- Vulnerable U
- Posts
- 🎓️ Vulnerable U | #143
🎓️ Vulnerable U | #143
FCC rolls back security requirements on telecom industry, Cloudflare postmortem, Salesforce with a new supply chain hack, and much more!
Read Time: 9 minutes

Brought to you by:
Howdy friends!
I feel like a lot of people are going through it this fall. If not maybe ask around. We just bought a friend their week’s groceries because they were kicked off food stamps but generally don’t love people knowing where they are at. I’m not saying this to flex, but to encourage you really understanding where people in your community are at. Some are struggling in silence!
ICYMI
🖊️ Something I wrote: I don’t understand why the Congressional budget office hack isn’t bigger news
🎧️ Something I heard: why everyone is mad at google (this time)
🎤 Something I said: Slept on the whole Anthropic threat intel report and …I have feelings
🔖 Something I read: I Almost Lost My Apple Account to the Most Sophisticated Phishing Attack I’ve Ever Seen
Vulnerable News
The FCC just voted 2-1 to scrap cybersecurity requirements for telecom companies, with Chairman Brendan Carr leading the charge to reverse Biden-era rules. This comes right after China's Salt Typhoon campaign absolutely wrecked poorly secured telecom networks and gave Beijing access to tons of sensitive data. A giant wtf.
The telecom industry successfully lobbied against the rules, claiming they were too burdensome and that voluntary cooperation works better. Democrats are predictably furious, with Commissioner Anna Gomez pointing out that "if voluntary cooperation were enough, we would not be sitting here today in the wake of Salt Typhoon." Carr insists the industry has stepped up their game since getting pwned, but trusting companies to self-regulate their security after they've already been breached feels like a bold strategy. Let's see how that works out for them. (read more)
Your security team is one-of-a-kind. Your AI SOC should be too.
On December 3rd, see how Reddit, one of the internet’s largest platforms, is using AI to boost SOC efficiency.
Join Nick Fohs, Senior Manager of Enterprise Systems & Security at Reddit, for:
Insight into how Reddit’s security team approaches AI
Top AI use cases you can get started with
A live walkthrough of how to get started building your own AI SOC
*Sponsored
(What a funny sponsored post for me to run, Nick is my old, brilliant, colleague! I was a very happy Tines customer when I worked at Reddit and it seems they continue to be after I’ve left)
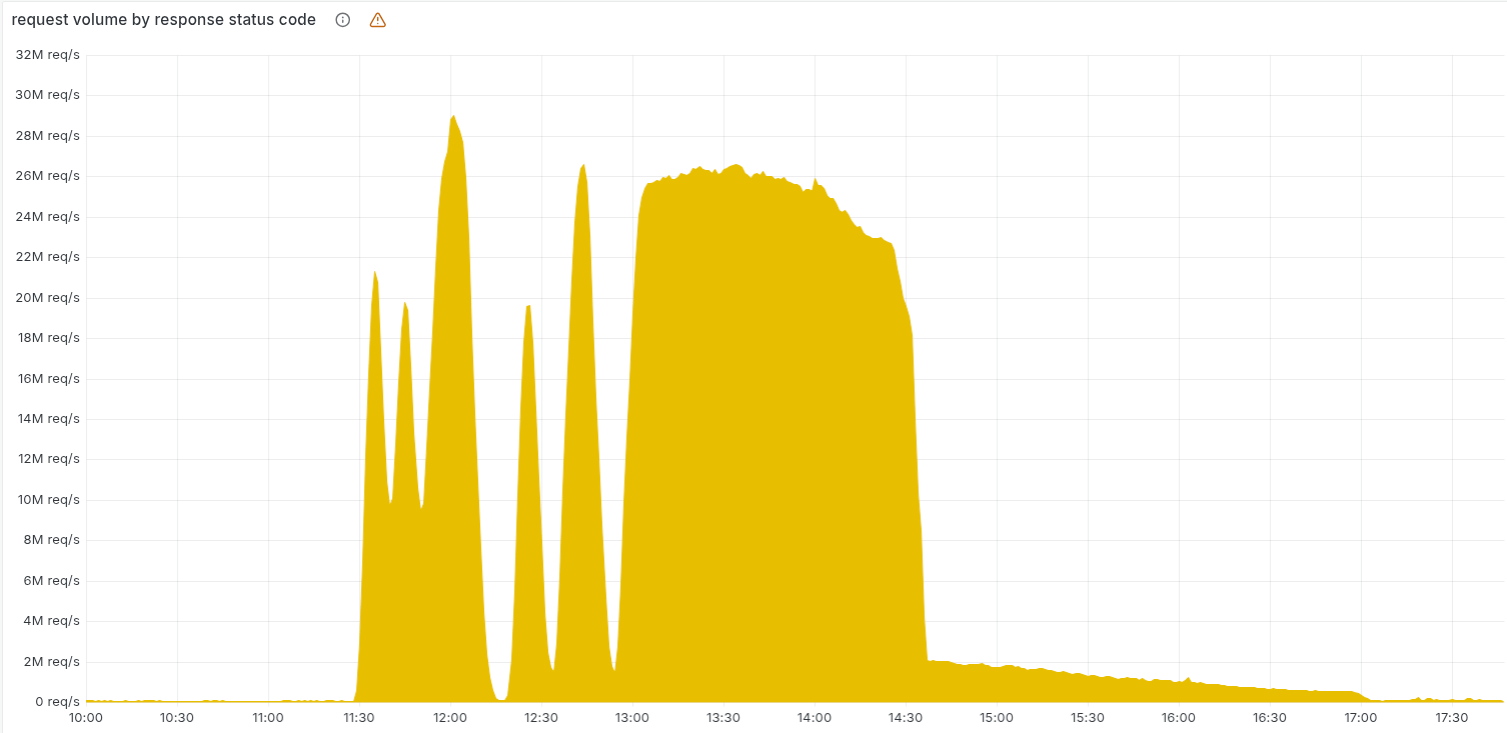
Cloudflare had a rough Monday, taking down a chunk of the internet for about 6 hours due to what they're calling their worst outage since 2019. The culprit was a seemingly innocent database permissions change that caused their Bot Management feature file to balloon with duplicate entries. Their proxy software had a hard limit of 200 features, but the corrupted file exceeded this, causing the whole system to panic and spew 5xx errors across their network.
What made this particularly confusing for their team was that the bad file was only generated every 5 minutes when queries hit the updated parts of their ClickHouse cluster, so the outage would fluctuate - sometimes working, sometimes not. This led them down the wrong path initially, thinking they were under a massive DDoS attack (especially when their status page coincidentally went down too). The fix was to stop the bad file generation and roll back to the last known good version.
Really a commendable way to handle this btw. Extremely detailed postmortem came out incredibly soon after the incident - they even shared f’n source code that caused the outage. Kudos. (read more)

Salesforce is dealing with another supply chain incident after hackers breached customer data through Gainsight, a third-party customer management platform. ShinyHunters is claiming responsibility and threatening to leak data from nearly a thousand companies unless Salesforce plays ball with their extortion demands. Salesforce is doing the classic "not our fault, it's the third-party integration" dance, saying the breach came through Gainsight's external connection rather than their own platform.
This whole mess feels super freaking familiar. We just did this in August for the Salesloft breach, where the same hacking crew used a similar playbook to compromise Salesforce customers through a connected app. That attack hit some big names like Cloudflare, Google, and Qantas. Now they're back with a new target and the same MO - compromise the third-party service, pivot to the connected Salesforce instances, then set up a leak site to pressure victims. (read more)
Amazon's playing more in the threat intelligence game and we just got some sobering research on what they're calling "cyber-enabled kinetic targeting" - basically nation-state actors using hacking to set up physical attacks. Imperial Kitten (Iran's IRGC crew) spent months compromising a ship's Automatic Identification System (AIS) systems and ship cameras, then in early 2024 they specifically tracked one vessel right before Houthi forces launched missiles at it.
Another case is even more direct - MuddyWater accessed Jerusalem CCTV feeds in June 2025, and on the same day Iran launched widespread missile attacks, Israeli officials warned citizens to disconnect internet cameras because Iran was using them for real-time targeting adjustments. (read more)
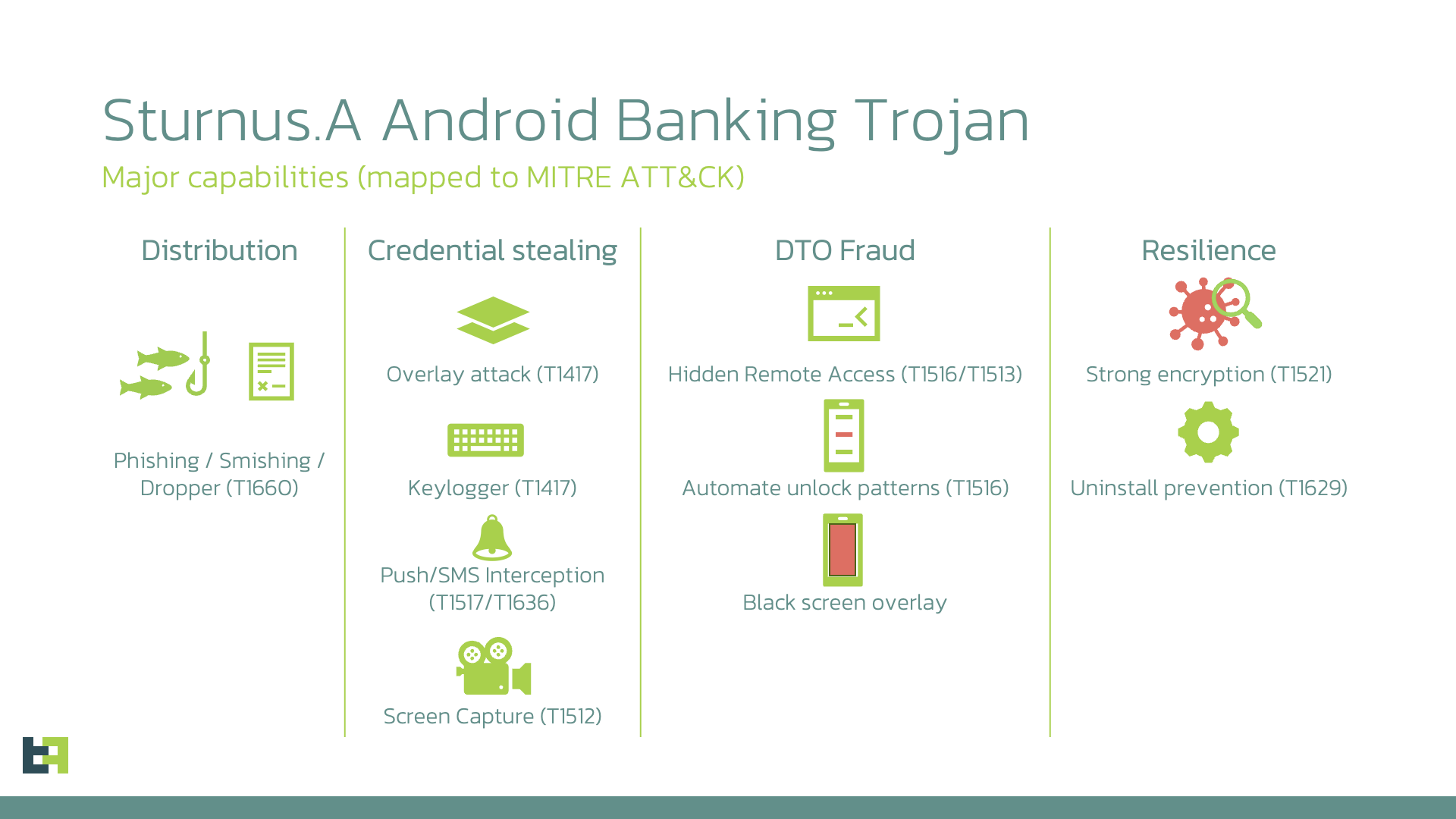
Meet Sturnus, a new Android banking trojan that's figured out how to sidestep all that fancy end-to-end encryption we love bragging about. Instead of trying to crack WhatsApp, Telegram, or Signal's crypto, it just waits for messages to be decrypted on your screen then captures everything through Android's Accessibility Services. I always say end-to-end still means if one of the “ends” is compromised, you’re toast.
The malware's currently in what looks like a testing phase, targeting users in Southern and Central Europe with the usual banking overlay tricks plus full remote control capabilities. The researchers at ThreatFabric found it masquerading as "Google Chrome" and "Preemix Box" apps. (read more)
Deepfake attacks are exploding and most companies still don’t have a real plan for GenAI threats. It’s not about whether someone will try to break in, it’s about whether you’re actually ready when they do.
A lot of orgs still rely on the usual stack like MFA and VPNs, but none of that matters if an attacker can convincingly pose as an employee. That’s the gap getting hit over and over. If you want what actually works, this new ebook breaks down how to secure the workforce by verifying the person at the keyboard instead of just their credentials.
Download it now to get the full rundown.
*Sponsored
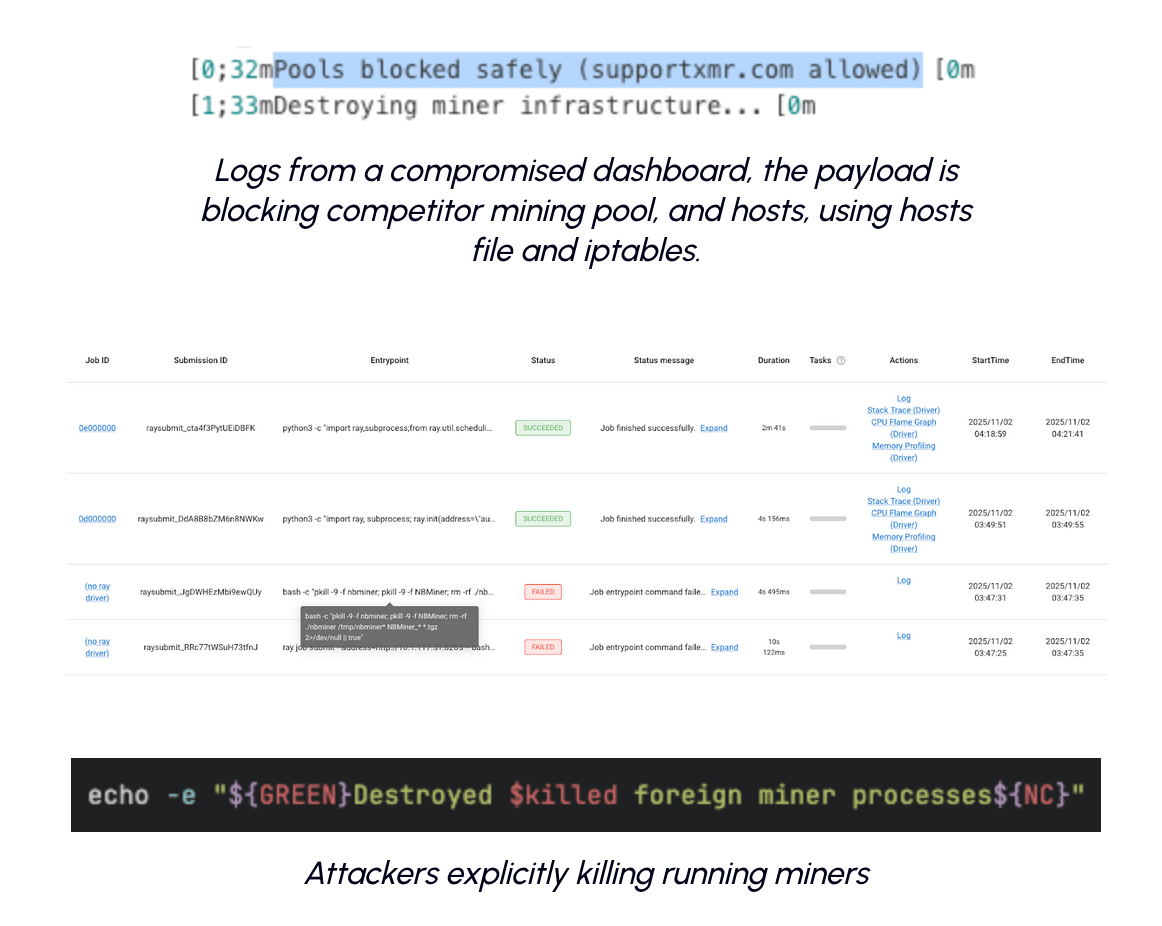
Turf wars
A cryptomining botnet is having a field day with Ray's AI framework, exploiting a 2-year-old authentication flaw (CVE-2023-48022) that Ray left unpatched. Dubbed ShadowRay 2.0, these attacks are turning exposed NVIDIA GPU clusters into a self-spreading crypto mining network. They started on GitLab, got booted, then migrated to GitHub seamlessly. The operation has grown from targeting a few thousand exposed Ray servers to over 200,000 worldwide.
The attackers are building a multi-purpose botnet capable of DDoS attacks, data exfiltration, and autonomous propagation. They're literally having turf wars with other mining groups, killing rival processes and blocking competing mining pools. The campaign targets high-end GPU clusters (think $4M+ annual compute costs), limits CPU usage to 60% to stay under the radar, and uses geolocation detection to serve different payloads to Chinese victims. The fact that this vulnerability remains "disputed" because Ray maintainers insist it should only run in trusted environments is creating a perfect storm for continued exploitation. (read more)
I’ve talked about the TP-Link China stuff a few times over on YouTube. Now TP-Link is throwing down with rival Netgear, claiming they're running a "smear campaign" to paint them as a Chinese government puppet. The lawsuit gets spicy because TP-Link already paid Netgear $135 million in 2024 to settle patent disputes, and part of that deal supposedly included Netgear promising to stop trash-talking them. Apparently that didn't last long.
The beef centers around Netgear CEO Charles Prober's earnings calls, where he allegedly twisted Microsoft's Storm-0940 botnet report to make it sound like TP-Link was actively helping Chinese hackers. TP-Link's crying foul, saying the Microsoft report never actually blamed them directly - their routers just got hijacked like any other vulnerable device. The corporate structure is messy though - TP-Link's predecessor was founded in China, and while they claim to be a legit California company now, those government investigations into their China ties probably aren't helping their case. (read more)
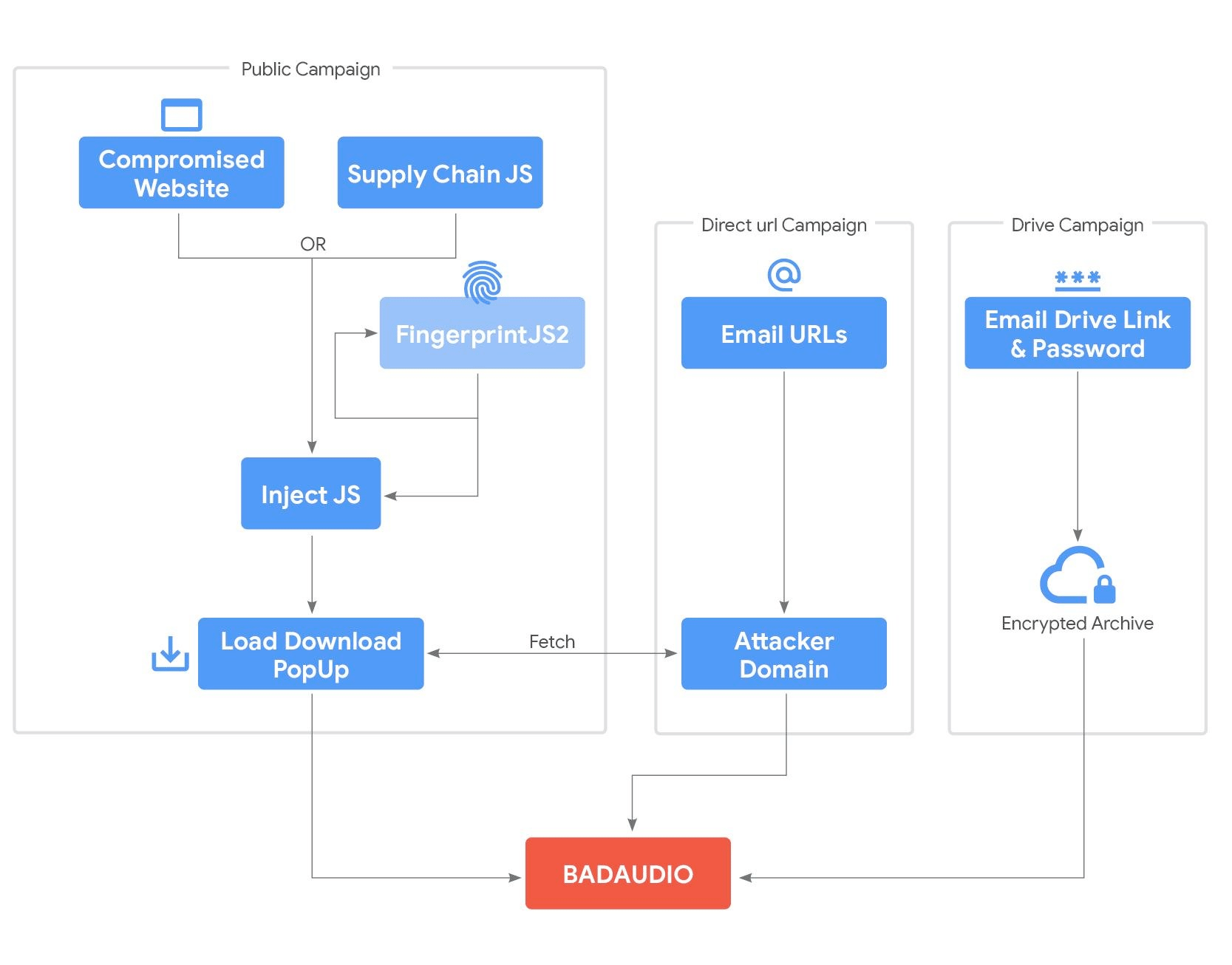
Google's threat intel folks have been tracking APT24 (China), which has been busy for the past three years with their BADAUDIO malware campaign. This thing is nasty - it's a heavily obfuscated first-stage downloader that makes reverse engineering a pain in the ass. The malware phones home with system info buried in cookie headers and eventually drops Cobalt Strike Beacon payloads.
They started with broad strategic web compromises hitting 20+ sites, but then they got smart and pivoted to supply chain attacks. They repeatedly compromised a Taiwanese digital marketing firm and used it to inject malicious JavaScript into over 1,000 domains. The attackers are using browser fingerprinting to selectively target victims and fake Chrome update pop-ups to trick people into downloading their malware. They've also been running targeted phishing campaigns using legitimate cloud storage like Google Drive and OneDrive. Good intel report. (read more)
The gang's all here for some fresh sanctions against Russian bulletproof hosting providers. The US, UK, and Australia just went after Media Land and its sister company ML Cloud, along with their leadership team. These outfits have been the backbone for some ransomware groups like Lockbit, BlackSuit, and Play, plus they've been hosting DDoS infrastructure targeting US critical infrastructure.
They also nailed Hypercore Ltd, which turns out was just a front company for the previously sanctioned Aeza Group. Shell game stuff - when one company gets sanctioned, just spin up another one in a different country and keep the party going. The Five Eyes countries and Netherlands also dropped a joint advisory on how to deal with these bulletproof hosting services, basically telling ISPs and defenders to get smarter about filtering malicious infrastructure. (read more)
Fortinet's having a rough week. They just admitted to another 0-day in FortiWeb (CVE-2025-58034) - an authenticated command injection bug that's being actively exploited. This comes just days after they released the first one (CVE-2025-64446), which was a path traversal flaw that bypasses authentication entirely. Trend Micro's already seeing around 2,000 detections of the new bug in the wild.
Here's where it gets spicy: security researchers are pretty convinced these two vulnerabilities are meant to be chained together. Use the first bug to bypass authentication, then leverage the second for command injection - boom, you've got unauthenticated remote code execution. Even CISA's spun up, giving federal agencies just 7 days to patch instead of the usual 15-30 day timeline. Fortinet's pattern of quietly patching vulnerabilities and only disclosing them after getting caught isn't doing them any favors in the trust department either. (read more)
The homies at GreyNoise spotted a massive spike in scanning activity hitting Palo Alto GlobalProtect portals - a 40x surge in just 24 hours starting November 14th. They logged 2.3 million sessions targeting the /global-protect/login.esp endpoint, with the bulk of traffic coming from AS200373 (3xK Tech GmbH) split between German and Canadian geolocations. The attackers are showing some consistency with their JA4t fingerprints and seem to be hitting targets in the US, Mexico, and Pakistan pretty evenly.
GreyNoise's noticed that spikes in Fortinet VPN attacks often precede vulnerability disclosures within six weeks. Makes you wonder if we're seeing early reconnaissance for something bigger. If you're running Palo Alto gear, might be worth keeping an eye on those two JA4t signatures they called out. If you're running GlobalProtect portals, might want to keep an extra eye on your logs and make sure you're patched up - this feels like the calm before another CVE storm. (read more)
A massive router hijacking campaign dubbed "Operation WrtHug" has compromised around 50,000 ASUS routers globally. This China-linked campaign has been quietly turning ASUS home routers into a global spy network, compromising over 50,000 devices in the last six months alone. The attackers are hitting End-of-Life routers with a cocktail of known vulnerabilities, primarily targeting the AiCloud service. They're using a shared self-signed TLS certificate with a ridiculous 100-year expiration as their calling card, making it easier for researchers to track but harder for victims to spot.
The geographical spread tells a story - 30-50% of compromised devices are in Taiwan, with clusters across the US, Russia, and Southeast Asia. This looks like another Operational Relay Box campaign where state-sponsored actors build massive networks of infected devices for persistent espionage. This campaign appears connected to another operation called "AyySSHush" that hits the same vulnerabilities on the same device types. ASUS has patched the vulnerabilities and released advisories, but if you're running old ASUS gear, might be time to check if you're part of someone else's spy network. (read more)
Microsoft just got absolutely hammered by what they're calling the largest DDoS attack ever seen against Azure - 15.72 Tbps and nearly 3.64 billion packets per second hitting a single endpoint in Australia back in October. Before you get too impressed though, it's not the global record holder (that's still Cloudflare's 22.2 Tbps monster from earlier). Both attacks were powered by the same culprit: the Aisuru botnet, which is basically a TurboMirai-class operation running off half a million compromised routers, cameras, and DVRs.
Aisuru operates as a DDoS-for-hire service and has been particularly fond of targeting gaming platforms, though they also dabble in credential stuffing and phishing. The fact that these TurboMirai botnets can't generate spoofed traffic is actually helping defenders identify and clean up infected devices, which is a rare silver lining in the botnet world. (read more)
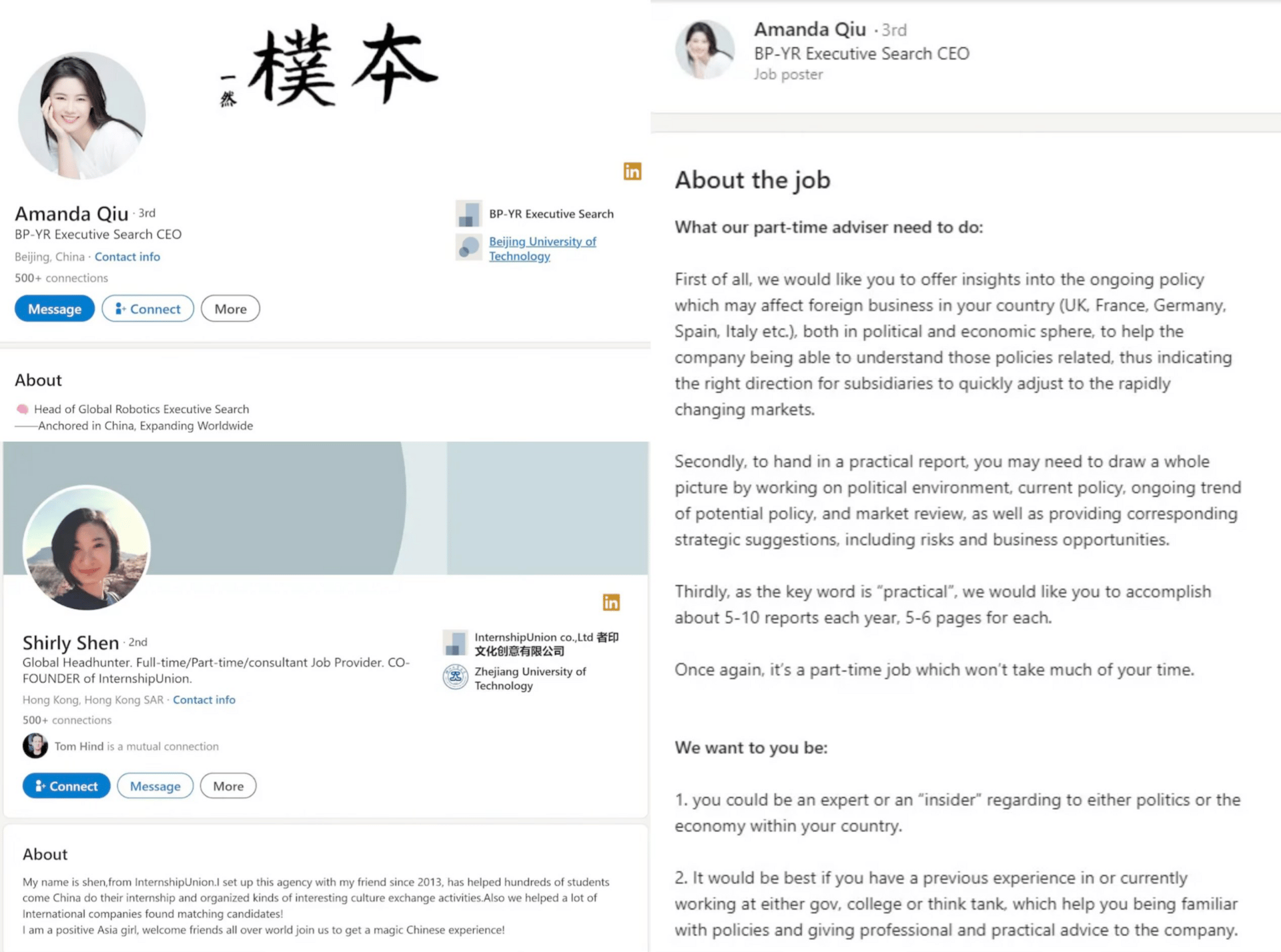
MI5 just put out a spy alert to Parliament about Chinese intelligence officers sliding into DMs on LinkedIn, basically catfishing MPs and government staff to recruit them. The UK's calling out two specific profiles that were fronting as legit headhunters but were actually working for Chinese intelligence. Security Minister Dan Jarvis is rolling out a whole Counter Political Interference and Espionage Action Plan - think security briefings for political parties, making LinkedIn a more hostile environment for spies, and tightening up political donation rules.
They're also throwing some serious cash at the problem - £170 million for new encrypted tech for civil servants and another £130 million for counter-terrorism and cyber security capabilities. (read more)
Miscellaneous mattjay
How'd I do this edition?It's hard doing this in a vacuum. Screaming into a void. Feedback is incredibly valuable to make sure I'm making a newsletter you love getting every week. |
Parting Thoughts:
Community was foundational in launching and propelling my career. Community is the only reason I can stand being in Texas during the summer months. Community is the point. Today, I invite you to embrace discomfort on the road to a more vulnerable you.
Stay safe, Matt Johansen
@mattjay
