- Vulnerable U
- Posts
- 🎓️ Vulnerable U | #148
🎓️ Vulnerable U | #148
Amazon catching thousands of North Korean spies in recruiting pipeline, Microsoft kills RC4 ...finally, CISA leadership is a disaster, and much more!
Read Time: 8 minutes

Brought to you by:
Merry Christmas!
Taking some time to celebrate with family. Apologies if this edition is a bit brief - I don’t want to be the dad on my laptop on Christmas day for too long. But I did shovel some news stories into my notes this week. (As I finish up, I’m realizing I wound up about normal size. Apparently I can’t help myself.)

I hope you all got to spend some time off and with loved ones. My family always leaned a bit heavier into Christmas Eve with a table full of appetizers, dips, and baked ziti. This year due to some travel plans and all that we did “Elf Dinner” small foods on Xmas Eve, a cozy Christmas Day and then “Bonus Christmas” the day after with a big Italian feast. My family baked ziti recipe is more cheese than pasta but is a favorite.
Do you have any family traditions this holiday season? |
ICYMI
🖊️ Something I wrote: Context is King (cheating as a double up “something I read” with just my small note, but its a good read)
🎧️ Something I heard: Exposing Honey's Evil Business Model - Part 2 of some incredible investigative journalism about how this shady browser extension has been ripping off every side of their equation.
🎤 Something I said: this is going to get way worse... - My thoughts on the future of API key worms.
🔖 Something I read: Steam, Steel, and Infinite Minds
Vulnerable News
I’ve been scratching my head about this story a bit this week. I’ll eventually make a video about it but I couldn’t really figure out how I’d possibly even go about measuring “keystroke lag.” - Like lag between what? If the laptop is at a laptop farm in Tennessee or Arizona, you have EDR on it, and you measure keystroke on that timed to when it hits your corp servers, that shouldn’t change. But they seem to have found a hunt signal that let them figure out if a laptop was being remote controlled from Asia.
Interesting thread trying to disect this over on Twitter too:
As the story reads: their security team noticed that a contractor's laptop keystrokes were taking over 110 milliseconds to reach Seattle instead of the normal tens of milliseconds, immediately flagging that the "US-based" worker was actually halfway around the world.
They have blocked over 1,800 North Korean hiring attempts since April 2024, with a 27% increase each quarter this year. The imposter in this case was actually an Arizona woman who got prison time for helping run these fake worker schemes. Amazon's team spent time watching the person operate before kicking them out, and thankfully, the laptop didn't have access to anything sensitive.
Key useful notes for us here are these impostors follow predictable patterns - same schools, same hard-to-verify overseas consulting firms, and they consistently fumble basic English usage like "a," "an," and "the." (read more)
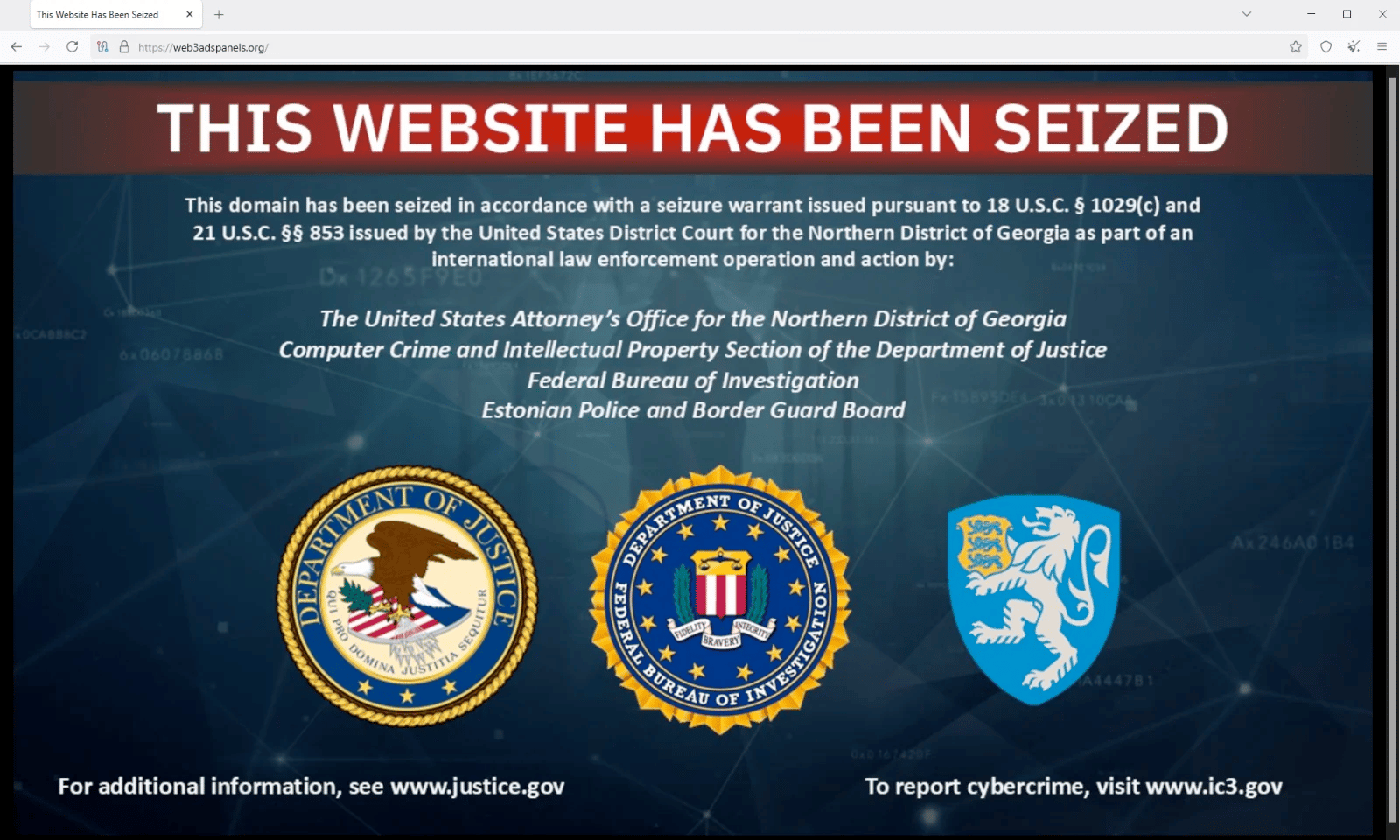
The FBI just took down another phishing operation, seizing the 'web3adspanels[.]org' domain that was storing stolen bank credentials from thousands of victims. The scammers were running fake ads on Google and Bing that would redirect people to lookalike banking sites to harvest their login info. They managed to grab $14.6 million in actual losses and tried for another $28 million on top of that from at least 19 confirmed victims across the US.
This wasn’t rocket surgery - just bought some search ads, create convincing fake banking portals, and wait for people to hand over their credentials. The domain was hosting a backend server that was active until November. Estonian law enforcement helped with the takedown, but no arrests yet. The FBI's seen over 5,100 similar complaints this year alone with $262 million in losses. Pro tip: bookmark your bank's actual website instead of Googling it and clicking top result. (read more)
I’ve been keeping an eye on this movement. When I get asked often about what kind of stuff keeps me up at night in the industry - I often answer how nation states like China have proven they can hack into these municipal utilities/critical infrastructure. They haven’t done anything with the access yet, but they’ve gotten in. These small water or power utilities can’t exactly compete with the Silicon Valley types for security talent or budgets. So some DEFCON groups have volunteered to help.
This most recent update talks about how they are moving from a volunteer hacker model to a full-blown MSSP framework specifically for rural water systems. The initiative, which previously matched white-hat hackers with utilities across six states, is now aiming to scale nationwide to help protect all 50,000+ water utilities. They've brought on cybersecurity veteran Tara Wheeler and are partnering with the National Rural Water Association to build what they're calling the "Water Watch Center" - essentially a hub-and-spoke model of regional MSSPs providing free security services to any water utility that needs it.
EPA found that over 70% of water systems failed basic cybersecurity checks in 2024, while Iranian and Chinese threat actors have been actively targeting these facilities. The new MSSP program will start with threat detection and monitoring before expanding to incident response and compliance support. (read more)
What a f*cking mess.

CISA's acting director just served up a masterclass in how not to handle failure. Madhu Gottumukkala wanted access to some ultra-sensitive cyber intelligence, took a polygraph to get it, failed, and then threw six career staffers under the bus by claiming they misled him into taking the test. Problem is, multiple officials say he pushed for the access despite being advised twice that he didn't actually need it and that previous leaders had skipped the polygraph entirely.
The whole mess has CISA staff calling the agency a "sinking ship" and "the Titanic." Six people got suspended with pay while DHS investigates whether they provided "false information" about the polygraph requirement. Meanwhile, CISA has already lost nearly a third of its workforce since January, doesn't have a permanent Senate-confirmed director, and is dealing with budget cuts. Nothing says strong leadership like failing a security clearance test and then blaming your subordinates for following your orders. (read more)
If you’re not following Peter on Twitter, he’s been on fire with these that have really got my funny bone lately.
About damn time. Microsoft just announced they're finally killing off RC4 encryption support by mid-2026, ending a 26-year run of what's essentially been a cryptographic nightmare. This ancient cipher has been a hacker's dream since the '90s - no salt, single MD4 hash round, basically crackable with a decent gaming rig. It's also been the default fallback for Active Directory authentication this whole time, even though they added AES support years ago.
The RC4 weakness was behind some nasty breaches, including last year's Ascension health system hack that disrupted 140 hospitals and exposed 5.6 million patient records. Senator Ron Wyden even called Microsoft out for "gross cybersecurity negligence" over this mess. Microsoft's excuse is it's tough to kill something that's been baked into every Windows install for decades. Fair enough, but maybe don't wait until a senator starts yelling at you publicly. At least they're providing tools to help admins identify any legacy systems still using RC4 before they flip the switch. (read more)
The UK's Foreign Office got popped back in October, and they're just now talking about it publicly. Trade Minister Chris Bryant confirmed the FCDO cyber-attack but is playing it pretty coy about who's responsible, despite The Sun pointing fingers at a Chinese group Storm 1849. This crew has allegedly been linked to the ArcaneDoor campaign that Cisco's been tracking, and they seem to have a thing for going after government critics and going after visa data - potentially tens of thousands of records this time.
This follows China's previous alleged hit on the UK's Electoral Commission that exposed 40 million people's data, so there's definitely a pattern here. The government says individual risk is low, but when you're talking about visa databases, that's exactly the kind of intel that could be useful for future operations. (read more)
The SEC just dropped charges on a $14 million crypto scam that had all the modern fraud greatest hits - fake AI investment tips, WhatsApp groups with phony "professors," and fake trading platforms. The op started with social media ads luring people into investment clubs where scammers posed as financial pros, then pushed victims onto fake platforms like Morocoin, Berge, and Cirkor that claimed to have government licenses. The platforms even offered fake Security Token Offerings for completely made-up companies like "SatCommTech" and "HumanBlock."
When investors tried to withdraw their money, the platforms demanded advance fees before cutting off access entirely. Some victims wired over $1 million individually, with funds quickly moved overseas through Chinese and Southeast Asian accounts. The scam pulled in at least $7.4 million in crypto and $6.6 million in fiat before getting shut down. (read more)
Socket's threat research team uncovered a spearphishing operation that's been abusing npm as a hosting platform for five months. The attackers published 27 malicious packages under six different aliases, turning the registry into durable phishing infrastructure that mimics secure document-sharing portals and Microsoft sign-ins. To put the “spear” in this “phishing” it was hyper targeted. They're going after specific sales people at 25 organizations across manufacturing, industrial automation, and healthcare sectors in the US and allied countries.
Tech breakdown in this report is great too. They deliver full browser-executed phishing flows with anti-analysis features like honeypot form fields, bot detection, and interaction gating that requires actual mouse/touch input. The lures pretend to be "MicroSecure" document sharing with hardcoded target email addresses, then transition to fake Microsoft login pages. The handoff infrastructure overlaps with known Evilginx AiTM phishing patterns, meaning they're potentially grabbing session tokens to bypass MFA. The threat actors likely sourced targets from trade show directories like K-Fair and Interpack - makes sense since these industrial events publish exhibitor contact lists openly. (read more)
Alright this one is rough for us security nerds. Malware posing as PoCs for new vulns that come out and its all hosted on GitHub. They've been targeting vulnerabilities like CVE-2025-59295 (Windows MSHTML buffer overflow) and others that got media coverage, complete with AI-generated descriptions that look pretty convincing at first glance.
Kaspersky found 15 of these repos before they got nuked, each containing password-protected ZIPs with the usual dropper that disables Windows Defender and pulls down the main WebRAT payload. It's the same old infostealer with webcam spying and credential theft for Steam, Discord, and crypto wallets. I know a lot of practitioners read this so fair warning - if you're hunting for exploit code on GitHub, maybe test it in a VM first. Because nothing says "legitimate security research" quite like downloading random executables from the internet, right? (read more)
I know all my AI nerd friends have been messing with n8n. Hopefully not on servers exposed from the Internet, but what I’d be worried about here is if the vulnerability can be exploited via input that gets sucked into a workflow from the Internet. A lot of people setup workflows that listen for RSS feeds or social media stuff - feels very log4j in that sense that exploit can be triggered as ingested. It’s patched, so grab an update! (read more)
Remember that LastPass breach from 2022? Apparently it’s the gift that keeps on giving. Researchers just traced over $35 million in stolen crypto from victims whose wallets are still getting drained years later. Turns out many users never bothered changing their weak master passwords, so hackers have been slowly cracking vaults and emptying crypto wallets ever since.
TRM used "demixing" techniques to trace the funds even after they went through CoinJoin mixers like Wasabi Wallet. The stolen Bitcoin consistently flowed to Russian exchanges including Cryptex (now sanctioned) and Audi6. Multiple indicators point to Russian cybercriminal involvement, from the infrastructure used to wallet behavior patterns. (read more)
Miscellaneous mattjay

How'd I do this edition?It's hard doing this in a vacuum. Screaming into a void. Feedback is incredibly valuable to make sure I'm making a newsletter you love getting every week. |
Parting Thoughts:
Community was foundational in launching and propelling my career. Community is the only reason I can stand being in Texas during the summer months. Community is the point. Today, I invite you to embrace discomfort on the road to a more vulnerable you.
Stay safe, Matt Johansen
@mattjay
