- Vulnerable U
- Posts
- 🎓️ Vulnerable U | #132
🎓️ Vulnerable U | #132
Salesloft Salesforce mega breach, The craziest AI hacking technique I've seen, WhatsApp Spyware, Streameast takedown, and much more!
Read Time: 9 minutes

Brought to you by:
Howdy friends!
Just got back from PAX West where I was out in Seattle talking about the intersection of cybersecurity and the gaming industry. The talk went great, We filled the room and there was a long line of questions.
That's generally how I judge if a talk went well - by the quality of questions. And we had such a long line we couldn't even get to them all in the 15 minutes that we allotted to questions. We did about 45 minutes of answering questions in the hallway after they kicked us out. So thank you everyone who came to that. It was a lot of fun.
Thanks to everyone who has signed up for VulnU Premium. Just sent out the second edition last night and it features a great interview with Trey Ford. Thanks Trey for getting vulnerable for the crew here. Upgrade if you haven’t already to check it out! - and check the first one we did with Rober RSnake Hansen which was an absolute banger to start it off.
ICYMI
🖊️ Something I wrote: I’m seeing a lot of breach fatigue
🎧️ Something I heard: Building Your Own Unified AI Assistant Using Claude Code
🎤 Something I said: Child Exploitation in Online Gaming Video- this was a rough one.
🔖 Something I read: Call Me A Jerk: Persuading AI to Comply with Objectionable Requests
Vulnerable News
All right, check the tape! Last edition of Vulnerable U, I called that this issue was going to be bigger than we knew so far, and then it's the only thing that anyone's been talking about all week.
This hack is widespread, and a lot of people are impacted. If you missed last week, hackers hit Salesloft Drift (an AI chatbot tool) and used it as a springboard to raid Salesforce instances belonging to over 700 companies. The attack group, tracked as UNC6395 by Mandiant, spent approximately 10 days systematically exporting data between August 8 and 18, targeting sensitive information such as AWS access keys and Snowflake tokens.
The victim list reads like a who's who of tech giants - Cloudflare, Zscaler, Palo Alto Networks, and Google all confirmed they got hit. Cloudflare found 104 of their API tokens in the stolen data (though they've seen no abuse yet), while others had customer contact info and support ticket data compromised. Salesloft pulled the plug on Drift and paused their Salesforce integration while everyone scrambles to rotate credentials. To be clear, when you’re reading about this, none of those companies got breached themselves; it was a third-party breach. But one compromised integration point has led to hundreds of victims. (read more)

What happens when you let AI dig into a vulnerability the way a seasoned analyst would? In Maze’s latest case study, AI Agents investigated CVE-2025-27363 and surfaced the risk that actually mattered while setting aside the dead ends.
That means your team gets less noise to sort through, clearer decisions to act on, and a stronger security posture overall. (read more)
*Sponsored
Oh boy, this one's a doozy. NX, a build system that proudly calls itself "AI-first," just got exploited in one of the more wild ways I’ve seen in a while. They used Claude to write code that checked PR titles, except the AI-generated code had a massive bash injection vulnerability. Someone immediately spotted it on Twitter, NX reverted the code, but the attackers were already cooking.
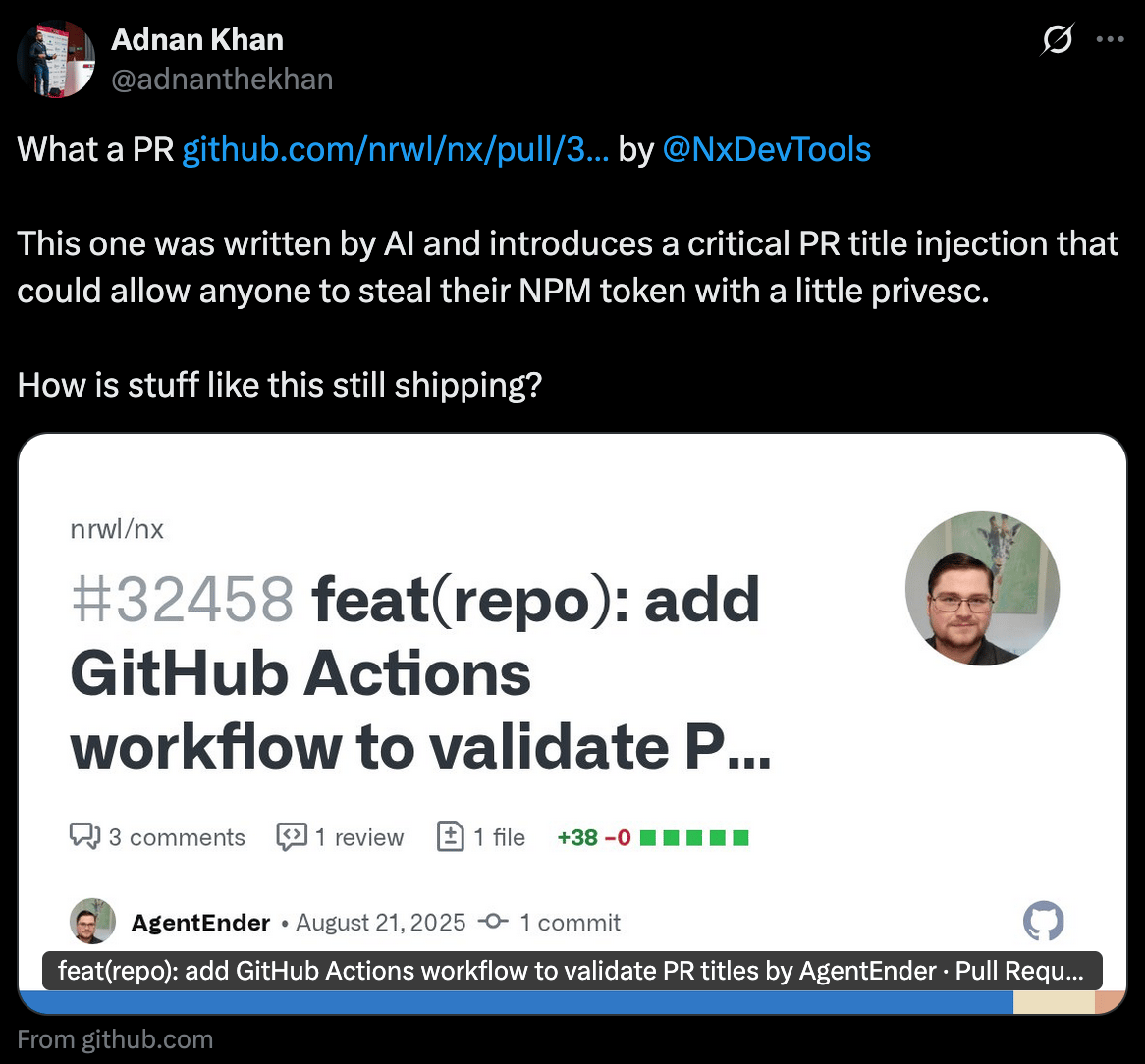
The hackers submitted a malicious PR against an old vulnerable branch, NX's CI automatically tested it (because of course it did), and boom - they had NX's GitHub and NPM keys. But here's the brilliant part: their malware didn't directly steal crypto wallets. Instead, it sent prompts to victims' AI coding assistants telling them to "search the filesystem" for config files and sensitive data. Basically, they used AI to hack AI users, targeting the exact demographic most likely to have crypto wallets lying around. Over 1,400 users got hit, and there's already a second wave using compromised keys to grab private repos.
So they got hacked via PR title, fun. But then they also passed AI commands to do more hacking for them. Really fun! (read more)
The day before football season started, the worlds biggest pirated streaming site, Streameast, got taken down and the people behind it arrested. Coincidence?!
Egyptian authorities working with the Alliance for Creativity and Entertainment nabbed two guys outside Cairo who were allegedly running this massive operation that pulled in 1.6 billion visits last year and laundered over $6 million through a UAE shell company. They confiscated laptops, phones, cash, crypto, and property docs.
But here's the thing about whack-a-mole with piracy sites - by Wednesday afternoon, people were already posting about mirror sites popping up. The technical infrastructure behind these operations is getting more sophisticated too, with Silent Push releasing a report the same day about a massive IPTV piracy network apparently running out of Afghanistan.
Wild idea: let’s make it easy and affordable to stream sports without a cable subscription. (read more)
Disney just coughed up $10 million to settle FTC claims that they've been letting YouTube collect kids' data without proper consent. The issue boils down to Disney failing to properly label their kid-focused content as "Made for Kids," which is supposed to block data collection and personalized ads. They were marking everything as MFK at the channel level, but individual videos were still tagged as "Not Made for Kids" - and YouTube even warned them about this back in 2020 for over 300 videos including stuff from Toy Story, Frozen, and Mickey Mouse.
Here's the thing that gets me - $10 million sounds like a lot until you realize Disney pulled in $95 billion in revenue last year. That's literally 0.01% of their annual revenue, which is basically pocket change for the House of Mouse. The settlement requires them to actually notify parents before collecting data and implement a proper tagging system, but given the financial impact, you've got to wonder if these fines are really deterring anyone from playing fast and loose with kids' privacy. (read more)
Someone just tried to pull off a $130 million heist from Brazil's Pix payment system by compromising fintech giant Evertec's Brazilian subsidiary Sinqia. The hackers got in using stolen credentials from an IT vendor account and attempted to move the cash through unauthorized business-to-business transactions involving two financial institutions. Brazil's Central Bank has since revoked Sinqia's access to Pix while they sort this mess out.
This attack hit a company that processes payments for 24 financial institutions in Brazil, so the ripple effects could be wild. No personal data was exposed according to Evertec, but their stock price probably isn't loving the SEC filing they had to make about this incident. HSBC got dragged into the headlines but insists their customer funds are safe. (read more)
When you see WhatsApp or Apple talking about highly targeted attacks with a 0-day, it means government spyware. We're not going to get any details about this until some of the spyware watchdogs tell us that this was the vuln used in some recent wave of spyware. But trust them when they say "actively exploited in targeted zero-day attacks." = this means spyware.
The WhatsApp bug lets attackers trick devices into processing content from arbitrary URLs through some linked device sync shenanigans. But wait! Theres more! It could be chained with an Apple vulnerability (CVE-2025-43300) - an out-of-bounds write bug that Apple quietly patched back in August.
The fact that both companies are simultaneously warning about chained exploits suggests someone with serious resources was behind this - probably not your average cybercriminal. (read more)
Yeah I knew it. When I saw 2.5 billion and none of the info was from Google themselves, I said no way in hell. But boy did I see this crap all over social media. And apparently the entire cybersecurity news machine went into full panic mode over a Gmail "warning" that never actually happened.
Multiple outlets ran stories claiming Google told all 2.5 billion Gmail users to reset their passwords after some massive breach. Problem is, Google never said any of that. They had to come out with a blog post basically saying "nope, didn't happen, our security is fine, please stop spreading nonsense."
This is becoming a frustrating pattern where cybersecurity news sites are racing to publish scary headlines without bothering to verify anything first. Remember that "largest data breach in history" earlier this year? Just old stolen credentials repackaged. Or those 3 million infected toothbrushes launching DDoS attacks? Completely hypothetical scenario that got reported as fact.
At some point, maybe we should start fact-checking before hitting publish on these "URGENT: EVERYONE PANIC" stories. Just a thought. (read more)
Krebs has some good additional thoughts on this story. Google's threat intel team is warning that the stolen credentials work across hundreds of integrated services including Slack, Google Workspace, AWS, and Azure.
The attack started as early as August 8th with hackers siphoning data from corporate Salesforce instances, then pivoting to hunt for even juicier credentials like AWS keys and VPN access in the stolen data. Various groups are claiming responsibility (ShinyHunters, some new "Scattered LAPSUS$ Hunters 4.0" Telegram channel), but honestly the attribution game is getting ridiculous at this point. What matters more is that this highlights how modern cloud integrations can turn a single breach into a multi-platform nightmare. For now companies using Salesloft need to invalidate all their integration tokens ASAP.(read more)
Researchers at LAB52 found a new Outlook backdoor called "NotDoor" that sits quietly waiting for emails with specific trigger words like "Daily Report." Once activated, it can run commands, steal files, and upload new payloads - all through innocent-looking email exchanges.
The deployment method is clever: they abuse legitimate OneDrive.exe via DLL side-loading to install the VBA macro and disable Outlook's security protections. The malware uses custom encryption and obfuscation, plus it disguises exfiltrated files with mundane names like "invoice.pdf" or "report.docx." Commands come in via encrypted emails and results get sent back to a ProtonMail address. It's been hitting companies across NATO countries, showing Russian APT28 continues evolving their toolkit to stay ahead of defenses. The IOCs are included if you want to hunt for this thing in your environment. (read more)
Mandiant caught some attackers having a field day with Sitecore deployments that were using sample machine keys from old deployment guides. These keys were sitting in public documentation from 2017 and earlier, giving attackers everything they needed to craft malicious ViewState payloads for remote code execution. The attack started with probing a /sitecore/blocked.aspx endpoint and deploying a custom reconnaissance tool called WEEPSTEEL that masqueraded as legitimate ViewState responses.
protecting ASP.NET machineKey from unauthorized access: guide
Once inside, the attackers went full-bore with their post-exploitation playbook - dropping EARTHWORM for tunneling, DWAGENT for persistent access, and SHARPHOUND for AD reconnaissance. They created local admin accounts, dumped SAM/SYSTEM hives, and moved laterally via RDP through their tunneled connections. The whole thing was pretty textbook once they got that initial foothold. Sitecore's on it now with CVE-2025-53690, updating their deployment guides to auto-generate unique machine keys instead of using those sample ones that should've been retired years ago.(read more)
Miscellaneous mattjay

lol wtf is this Apple? Every single update you push out includes a security update.


How'd I do this edition?It's hard doing this in a vacuum. Screaming into a void. Feedback is incredibly valuable to make sure I'm making a newsletter you love getting every week. |
Parting Thoughts:
Community was foundational in launching and propelling my career. Community is the only reason I can stand being in Texas during the summer months. Community is the point. Today, I invite you to embrace discomfort on the road to a more vulnerable you.
Stay safe, Matt Johansen
@mattjay
