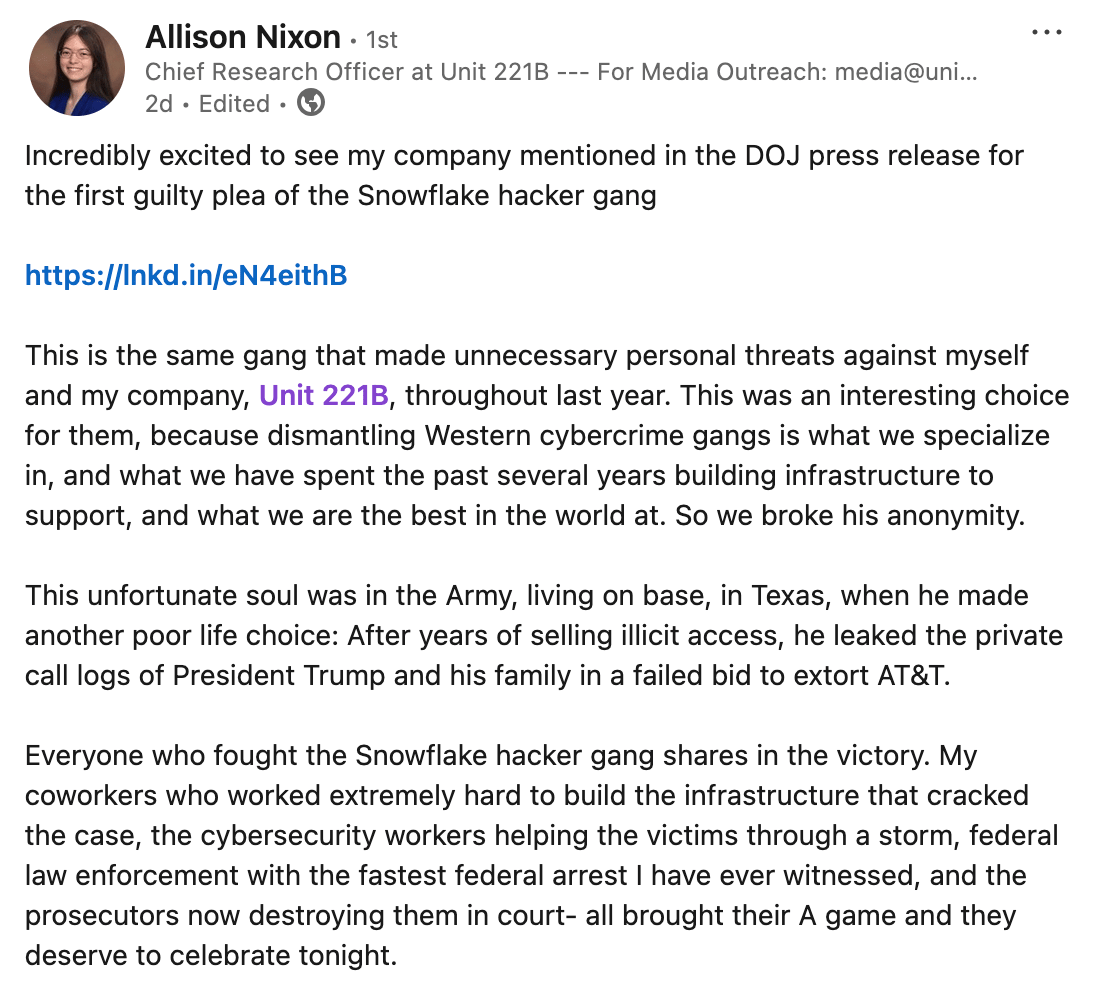
Bad idea to go after people who make their entire living off of finding people like you.
Former Army soldier Cameron John Wagenius, aka "kiberphant0m," just pleaded guilty to a pretty extensive hacking and extortion scheme targeting telecom companies. This guy was running a whole operation - brute forcing his way into victim networks, coordinating with accomplices through Telegram group chats, and then trying to shake down the companies he breached. When extortion didn't work, he'd just sell the stolen data on BreachForums or use it for SIM swapping attacks.
10 victim companies including AT&T and Verizon, where he managed to steal massive amounts of call records. He's also been linked to the broader Snowflake breach fallout that's been causing headaches across the industry. Sentencing is set for October 6th, and he's looking at up to 20 years. (read more)
Chinese espionage groups are going hard after Taiwan's semiconductor industry right now. Proofpoint tracked three different threat actors between March and June 2025 - UNK_FistBump, UNK_DropPitch, and UNK_SparkyCarp - all specifically targeting Taiwan's chip makers, designers, and even investment analysts who cover the sector. Fake job applications from "university students" looking for work, bogus investment collaboration emails, and credential phishing campaigns.
The activity levels are notably higher than what Proofpoint has seen historically, suggesting this is a priority target. UNK_FistBump was particularly busy, using everything from Cobalt Strike to a custom backdoor called Voldemort that uses Google Sheets for C2 (because apparently even Chinese spy craft relies on spreadsheets).(read more)
Salt Typhoon. Undetected. In a U.S. Army National Guard network for nine whole months in 2024. Carried this threat actor to term before detecting!
These Chinese state-sponsored hackers didn't just grab some random files - they walked away with network diagrams, configuration files, admin credentials, and personal info that could be the keys to compromising National Guard and government networks across every other state and at least four territories.
DHS says Salt Typhoon has snagged 1,462 network configuration files from around 70 U.S. government and critical infrastructure entities between 2023-2024. Their playbook is pretty straightforward - exploit old vulnerabilities in Cisco routers and other network gear, then use those stolen config files to map out paths to other juicy targets. The fact that they can stay hidden for nine months while methodically collecting this treasure trove of network intelligence is just wild to me. (read more)
No. This isn’t the same critical unauthenticated Cisco vuln as last week. Or the week before. It’s been a bad summer for Cisco putting up some high scores on the CVSS board.
CVE-2025-20337 impacts their Identity Services Engine (ISE) and scored a perfect 10/10 on the severity scale. This bug lets unauthenticated attackers remotely execute code and potentially grab root privileges on vulnerable devices. It's hitting ISE versions 3.3 and 3.4, and there's no workaround available - you've got to patch your way out of this one.
The third max-severity RCE bug found in ISE recently, joining CVE-2025-20281 and CVE-2025-20282. If you patched those earlier ones, you're still not covered for this new one. Time to upgrade to ISE 3.3 Patch 7 or ISE 3.4 Patch 2 if you're running affected versions. No exploitation seen in the wild yet, but with details public, that clock is ticking. (read more)
Chainalysis just dropped their mid-year crypto crime report and it's got a lot of big numbers in it... And not in a good way. We're looking at over $2.17 billion stolen from crypto services in the first half of 2025 alone, putting us on track for a potential $4+ billion year - absolutely crushing records. The big story here is North Korea's $1.5 billion ByBit hack, which is now the largest single crypto theft in history and accounts for most of this year's damage.
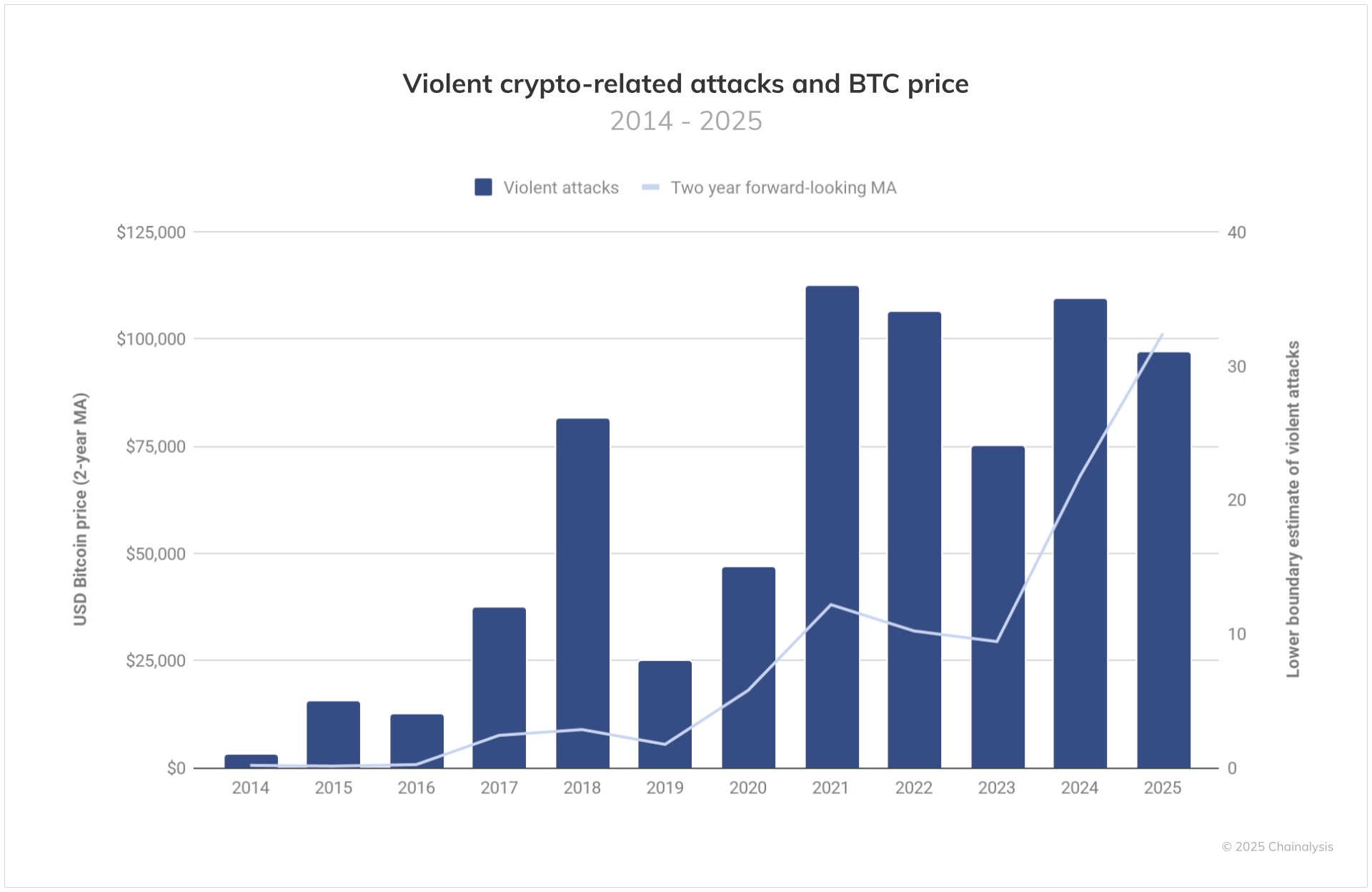
There is also a statistically significant and concerning shift toward targeting individual users. Personal wallet compromises now make up about 23% of all crypto theft. Even more disturbing is the rise in "wrench attacks" where criminals use physical violence to steal crypto, with incidents correlating to bitcoin price movements. (read more)
TeleMessageTM SGNL, an enterprise messaging system that's basically Signal for government agencies and big corporations, has a nasty vulnerability that's leaking sensitive data all over the place. CVE-2025-48927 stems from their use of an old Spring Boot Actuator configuration where the /heapdump endpoint is publicly accessible without any authentication. When exploited, this thing dumps about 150MB of heap memory containing plaintext usernames, passwords, and other juicy data. CISA added it to their KEV catalog on July 14th, so we know its being used in the wild.
GreyNoise is tracking active exploitation with 11 IPs already hitting the vulnerability, plus over 2,000 IPs doing reconnaissance on Spring Boot Actuator endpoints in the past 90 days. (read more)
Google's threat intel folks just dropped a hefty report on some nasty SonicWall exploitation. The group they're calling UNC6148 has been hitting end-of-life SMA 100 series appliances with a previously unknown backdoor called OVERSTEP. Even if you've patched your appliances, these attackers are using credentials and OTP seeds they stole during previous compromises to waltz right back in. OVERSTEP is basically a rootkit that modifies the boot process, hides its own files, and gives attackers persistent shell access through crafted web requests. (read more)
A crypto dev lost $500K after installing what they thought was a legit Solidity syntax highlighter extension for Cursor IDE (the VSCode-based AI editor). The malicious extension, which racked up an artificially inflated 54,000 downloads on Open VSX, deployed ScreenConnect for remote access and dropped some nasty payloads including Quasar RAT and PureLogs stealer. (read more)
A critical train brake vulnerability discovered in 2005 is finally getting fixed after multiple researchers and 20 years of industry pushback. The protocol linking End-of-Train (EoT) and Head-of-Train (HoT) devices has zero authentication or encryption, letting attackers manipulate train brakes with just $500 in radio equipment. CISA's new advisory (CVE-2025-1727) confirms what researcher Neil Smith found in 2012 - you can remotely control train brakes from long distances, potentially causing derailments or system-wide shutdowns. (read more)
Miscellaneous mattjay

How'd I do this edition?It's hard doing this in a vacuum. Screaming into a void. Feedback is incredibly valuable to make sure I'm making a newsletter you love getting every week. |
Parting Thoughts:
Community was foundational in launching and propelling my career. Community is the only reason I can stand being in Texas during the summer months. Community is the point. Today, I invite you to embrace discomfort on the road to a more vulnerable you.
Stay safe, Matt Johansen
@mattjay



