- Vulnerable U
- Posts
- 🎓️ Vulnerable U | #147
🎓️ Vulnerable U | #147
Children cancer patients scammed of donations, Mixpanel breach impacting more victims, Browser extensions spying on your AI chats, and much more!
Read Time: 8 minutes

Brought to you by:
Howdy friends!
Happy holiday season everyone. It’s been such a busy Q4, my family had to make sure to get a lot of the holiday fun stuff on the calendar before December evaporated. I’m glad we did! Got to do a lot of the fun things Austin has to offer this time of year, which were all great, and I feel fortunate to live in a city full of awesome people.
If you haven’t already, I encourage you to do the same and make sure you put the proverbial pen down for a bit and get out into your city/town and be a part of the community.
It’s easy for us to hole up and play the busy card in this industry. When I was doing incident response, I don’t think a single U.S. holiday went by without an incident bridge firing up, so for this year I’m thankful to not be manning the wall. - To all of you out there who are, I’ve been there and major good vibes your way. But please take some time to do whatever it is that helps you feel connected to your family and community this time of year.
I don’t like overplaying the “recharge and come in strong for the New Year!” stuff - because that honestly isn’t the goal. Not trying to just exist out here for the rare week off just to get back to it. - I hope we can all take a little time to be more present with those around us.
Connecting with, and being a contributing part of, our communities around us is what it’s all about.
 |  |
ICYMI
🖊️ Something I wrote: This PornHub, OpenAI, Mixpanel hack is super weird.
🎧️ Something I heard: Dan Miessler and Clint Gibler’s webinar about some of the crazy AI tools Dan has been building
🎤 Something I said: I think this npm worm is the tip of the iceberg - this is going to get way worse
🔖 Something I read: Detection Engineering Weekly Field Manual - What are Atomic Detection Rules?
Vulnerable News
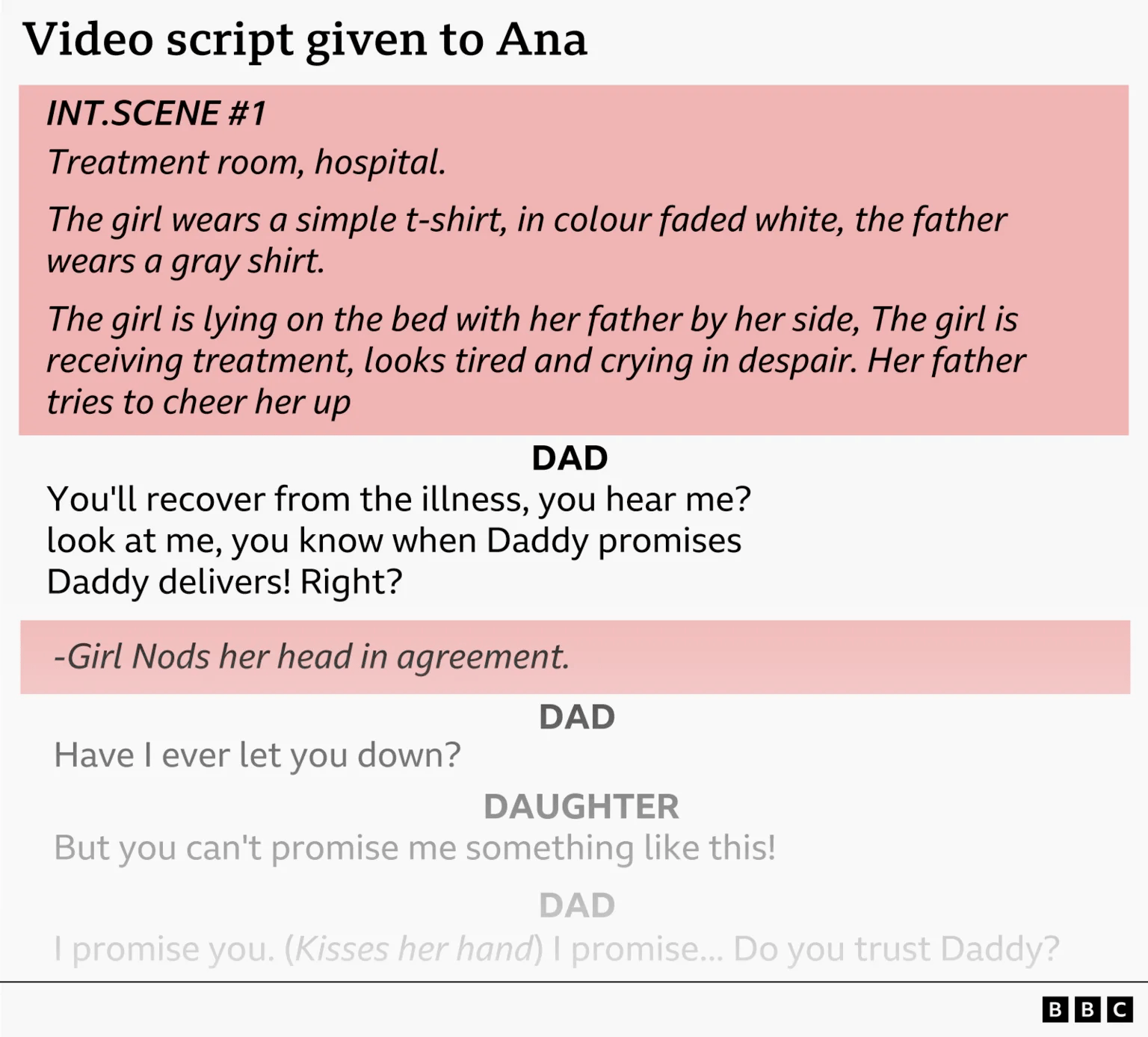
I could’ve picked some much more disturbing images to include. Fair warning.
This is absolutely vile. The BBC uncovered an international scam network exploiting families with children who have cancer, stealing millions in crowdfunded donations. The operation, led by Israeli-Canadian Erez Hadari, targets desperate parents and stages elaborate fake medical videos - complete with scripts, fake drips, and forced tears using chopped onions and menthol. They're looking for "beautiful children" aged 3-9 without hair to maximize sympathy donations.
The scale is way too big for what this is - 15 families identified across multiple countries, with campaigns appearing to raise over $4 million that never reached the families. Instead, parents got filming fees of a few hundred dollars while their children's suffering was monetized through YouTube ads and crowdfunding pages. What makes this particularly heinous is that many of these kids actually did have cancer and died while the scammers kept collecting donations in their names. (read more)
85% of CISOs say they’re not fully confident in their ability to handle GenAI-enabled fraud. This gap reflects a broader concern: legacy workforce security controls were not built for today’s identity threat landscape, especially as attackers use a mix of sophisticated tactics to scale social engineering, impersonation, and identity abuse. Persona’s workforce security ebook explores what this shift means for enterprise defenses and how leaders are preparing their teams. (read more)
*Sponsored
China putting out some interesting statements about U.S. cyber operations. Their Ministry of State Security revealed that the NSA has been running a three-year hacking campaign against China's National Time Service Center in Xian, which provides precision timing for their BeiDou satellite navigation system. Defense analysts are calling it a major clue about America's "left-of-launch" missile defense capabilities, basically the ability to mess with enemy missiles before they even fire. Get them to explode in silo before launch.
By potentially compromising China's timing infrastructure, the U.S. could theoretically plant malware that disrupts missile guidance, feeds false navigation data, or even causes missiles to blow up in their silos. Israel recently showed how effective this approach can be when they took out Iranian mobile missiles before they could fire during their retaliatory strikes. Taking ALL of this with a grain of salt, because you have to ask why any government is saying this kind of stuff publicly. (read more)
Mixpanel had a really bad month. The company got hit with a SMS phishing campaign back in November, and now the fallout is hitting some big names. PornHub sent out breach notifications this week after hackers used their Mixpanel access to grab some user analytics data. Includes watch and download history. OpenAI also got caught up in this mess, with some API user data getting scooped up in the same incident.
SoundCloud took a different approach and didn't name Mixpanel directly, but their breach has the same fingerprints. About 40 million users got their email addresses and public profile info exposed. When SoundCloud tried to lock down the attackers, they got hit with DDoS attacks that temporarily knocked the platform offline. ShinyHunters is allegedly behind these attacks, which would make sense given their track record of going after Salesforce customers earlier this year. Third-party analytics services are becoming quite the attack vector. (read more)
This is a very good writeup by AWS about some attacks they saw. It details a crypto mining campaign where the attackers were using compromised IAM credentials to spin up mining operations on both EC2 and ECS services, and they were fast - getting miners operational within 10 minutes of initial access. They disabled API termination on all launched instances, making it harder for victims to kill the resources and disrupting automated remediation.
The campaign used a malicious Docker image (yenik65958/secret) that's already been pulled over 100,000 times before getting yanked from Docker Hub. They created dozens of ECS clusters, auto scaling groups configured to scale up to 999 instances, and even set up Lambda functions with public endpoints for persistence. (read more)
The DOJ just took down another crypto laundering operation, this time targeting E-Note and its alleged Russian operator Mykhailo Petrovich Chudnovets. They're saying this platform moved over $70 million in dirty money since 2017, including ransomware payouts and funds stolen from healthcare and critical infrastructure victims. Prosecutors describe E-Note's evolution from a basic money mule operation in 2010 to a full-scale online platform by 2025.
The takedown was a coordinated effort with German and Finnish law enforcement, and they managed to seize servers, mobile apps, and websites including e-note.com and e-note.ws. Investigators got their hands on customer databases and transaction records from earlier server copies, which means this bust could lead to a whole lot more arrests down the road. Chudnovets is looking at up to 20 years if convicted, though the announcement doesn't mention whether he's actually in custody or still chilling in Russia. (read more)
React2Shell is turning into an absolute nightmare for defenders. This maximum-severity bug in React (CVE-2025-55182) has already hit over 60 organizations with Microsoft reporting "several hundred machines" compromised across diverse targets. VulnCheck confirmed nearly 200 valid exploits, giving it the highest verified public exploit count of any CVE ever. Everyone from ransomware gangs to Chinese espionage groups and Iranian threat actors all piling on within hours of the December 3rd disclosure.
The targeting is getting spicy too. Cloudflare spotted attacks hitting a national authority responsible for uranium and nuclear fuel imports, plus U.S. government sites and critical infrastructure. Some ransomware crews are moving so fast they're dropping payload within a minute of initial access. Exploitation timelines have shrunk from weeks to hours, and with additional related CVEs popping up during cleanup efforts, this one's going to have long legs. If you're running React components, hopefully this isn’t news to you. Get to running that incident. (read more)
France just busted a Latvian crew member for allegedly planting malware on an Italian passenger ferry that could have let someone remotely control the ship. The guy was working aboard GNV's Fantastic ferry when they discovered the remote access tool while docked at Sète. His Bulgarian colleague got released, but the Latvian is facing charges for conspiring to infiltrate computer systems on behalf of a foreign power.
The French Interior Minister is being coy about naming names, but when he says "these days one country is very often behind foreign interference," we all know who he's talking about. GNV says they neutralized the malware "without consequences," but the idea of someone potentially hijacking a passenger ferry remotely is pretty unsettling. This comes right after France's Interior Ministry also got breached, so they're dealing with multiple incidents that smell like coordinated foreign ops. At least they caught this one before anything bad happened to the ferry. (read more)
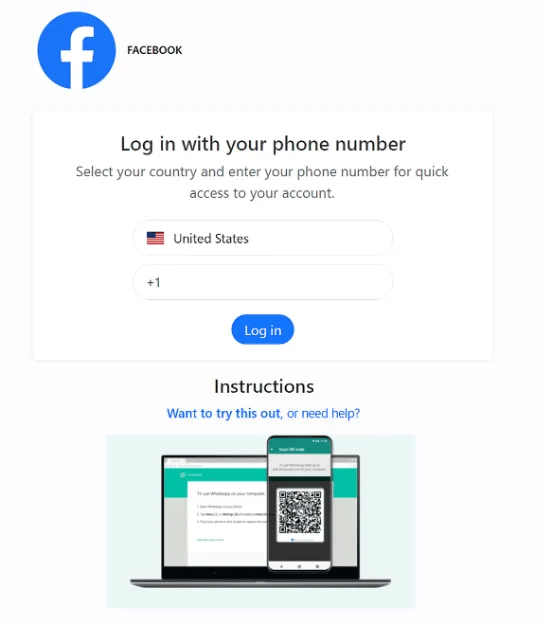
Fake Facebook page showed after clicking on the WhatsApp received link
Researchers at Gen have uncovered a WhatsApp takeover scam they're calling "GhostPairing." Victims get messages from their contacts saying something like "Hey, I just found your photo!" with a link that looks like Facebook. Click it, and you're taken to a fake Facebook page that asks you to "verify" by entering your phone number, then inputting a pairing code into WhatsApp. What you're actually doing is approving the attacker's browser as a linked device on your account - no password theft or SIM swapping required.
Once they're in, attackers have full access to read your messages, download your photos, and send that same lure to all your contacts to spread the attack. It started in Czech Republic but works anywhere since it abuses WhatsApp's legitimate device pairing feature. Your best defense is simple: regularly check Settings → Linked Devices and boot anything you don't recognize. (read more)
Cisco Talos report about Chinese APT group (UAT-9686) going after Cisco email security appliances with a custom toolkit they're calling the "Aqua" suite. The vulnerability lets attackers execute arbitrary commands with root privileges, and Cisco Talos discovered the attacks on December 10th after they'd been running since late November. The attackers are using a full toolkit including AquaShell backdoor, AquaPurge for log cleaning, and Chisel for tunneling into internal networks.
There's no patch available yet, just mitigations, which means this one's still wide open. CISA slapped it on the Known Exploited Vulnerabilities list with a Christmas Eve deadline for federal agencies. (read more)
Another day, another critical Fortinet vulnerability being hammered in the wild. We've got two CVEs here - CVE-2025-59718 and CVE-2025-59719 - that let attackers bypass authentication through crafted SAML messages and grab admin access. While FortiCloud SSO is disabled by default, it automatically turns on when you register your device to FortiCare through the GUI unless you explicitly opt out. So chances are, if you've got Fortinet gear registered for support, you're probably exposed.
Arctic Wolf spotted active exploitation, CISA tossed it on their KEV list, and Rapid7's seeing attacks against their honeypots. The attack pattern is pretty straightforward - bad actors auth as admin, immediately yank the system config file (which has those juicy hashed creds), and you're left assuming everything's compromised. Patches dropped on December 9th covering FortiOS, FortiProxy, FortiSwitchManager, and FortiWeb across multiple version branches. If patching isn't immediately feasible, you can disable FortiCloud SSO administrative login as a stopgap. (read more)
TikTok got caught tracking a user's Grindr activity along with his shopping habits across other apps. The Vienna-based digital rights group noyb filed complaints saying TikTok violated GDPR by processing sensitive data about the user's sexual orientation without explicit consent. When the guy kept asking TikTok what data they had on him (which is his legal right), they allegedly gave him the runaround with incomplete and confusing responses.
Noyb is the same group that got Meta slapped with a €1.2 billion fine and previously got TikTok dinged for €530 million over data transfers to China. The Israeli data broker AppsFlyer apparently helped facilitate this cross-app tracking mess. (read more)
GreyNoise caught a massive, coordinated credential stuffing campaign hitting enterprise VPN gateways over two days in mid-December. First was Palo Alto GlobalProtect, which got hammered with 1.7 million login attempts from over 10,000 unique IPs in just 16 hours. The next day, Cisco SSL VPN endpoints saw their daily attacking IPs jump from the usual sub-200 to 1,273 - a pretty clear sign someone was working their way through the VPN vendor playbook.
Nearly all the traffic came from 3xK GmbH hosting in Germany, using consistent tooling and even the same TCP fingerprints across both campaigns. This wasn't some distributed botnet - it was centralized, cloud-hosted infrastructure doing systematic credential spraying. The good news is it's not exploiting vulnerabilities, just trying weak passwords. The bad news is if you're running these VPN gateways without solid MFA and password hygiene, you're probably going to have a bad time. (read more)
Eight browser extensions with over 8 million combined users have been quietly harvesting every single AI conversation you've had since July. These aren't sketchy no-name extensions either - we're talking about popular VPN and ad-blocking tools like Urban VPN Proxy (6 million users) that Google and Microsoft have actually endorsed with "Featured" badges. The extensions inject custom scripts that override your browser's normal network functions, essentially man-in-the-middling every ChatGPT, Claude, and Gemini conversation you have.

The conversation harvesting runs completely independently from the extension's advertised features. So even when you turn off the VPN or ad blocker, it's still siphoning your prompts, responses, timestamps, and session data to Urban Cyber Security's servers. They're selling this goldmine of personal data - medical questions, financial details, business secrets - for "marketing analytics purposes." While their privacy policies technically mention this data collection, it's buried in 6,000 words of legal gibberish that nobody reads. (read more)
Texas AG Ken Paxton just dropped lawsuits on five major TV manufacturers - Sony, Samsung, LG, Hisense, and TCL - for secretly screenshotting what people watch every 500 milliseconds using Automated Content Recognition tech. Yeah, I read that twice too… - your smart TV has been taking screenshots of your screen twice per second and beaming that data back to corporate servers without telling you. The AG is particularly cranky about the Chinese companies since they're subject to China's National Security Law, which could theoretically give Beijing access to Americans' viewing habits.
This isn't exactly new territory - Vizio got slapped with a $2.2 million settlement back in 2017 for similar shenanigans, collecting viewing data from 11 million users and selling it to advertisers. The difference here is the scale and sophistication of the data collection. ACR technology can capture everything from Netflix binges to private video calls displayed on your TV. This is why security nerds like dumb devices: maybe don't connect that smart TV to your network in the first place. (read more)

Infoblox researchers found that over 90% of parked domains now redirect visitors to malicious content - a massive jump from just 5% back in 2014. Things like expired domains, typos of popular sites, and lookalike domains that used to show harmless parking pages but now push scams, malware, and worse. These redirects only happen if you're coming from a residential IP address. Hit the same domain through a VPN or business connection and you'll see a normal parking page.
They found one operation running nearly 3,000 typosquatting domains targeting everything from Gmail to government sites. Even gmai[.]com (missing the 'L') has its own mail server set up to catch misdirected emails for scam purposes. Google's recent policy changes might have made things worse by reducing legitimate ad revenue for parked domains, pushing owners toward shadier monetization schemes. Time to embrace bookmarks and maybe that password manager suggestion. (read more)
Miscellaneous mattjay

How'd I do this edition?It's hard doing this in a vacuum. Screaming into a void. Feedback is incredibly valuable to make sure I'm making a newsletter you love getting every week. |
Parting Thoughts:
Community was foundational in launching and propelling my career. Community is the only reason I can stand being in Texas during the summer months. Community is the point. Today, I invite you to embrace discomfort on the road to a more vulnerable you.
Stay safe, Matt Johansen
@mattjay
