- Vulnerable U
- Posts
- 🎓️ Vulnerable U | #149
🎓️ Vulnerable U | #149
MongoBleed Christmas Present, Major crypto heist via malware that resulted from npm worm, React vuln still causing breaches, and much more!
Read Time: 5 minutes

Brought to you by:
Howdy friends!
Happy New Year! Not a big resolution guy myself. Let’s all just focus on being better community members. Define community however you like. But let’s be the best we can be in whatever circle we draw. Happier, healthier, wealthier. Onward!
I bought myself a Christmas present yesterday - a whole new YouTube studio setup. Moving off my USB mic and webcam that got us to 20k+ subscribers. On to XLR mics and Mirrorless cameras with professional lighting rigs. - I’m under no illusion that the video quality is the thing keeping me from a large YouTube channel, but it felt like a good time to upgrade. I’ll give you guys a bit of a run through when it is all setup.
ICYMI
🖊️ Something I wrote: This is the new bar btw. It’s been set. I have a feeling if we don’t all start clearing this expectation we’ll be considered dinosaurs.
🎧️ Something I heard: LowLevel’s summary of MongoBleed
🎤 Something I said: this is going to get way worse...
🔖 Something I read: The Prison Of Financial Mediocrity
Vulnerable News
MongoBleed
I couldn’t link just one main story here. There are a lot of good writeups. - This is one of those holiday ruiners. Major vuln, super widespread, very easy to exploit, quickly weaponized.
Just sucks that eveyrone involved dropped this stuff Xmas and Xmas Eve. Someone from Elastic Security dropped a working exploit for CVE-2025-14847 on Christmas Morning. Coal in his stocking I guess. The exploit is stupidly simple - just point it at an IP and watch it hoover up database passwords, AWS keys, and other juicy secrets that MongoDB keeps in plaintext memory.
This bug lets unauthenticated attackers remotely leak sensitive data by sending malformed compressed packets that trick the server into returning uninitialized heap memory. (Hence the -Bleed name. it fits!) The flaw sits in the zlib decompression logic that runs before authentication, so basically anyone can poke at it. Wiz found that 42% of cloud environments are running vulnerable versions, and there's already a public exploit floating around with active exploitation in the wild.
The good news is patches are available across all supported versions (8.2.3, 8.0.17, 7.0.28, etc.), and if you can't patch immediately, you can disable zlib compression as a workaround. MongoDB Atlas users got auto-patched, so they're sorted. The bad news - Censys spotted about 87K potentially vulnerable instances worldwide just sitting on the internet.
LowLevel has a very good summary: https://youtu.be/9Wg6tiaar9M
Gossi has a great writuep - https://doublepulsar.com/merry-christmas-day-have-a-mongodb-security-incident-9537f54289eb
Eric Capuano has a great hunting guide - https://blog.ecapuano.com/p/hunting-mongobleed-cve-2025-14847
Wiz’s data is always useful in these situations too - https://www.wiz.io/blog/mongobleed-cve-2025-14847-exploited-in-the-wild-mongodb
There is always an xkcd that explains better - https://xkcd.com/1354/
LLMs fail in ways traditional SAST and threat models were not designed to catch. This guide breaks down the OWASP Top 10 for LLM Applications with concrete examples of how these failures show up in production LLM architectures and how teams mitigate them before shipping. (read more)
*Sponsored
Spoiler alert: they don’t know if they can solve this. Their browser agent, Atlas, can click around and interact with websites just like you would, which makes it a target for bad actors trying to hijack it with malicious instructions. They found an attack where a poisoned email could trick the agent into sending your boss a resignation letter when you just asked it to write an out-of-office reply.
I made a video about this a few weeks ago.
They built an automated red team system using reinforcement learning that continuously hunts for new prompt injection techniques. When it finds something that works, they immediately patch the defenses and retrain their models. Kind of wild that we just …don’t really have an answer to this. Not that it would be less cat and mouse if we did, I mean look at 20+ years of XSS we’ve known how to solve. (read more)
Trust Wallet just dropped a post-mortem on how they got absolutely wrecked by the Shai-Hulud supply chain worm back in November. Turns out their GitHub secrets got exposed, which handed attackers the keys to their Chrome Web Store API. The bad actors then pushed a trojanized version (2.68) of their browser extension that silently harvested users' seed phrases every time they unlocked their wallets. Pretty neat detail to me - they disguised the stolen data as error telemetry, so it looked like normal analytics traffic.
About $8.5 million drained from 2,520 wallet addresses into 17 attacker-controlled wallets. They staged the infrastructure on December 8th but didn't push the malicious update until December 24th. Even left a little Dune reference ("He who controls the spice controls the universe") on their command server. I knew that worm story wasn’t over. (read more)
Love a good report based on hard to aggregate or private data. While security incidents actually dropped from 410 to 200 compared to 2024, total losses jumped 46% to nearly $3 billion. A single Bybit incident accounted for $1.46 billion of that damage. Meanwhile, North Korean hacker groups had a helluva year, stealing $1.645 billion in just the first nine months.
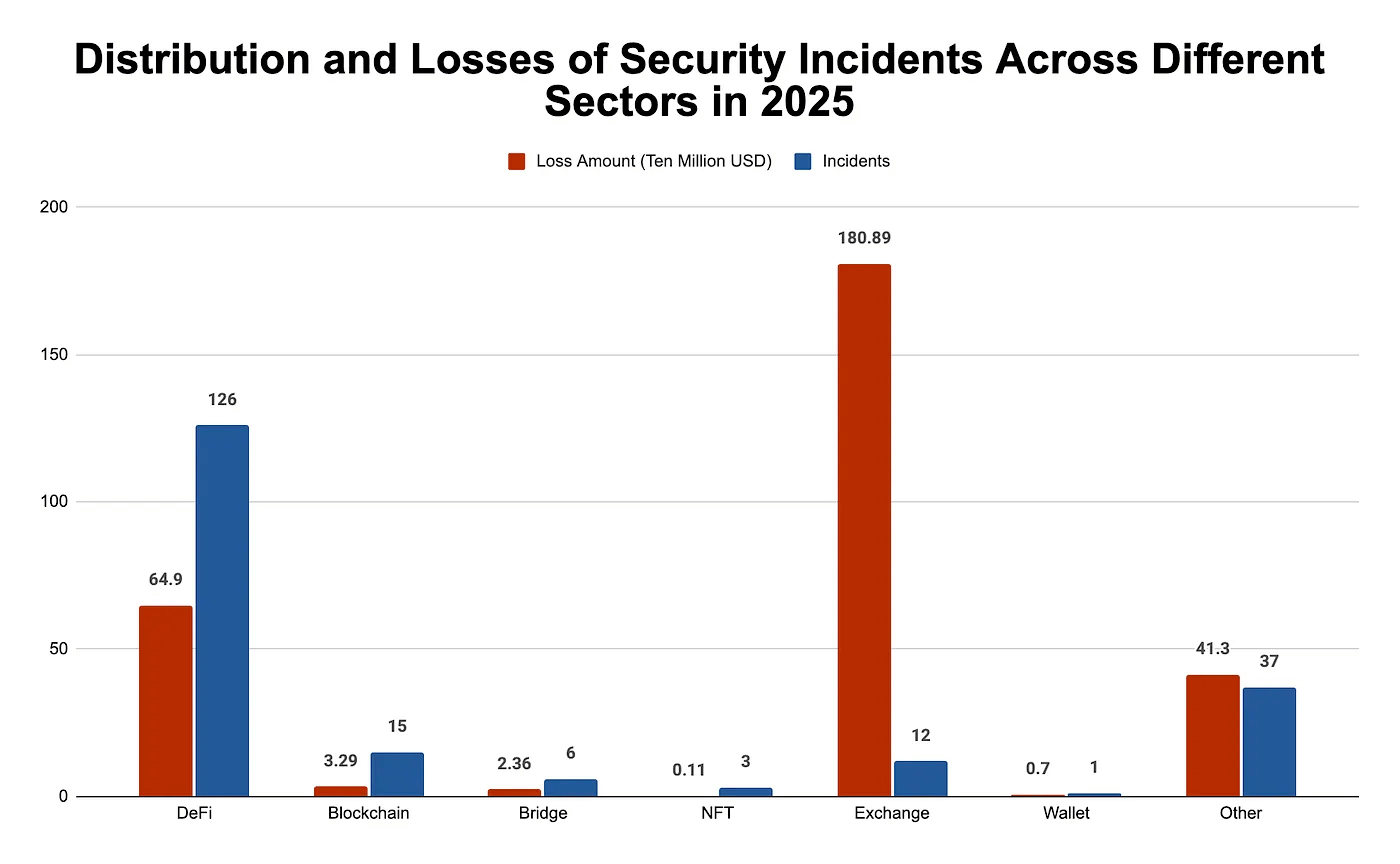
Wallet drainer attacks actually declined significantly (down 83% to $83.85 million), but that's probably cold comfort when you look at the overall trend. On the flip side, regulators are finally getting their act together with more cross-border enforcement and tighter scrutiny of mixing services. (read more)
RondoDox botnet has been hammering Next.js servers since early December. If you missed me talking about it when it came out - this RCE flaw can be exploited with a single HTTP request and affects anything using React Server Components. It’s everywhere. Over 94,000 exposed assets just sitting there waiting to get pwned.
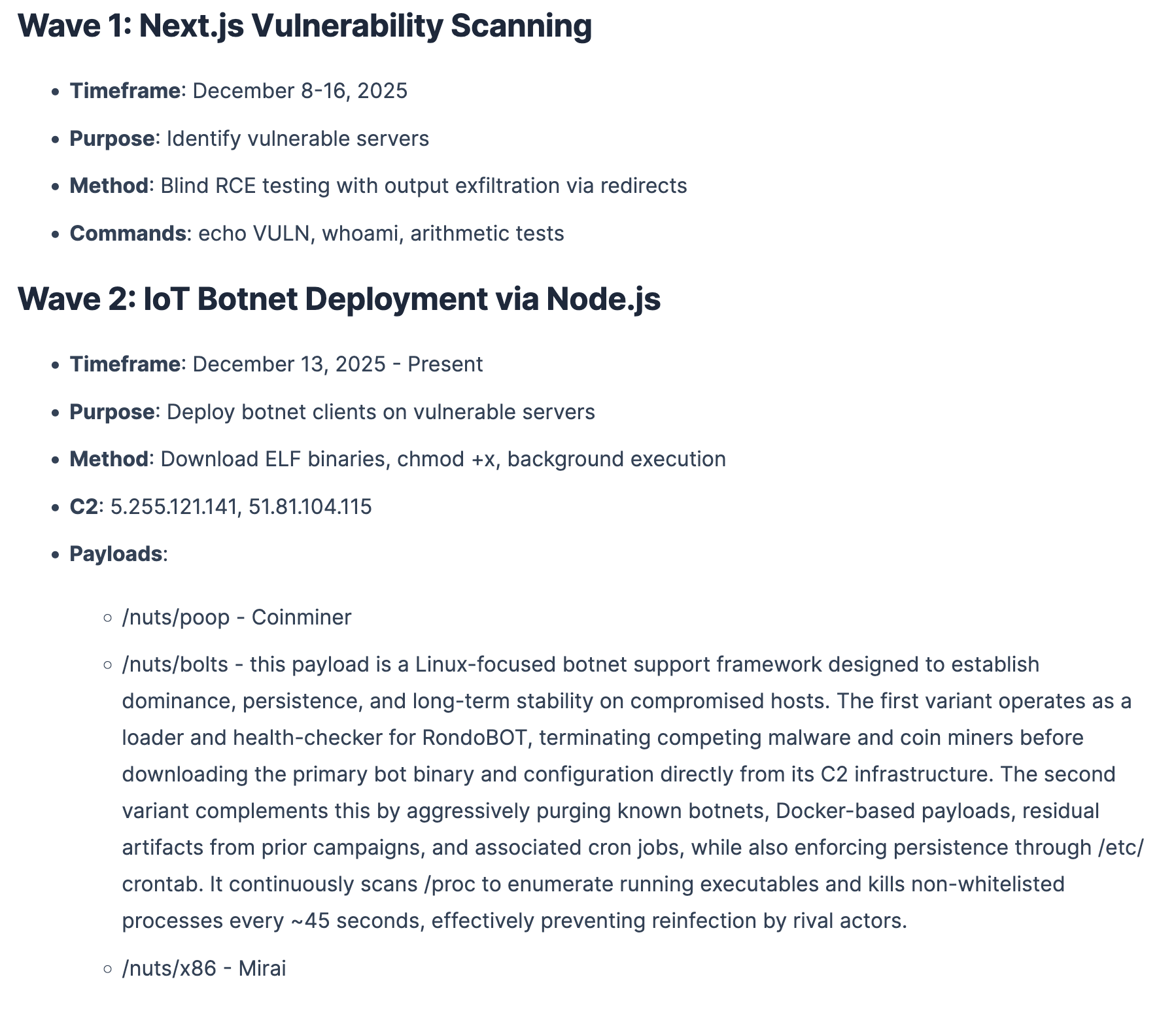
The group behind this botnet are running hourly exploitation waves, dropping cryptominers, Mirai variants, and botnet loaders with fun names like "/nuts/poop" and "/nuts/bolts." The latter kills competing malware and enforces persistence every 45 seconds, because apparently they don't like sharing. North Korean hackers are also in on the action, using React2Shell to deploy their EtherRAT malware. (read more)
Huntress with a good review of social engineering they saw in the wild this year. Threat actors are still having success with the classics - fake Social Security statements, party invitations, and overdue invoices to trick people into downloading their malicious RMM tools.
ScreenConnect accounts for 74.5% of all the abused remote access tools Huntress sees, and RMM abuse makes up 17.3% of all threat actor remote access methods. The attackers are smart about it too, using legitimate tools that bypass traditional AV while giving them full remote access. The good news is these attacks are pretty detectable if you're looking for unauthorized RMM instances calling back to sketchy domains. (read more)
I more liked 4th wave emo, not 4th wave of malware, but here we are. This GlassWorm malware-slinging VS Code extension crew has pivoted from Windows to macOS, racked up 50,000 downloads. They also started replacing legitimate hardware wallet apps like Ledger Live and Trezor Suite with trojanized versions. They've also ditched their previous invisible Unicode and Rust binary techniques for AES-encrypted JavaScript payloads that wait 15 minutes before executing, effectively dodging most automated sandbox detection.
Every time researchers expose this group’s methods, they adapt within weeks - four distinct waves in just two and a half months. The hardware wallet trojan capability is especially gnarly since it targets what's supposed to be the most secure way to store crypto. While the trojan payloads aren't fully active yet (the C2 is serving empty files), the infrastructure is there and ready. Plus they're still stealing everything else - 50+ crypto wallets, developer credentials, SSH keys, macOS Keychain data, etc. (read more)
Ryan Goldberg from Georgia and Kevin Martin from Texas both pleaded guilty to working with the ALPHV Blackcat ransomware gang to shake down U.S. companies for crypto. These weren't script kiddies - Goldberg worked at Sygnia and Martin at DigitalMint, so they had the inside knowledge to really do some damage.
The whole thing feels like a nightmare scenario where the people supposed to protect you are actively working against you. Both companies quickly threw their former employees under the bus and said they cooperated fully with the DOJ investigation. There's apparently a third conspirator out there somewhere, but ALPHV Blackcat itself vanished after that massive UnitedHealth attack last year. Both guys are looking at up to 20 years in prison come March sentencing. (read more)
Georgia just arrested their former spy chief Grigol Liluashvili for allegedly taking bribes to protect scam call centers that were ripping off people worldwide. The guy who was supposed to be fighting cybercrime was apparently getting paid $1.4 million to look the other way while fraudsters operated with impunity. When asked about his potential arrest, he told reporters "Everything is God's will" - which feels like an interesting way to frame alleged corruption.
Investigative journalists found one of these major scam operations literally right next to the state security service headquarters in Tbilisi. That particular outfit employed 85 people and pulled in $35.3 million from over 6,100 victims since 2022. Keep your enemies close and all that… His cousin Sandro is already in custody on related charges, and if convicted, Liluashvili could be looking at 15 years behind bars. Sometimes the call really is coming from inside the house. (read more)
Miscellaneous mattjay

How'd I do this edition?It's hard doing this in a vacuum. Screaming into a void. Feedback is incredibly valuable to make sure I'm making a newsletter you love getting every week. |
Parting Thoughts:
Community was foundational in launching and propelling my career. Community is the only reason I can stand being in Texas during the summer months. Community is the point. Today, I invite you to embrace discomfort on the road to a more vulnerable you.
Stay safe, Matt Johansen
@mattjay