- Vulnerable U
- Posts
- 🎓️ Vulnerable U | #139
🎓️ Vulnerable U | #139
Exploit dev boss selling secrets to Russia, YouTube malware network takedown, Dissection of massive sms phishing operation, and much more!
Read Time: 9 minutes

Brought to you by:
Howdy friends!
Got to do a quick trip to DC this week to speak to Fannie Mae for Cybersecurity Awareness Month. Was fun to meet some of their team and get out of the echo chamber a bit. Always wild to see people’s faces when I pull the curtain back on some of the stuff North Korea or Scattered Spider are up to in detail.
Thanks to their CISO and my buddy Chris Porter for having me come out.
ICYMI
🖊️ Something I wrote: F5 breach - everything we know so far
🎧️ Something I heard: DHH and Prime talking about Omarchy
🎤 Something I said: court blocks you from knowing your data was leaked
🔖 Something I read: Summary of the Amazon DynamoDB Service Disruption in Northern Virginia (US-EAST-1) Region
Vulnerable News
The feds just charged Peter "Doogie" Williams, former boss at L3Harris's Trenchant division, the folks who build fancy hacking tools for Five Eyes governments (US, UK, Canada, Australia, and New Zealand). Williams allegedly made off with eight trade secrets and sold them to Russia for a cool $1.3 million between 2022 and this past August. Trenchant develops zero-days and surveillance tools for Western intelligence agencies, so this is basically the hacker of selling nuclear launch codes.
What's wild is that Trenchant was already investigating a separate leak of their Chrome exploits earlier this year and initially blamed the wrong employee - some iOS exploit developer who couldn't have even accessed the Chrome tools due to compartmentalization. Meanwhile, Williams was sitting there as general manager with broader access, allegedly running his own little side business with the Russians. (read more)
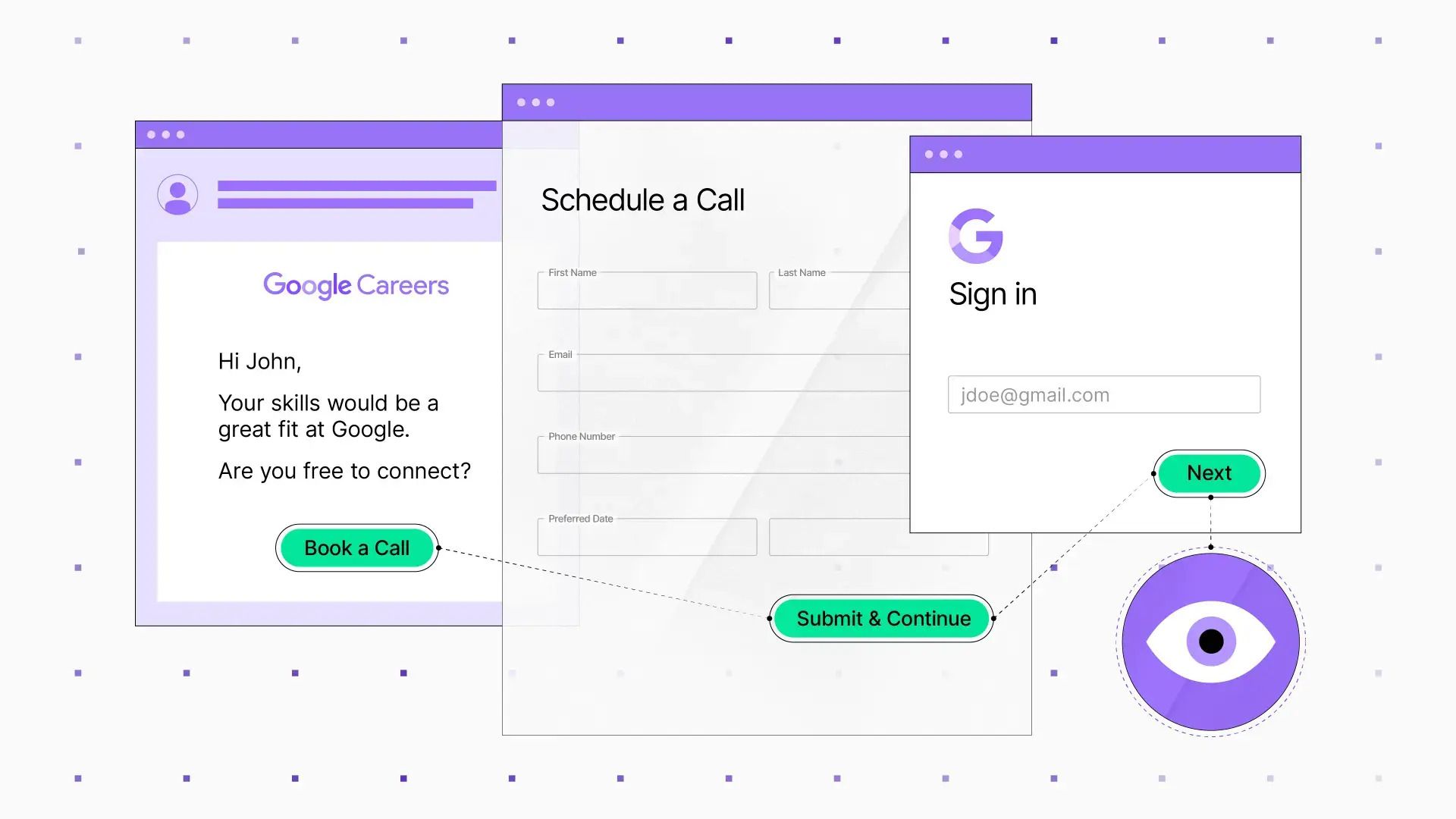
Scammers love going after people when they’re vulnerable, and job hunting is a sweet spot. A recent campaign even used a fake Google Careers site to trick people. The best defense is knowing the signs and using a security tool like Sublime that blocks these emails before they hit your inbox. You can’t fall for a scam you never see.
*Sponsored
Recorded Future just dropped a massive report on how Russia's cybercriminal ecosystem adapted after Operation Endgame. Turns out the whole "Russia as a blanket safe haven" narrative is getting more complicated. Moscow's been selectively burning certain players - they went hard after cash-out services like Cryptex and UAPS with mass arrests and asset seizures, but kept protecting the heavy hitters like Conti and Trickbot who have alleged intelligence ties. The report calls this "Dark Covenant 3.0" - basically a managed market where your protection depends on how useful you are to the state, not just geography.
The underground is fracturing under this pressure. Forums are seeing more scam complaints, ransomware groups are requiring deposits and going semi-private, and OPSEC discussions are all about moving to decentralized platforms. Meanwhile, ransom payments dropped significantly in 2024-2025 as Western governments implemented disclosure rules and payment restrictions.
All this pressure is making the ecosystem more centralized around state-protected core groups while burning the peripheral services. Russia's not abandoning cybercrime - they're just getting pickier about who they protect. (read more)
Google's threat intel team wrote up a bunch of awesome details on a Vietnamese crew (UNC6229) that's been running a big social engineering operation. They're posting fake job listings on legit platforms like LinkedIn, targeting digital advertising and marketing folks. The beauty of their scheme is that victims initiate contact by applying for the fake jobs, which immediately builds trust. Once someone bites, the attackers follow up with either malware disguised as "skills tests" or phishing links for fake interview scheduling.
They're going after people who have access to high-value corporate advertising accounts, which they can then hijack and monetize. The attackers are also abusing legitimate CRM platforms like Salesforce to send their initial contact emails, making them more likely to bypass security filters. Their phishing kits are cool too, handling various MFA schemes including Okta and Microsoft. Google's already blocking the domains and files they found, but expect this tactic to spread beyond just the advertising industry. (read more)

Check Point with a big report of findings on what they're calling the "YouTube Ghost Network" - a coordinated malware distribution operation that's been using over 3,000 malicious videos to spread infostealers. The network's been running since at least 2021, but things got spicy in 2025 when activity tripled. They're targeting people looking for game cheats (especially Roblox stuff) and cracked software like Adobe Photoshop. The most successful video hit 293k views promising free Photoshop, which is pretty impressive reach for cybercriminals.
They've got compromised YouTube accounts playing different roles. Some upload the malicious videos, others post community updates with download links and passwords, and others just spam positive fake comments to build trust. After Lumma Stealer got disrupted earlier this year, they pivoted to Rhadamanthys as their infostealer of choice. The whole setup is pretty clever - they're using legitimate platforms like Dropbox and Google Sites to host their payloads, and the fake engagement makes everything look legit to potential victims. (read more)
Shadow IT, supply chains, and cloud sprawl are expanding attack surfaces - and AI is helping attackers exploit weaknesses faster. Built on insights from 3,000+ organizations, Intruder’s 2025 Exposure Management Index reveals how defenders are adapting.
High-severity vulns are up nearly 20% since 2024.
Small teams fix faster than larger ones - but the gap’s closing.
Software companies lead, fixing criticals in just 13 days.
Get the full analysis and see where defenders stand in 2025.
*Sponsored
North Korean Lazarus hackers are pointing their Operation DreamJob playbook at European defense companies. ESET caught them targeting three firms in late March - a metal engineering company in Southeastern Europe and two Central European firms making aircraft parts and defense tech. What's interesting is these companies are all involved in UAV technology and their gear is currently being used in Ukraine, which lines up nicely with North Korea's recent push to build up their drone capabilities.
The attack chain is classic Lazarus - they're using fake job recruiters to get targets to download trojanized legitimate software like MuPDF viewer, Notepad++, and WinMerge plugins. Once they get a foothold through DLL sideloading, they deploy their ScoringMathTea RAT which gives them the usual remote access toolkit. Despite years of security researchers documenting these DreamJob tactics, it's still working for them. The fact that they're specifically hunting drone tech companies while their government is ramping up UAV development isn't exactly subtle, but hey, if it works, it works. (read more)
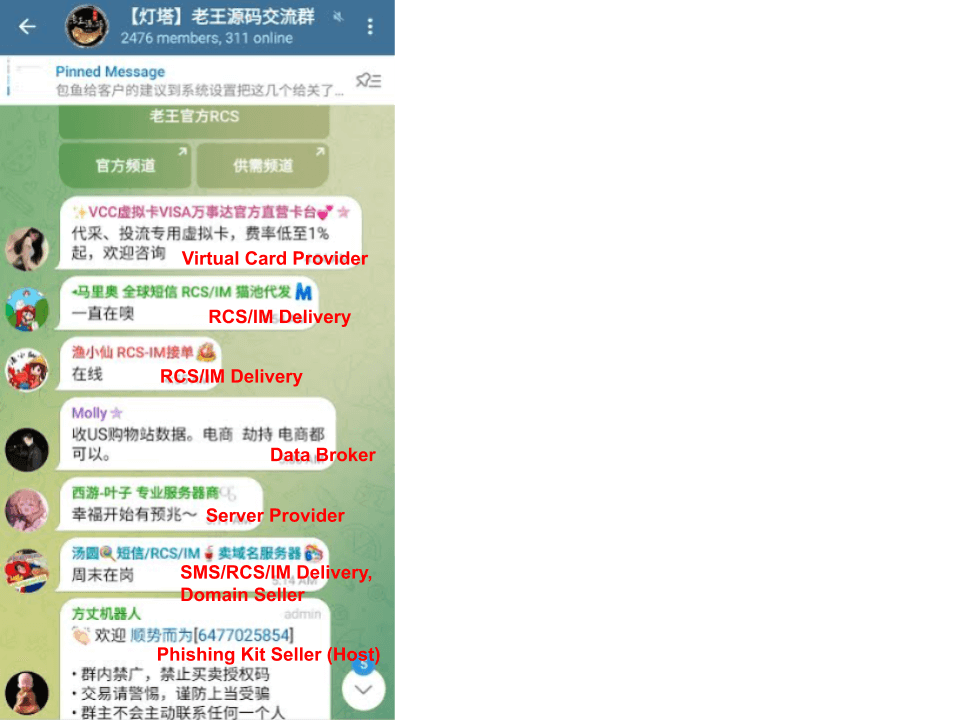
Palo Alto's Unit 42 just dropped some impressive research on what they're calling the "Smishing Triad" - a China-based crew that's been absolutely flooding the world with fake text messages. ~194,000 malicious domains since January, impersonating everything from toll services and package delivery to banks, government agencies, and cryptocurrency exchanges. The scale is bonkers - they're registering thousands of new domains daily and burning through them quickly to stay ahead of blocklists.
It's basically a full phishing-as-a-service operation with different specialists handling domain registration, hosting, SMS delivery, and even "liveness scanning" to check if phone numbers are valid. The domains get registered through Hong Kong but hosted primarily on US cloud services, and they're going way beyond the usual USPS fake delivery notices. They're now impersonating services globally - from German banks to UAE police forces to Russian e-commerce sites. The whole thing runs through a Telegram channel where different threat actors compete to offer services. It’s always fun to read these looks behind the curtains on an actual huge operation that is enabling what a lot of people think is just spam texts. (read more)
Remember Dan Kaminsky's 2008 DNS cache poisoning bombshell that had the entire internet scrambling? No? I’m old? Well, we're getting a throwback with new vulnerabilities in BIND and Unbound DNS resolvers. The BIND bugs (CVE-2025-40778 and CVE-2025-40780) can let attackers poison DNS caches again, with one actually weakening the defenses put in place after Kaminsky's disclosure. The culprit is a weak pseudo-random number generator that makes it possible to predict source ports and query IDs - basically undoing part of the entropy fix that saved us back then.
Before you panic though, this isn't quite 2008 all over again. If it was, buy bitcoin. The attack requires network-level spoofing, precise timing, and only affects cache integrity rather than full server compromise. Plus, we've got additional defenses now like DNSSEC, rate limiting, and better firewalling that weren't as widespread back in the day. Still, patches dropped Wednesday and you'll want to get them installed. (read more)
Palo Alto's Unit 42 dropped a deep dive on "Jingle Thief," a Morocco-based crew that's been running gift card fraud since 2021. These guys are patient - they'll sit inside your Microsoft 365 environment for over a year, compromising 60+ accounts while learning your systems inside and out. This is a great post and goes through their playbook: phish credentials, dig through SharePoint for gift card workflows, set up email forwarding rules, and eventually register rogue devices for persistence.
What makes them dangerous isn't just the longevity - it's that they operate entirely within cloud environments using legitimate Microsoft features. No malware needed when you can just abuse SharePoint, OneDrive, and Entra ID. They time their operations around holidays when staffing is low and gift card usage spikes. They access those gift card issuance systems and pump out high-value cards for resale on gray markets. (read more)
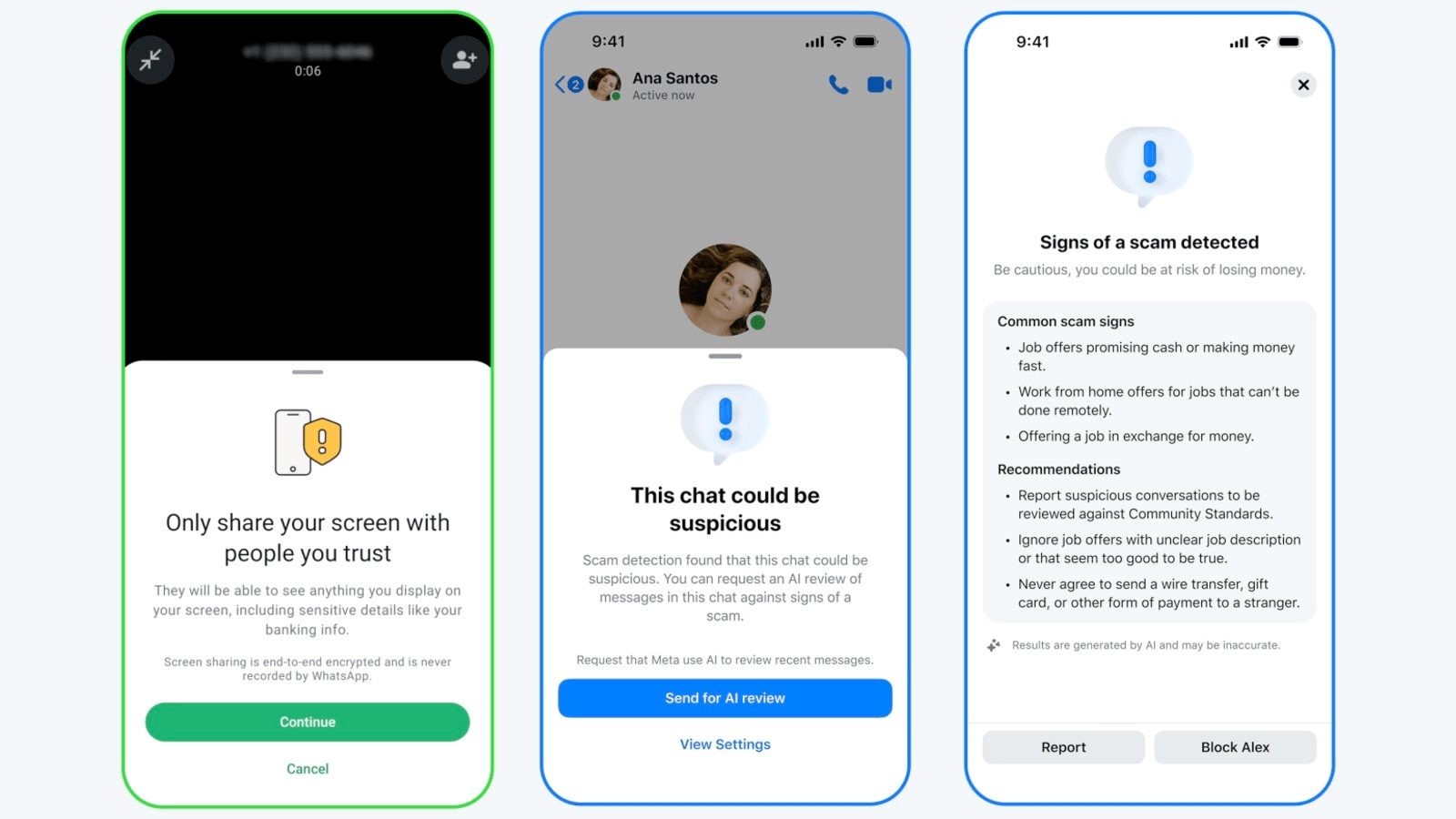
Meta's rolling out some new anti-scam features for WhatsApp and Messenger that actually sound pretty useful. The Messenger side is getting AI-powered scam detection that'll flag suspicious messages from new contacts and let you submit recent chats for review. Meanwhile, WhatsApp users will now get warnings when they're about to share their screen during video calls with unknown contacts - apparently scammers have been using this trick to get people to show their bank details or verification codes.
They've nuked nearly 8 million scam accounts just this year, mostly tied to operations in Southeast Asia and the UAE. Plus they took down over 21,000 fake customer support pages trying to phish people. It's good to see them being proactive rather than just playing whack-a-mole after people get burned. The features are opt-out by default, so most users should get the protection without having to think about it. (read more)
Billion. With a B?! The recent cyberattack on Jaguar Land Rover (JLR) shows how devastating a single breach can be. The attack, which paralyzed JLR's global manufacturing for over a month, has racked up an estimated £1.9B ($2.5B) in damages across the UK economy - making it the country's costliest cyber incident ever. The impact rippled through over 5,000 organizations, from direct suppliers to dealerships, threatening thousands of jobs and forcing the British government to step in with emergency support.
This wasn't your typical ransomware-spreads-through-shared-infrastructure scenario. Instead, it demonstrates how targeting just one major manufacturer can create a "cyber shockwave" (as one UK politician put it) through the entire supply chain. JLR, which accounts for 4% of British exports, is now trying to help its suppliers stay afloat with upfront cash payments while slowly restarting operations. (read more)
Senate lawmakers are finally doing something about those bullshit robocalls that plague us all. The Foreign Robocall Elimination Act just cleared a key committee, creating a new task force at the FCC to study and combat overseas robocalling operations. The bipartisan bill would give policymakers some actual data on how many of these calls come from abroad and which countries are hosting these scam operations.
They're also taking a hard look at STIR/SHAKEN, the call authentication system that was supposed to stop spoofing but clearly isn't working great. Remember those fake Biden robocalls in New Hampshire? Yeah, those sailed right through with the highest confidence rating. The bill also includes some teeth - telecom companies would need to put up a $100,000 bond before transmitting calls in the US, and companies can't just re-register for free after getting booted from the robocall database. About time someone made this more expensive for the bad guys. (read more)
CISA just confirmed that Oracle E-Business Suite CVE-2025-61884 is getting hammered in the wild, adding it to their Known Exploited Vulnerabilities list. Federal agencies have until November 10 to patch this SSRF flaw that lets attackers grab "critical data or complete access" without authentication. The whole thing traces back to Cl0p's summer rampage against Oracle EBS instances, though there's been some amusing confusion about which exploit does what.
Here's where it gets messy - there were actually two separate attack campaigns using different exploits, but Oracle somehow mixed up their IOCs when ShinyHunters leaked one of them on Telegram. The July attacks used the UiServlet SSRF (now CVE-2025-61884), while August used a different SyncServlet exploit (CVE-2025-61882). Despite multiple attempts to get Oracle to clarify which exploit belongs to which CVE, Oracle's playing the silent game… (read more)
Researchers found 94+ known CVEs in Cursor and Windsurf, two of the biggest AI-powered IDEs with 1.8 million users combined. Both editors are built on outdated VS Code versions that bundle ancient Chromium builds. The team successfully weaponized CVE-2025-7656 (already patched in current Chromium) to crash the IDEs via a deeplink attack that tricks victims into visiting a malicious site through the built-in Simple Browser.
This isn't just crashing an editor. Developer machines are absolute gold mines for supply chain attacks, packed with production access, API keys, source code, and credentials. When researchers reached out about their findings, Windsurf went radio silent while Cursor brushed it off as "self-DOS" - completely missing that the underlying memory corruption could enable code execution. With 93 other unpatched CVEs sitting there like a buffet for threat actors, this feels like a ticking time bomb for the entire software supply chain. (read more)
Miscellaneous mattjay
Security is being a fitness coach for participants of the hotdog eating olympics. And they are SNORTING these hotdogs at Mach 8.
— solst/ICE of Astarte (@IceSolst)
3:10 PM • Oct 22, 2025
everybody apologizing for cheating with chatgpt… we are SO cooked
— ria 🦦 (@lapislazuria)
11:18 PM • Oct 21, 2025
Please not another browser
— Fabrizio Rinaldi (@linuz90)
12:14 PM • Oct 23, 2025
How'd I do this edition?It's hard doing this in a vacuum. Screaming into a void. Feedback is incredibly valuable to make sure I'm making a newsletter you love getting every week. |
Parting Thoughts:
Community was foundational in launching and propelling my career. Community is the only reason I can stand being in Texas during the summer months. Community is the point. Today, I invite you to embrace discomfort on the road to a more vulnerable you.
Stay safe, Matt Johansen
@mattjay