- Vulnerable U
- Posts
- 🎓️ Vulnerable U | #150
🎓️ Vulnerable U | #150
China hacking Congressional staff, ICE tracking everyone's location without warrants via data broker info, ESXi exploits in the wild, Stalkerware producer pleads guilty, and more!
Read Time: 8 minutes

Brought to you by:
Howdy friends!
Setting up my new office/studio this week. Lot’s of new hardware to figure out. But! The direction I’m going is to put out significantly more and higher quality content in 2026. We’ve grown a bit at VulnU and we’ve got some new video producers, writers, social media, and community managers.
VulnU Premium will soon come with a community as promised, and when that happens I’ll be upping the price a bit to help cover all the programming we’ll be doing in there. So Go ahead and upgrade now to keep current price and thank you so much for those who have already been supporting.
What would you be most excited about in a VulnU community?After you vote, you get an extra text box - consider it a suggestion box. Lemme know what you'd want to see in there. |
|
ICYMI
🖊️ Something I wrote: Some code?! (gasp) - I’ve been helping a good buddy of mine Pedram with this project he’s been working on for AI Agent Orchestration - Maestro.
🎧️ Something I heard: I think I’m going to try to follow this guide from NetworkChuck on rolling my own security cameras
🎤 Something I said: IBM’s AI Agent vulnerable to prompt injection
🔖 Something I read: Important for us security people to stay on top of the latest in AI coding even if you hate it. How will we secure what we don’t know is happening. This Ralph tool went viral - and a lot of similar tools popping up.
Vulnerable News
Salt Typhoon strikes again, this time hitting congressional committee staff emails. Chinese intelligence managed to breach email systems used by staffers on some pretty high-profile committees - the House China committee, foreign affairs, intelligence, and armed services panels. The intrusions were spotted in December, though it's unclear if they actually got into lawmakers' personal emails or just staff accounts.
This is all part of the ongoing Salt Typhoon campaign that's been running for years, giving China's Ministry of State Security access to basically anyone's unencrypted calls, texts, and voicemails. US telecom companies haven't done much to shore up their defenses because, surprise, it's expensive. Treasury was ready to drop sanctions on the MSS entities behind this mess but pulled back because they didn't want to mess with the Trump-Xi détente. Meanwhile, China's doing the usual "we don't know what you're talking about" routine through their embassy. (read more)
Yeah, same problem everywhere.
Compliance fails because manual checks can’t keep up with how fast everything changes. Drata takes that work off your plate by continuously monitoring controls across frameworks like SOC 2 and ISO 27001, so you’re not scrambling every time an audit pops up.
It plugs into the tools you already use, pulls evidence automatically, and gives you real-time visibility into where risk is creeping in, without slowing engineers down.
If staying compliant and reducing risk without dreading audit season sounds appealing, this is worth a look. (read more)
*Sponsored
Some FOIA work done by ACLU and 404media shows ICE bought 2 tools used to track people’s locations without a warrant. The company Penlink has two tools, Tangles and Webloc. Webloc is basically Google Maps where you can draw a shape and find every device inside it’s borders within a given timeframe. Likely data bought from data brokers/advertisers based on apps we have on our phones selling the info.

Tangles is a facial recognition app that matches photos of people to their social media and online presence. It then performs “sentiment analysis” about that person. They demonstrated this on protestors photos of their face which then traced back to full online identities. The company swears they are doing nothing wrong, the Supreme Court has held up that there isn’t a reasonable expectation of privacy for data you’ve willingly given up (installed the app, gave it permissions). - I don’t think any of us have willingly participated in this data broker ecosystem just so we could check the weather on our phones. (read more)
This is a fun one. Also is becoming my most watched video across multiple sites…
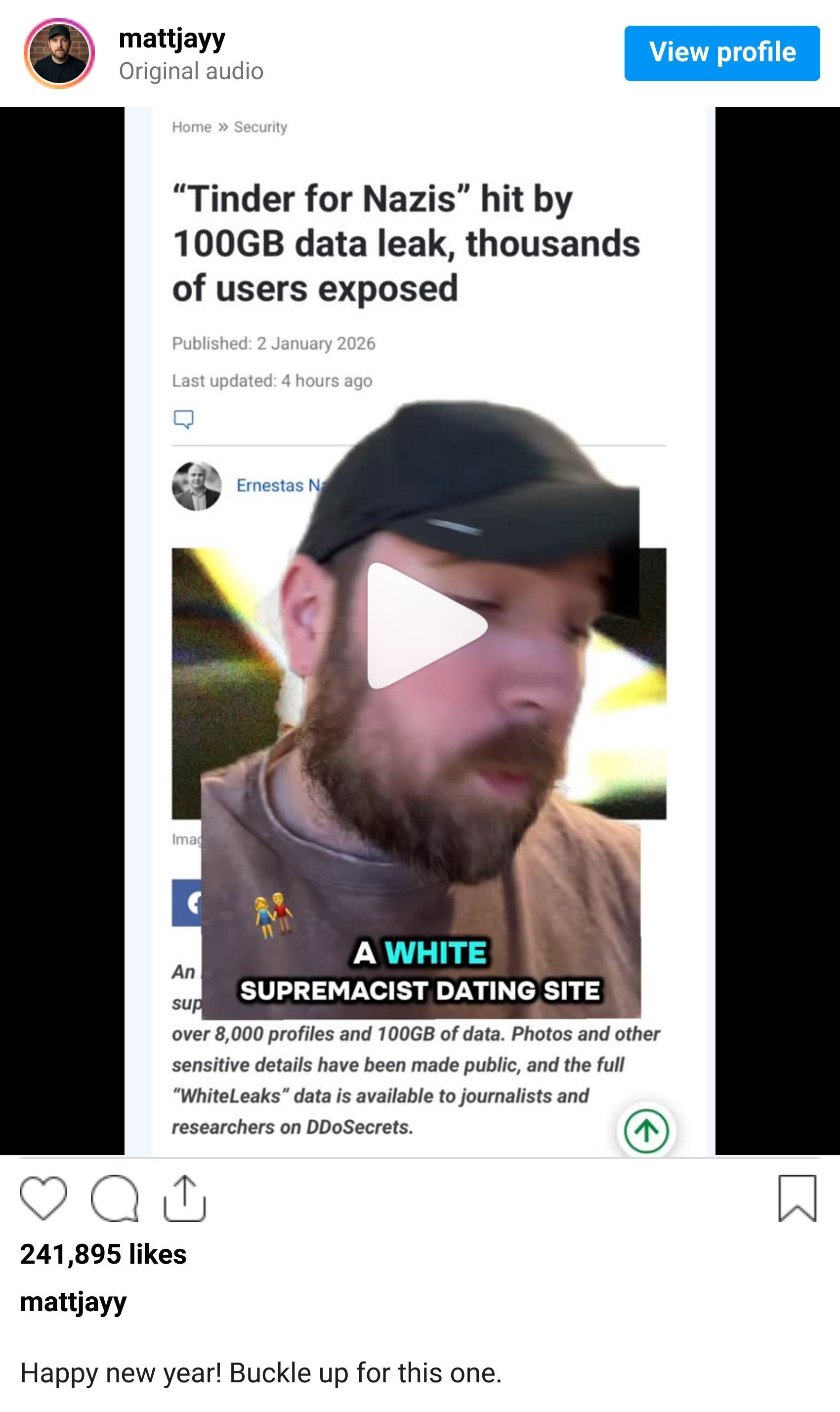
An investigative journalist going by "Martha Root" just pulled off a pretty wild social engineering operation against white supremacist dating sites. She used AI chatbots powered by local LLMs to create fake accounts that were so convincing they got verified as "white" and had users falling in love with them over weeks of conversations. While the bots were busy making soul mates, Root was collecting data - over 8,000 profiles and 100GB worth from WhiteDate, WhiteChild, and WhiteDeal.
The exposed data includes everything from personal details to photos with EXIF metadata containing GPS coordinates, basically handing out home addresses. She presented the findings at Chaos Communications Congress and made the dataset available to researchers through DDoSecrets. She also got a round of applause live when she ran a bunch of scripts on stage to delete the whole hacked site off the Internet, including backups.
This was the most disgusting thing I’d ever seen on Twitter, and that’s saying something. I didn’t even want to screenshot it to spread it, or even have that on my hard drive. But people have not only been convincing Grok to undress women without their consent, but also it started producing CSAM. Somebody outraged RT’d it and thats how it came across my timeline and I couldn’t believe it.
Researchers found around 1,200 cached URLs from Grok's website showing it's been cranking out seriously disturbing sexual content - violent, graphic stuff that makes X's "undressed" images look tame. About 10% of the content appears to involve minors, which researchers have reported to European regulators. Unlike other AI companies that block adult content, xAI lets Grok run wild with its "spicy" mode.
The depravity is organized too. There's a 300-page forum thread dedicated to sharing prompts that bypass xAI's safety measures, complete with success rates and workarounds. No age verification either, despite hosting explicit content that would trigger those new state laws. Meanwhile, xAI isn't responding to press inquiries, though Musk has said people creating illegal content will face consequences. (read more)
During a Mar-a-Lago press conference about the Venezuela operation that nabbed Maduro, he straight up said the US turned off Caracas's lights using "a certain expertise that we have." Gen. Dan Caine backed this up, mentioning that Cyber Command and Space Command were "layering different effects" to create a pathway for US forces. That's about as close as you'll get to officials admitting they cyber-attacked another country's power grid.
This is pretty wild territory - the US typically keeps these operations under wraps, and for good reason. NetBlocks confirmed internet outages during the power cuts, and this follows previous attacks on Venezuela's state oil company PDVSA that they blamed on Washington. Venezuela's not exactly a cyber superpower, but publicly flexing like this sets some interesting precedents. (read more)
Cambodia just handed over Chen Zhi to China, and this guy's story is insane. The 37-year-old billionaire was allegedly running one of the biggest crypto scam operations ever through his Prince Group empire. $15 billion in Bitcoin that the FBI seized - that's "one of the largest financial fraud takedowns in history" according to them. His whole setup involved trafficking people to Cambodia under the guise of legitimate jobs, then forcing them to run online scams from what are basically digital sweatshops.
Chen Zhi had given up his Chinese citizenship to become Cambodian in 2014, and his Prince Group was everywhere - banks, real estate, you name it. Some estimates suggest scam operations like his account for around half of Cambodia's entire economy. The UN says hundreds of thousands of people have been trafficked to Southeast Asia for these scam farms. China's been quietly investigating since 2020, but it took international pressure and sanctions from the US and UK to really get things moving. (read more)
KrebsOnSecurity did some solid detective work tracing the money behind those massive Kimwolf and Aisuru botnets that enslaved millions of Android TV boxes. Turns out a Utah company called Resi Rack was hosting key infrastructure, with co-founder "Shox" actively involved in Discord channels selling proxy services. The investigation also revealed connections to several sketchy proxy providers like Plainproxies/ByteConnect and Maskify, which were essentially laundering botnet traffic for dirt-cheap prices that legit providers can't match.
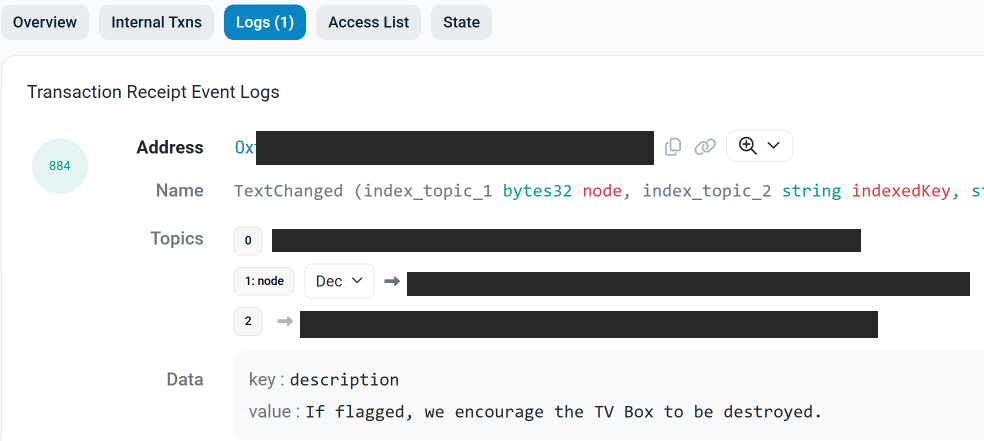
The botmasters didn't take kindly to the exposure. Right after the first story dropped, they nuked their Discord server, DDoSed the security firm Synthient, and even used Ethereum Name Service records to dox researchers. They're using blockchain infrastructure to make their command-and-control servers harder to take down. If you've got one of these infected Android TV boxes, just trash it - there's no fixing these things once they're compromised. Here is a list of models to look for and throw out. (read more)
Huntress just dropped a great breakdown of a VMware ESXi exploit they caught in the wild. The attackers got in through a compromised SonicWall VPN (because of course they did), then deployed a full hypervisor escape that breaks out of guest VMs to own the entire ESXi host. The toolkit supports 155 different ESXi builds spanning versions 5.1 through 8.0, and the PDB paths suggest it was developed as a zero-day over a year before VMware's March disclosure. Chinese strings in the development paths point to well-resourced developers likely operating in a Chinese-speaking region.
What makes this particularly sneaky is the use of VSOCK for backdoor communication, which completely bypasses traditional network monitoring since the traffic never hits the network stack. The exploit chains three CVEs to leak memory, corrupt VMX processes, and escape the sandbox, ultimately dropping a backdoor called "VSOCKpuppet" that listens on VSOCK port 10000. If you're running ESXi 7.0 or 8.0, patch immediately. If you're still on 6.x or earlier, well, you're out of luck since those are end-of-life with no fixes available. Hypervisor security is fun! (read more)

Bryan Fleming just learned the expensive way that running a "catch a cheater" spyware operation isn't actually legal. He created pcTattletale back in 2002 as legitimate monitoring software for parents and employers, but somewhere along the line it morphed into full-blown stalkerware. By 2022, the company was actively marketing to people wanting to spy on their partners, complete with blog posts on catching cheating boyfriends and instructions to install it "when they are sleeping."
The feds had been watching Fleming help customers with tech support requests like hiding screenshot notifications from suspicious spouses. After a 2022 raid on his home and a 2024 data breach that basically killed the business anyway, Fleming finally pled guilty to knowingly selling software for surreptitious interception. One stalkerware operation down, unfortunately plenty more still out there. (read more)
Miscellaneous mattjay
How'd I do this edition?It's hard doing this in a vacuum. Screaming into a void. Feedback is incredibly valuable to make sure I'm making a newsletter you love getting every week. |
Parting Thoughts:
Community was foundational in launching and propelling my career. Community is the only reason I can stand being in Texas during the summer months. Community is the point. Today, I invite you to embrace discomfort on the road to a more vulnerable you.
Stay safe, Matt Johansen
@mattjay