- Vulnerable U
- Posts
- 🎓️ Vulnerable U | #152
🎓️ Vulnerable U | #152
curl bug bounty ended over ai slop, LLM generating polymorphic malware client side in real time, Zendesk hijacked for massive spam storm, and much more!
Read Time: 9 minutes

Brought to you by:
Howdy friends!
Had a better week this week after last week’s disaster. Everyone is on the mend over here and we’ve kept busy. One of my Xmas gifts to my daughter was piano lessons so it has been a ton of fun hearing that and watching her be so proud of Old MacDonald Had a Farm. I also got to take her out to a ranch this weekend with a few of her friends where they got to just mob around like wild animals. It was a good reset.

If you’re reading this as the cold front hits the US - may it find you warm and with power. I’m over here watching Ted Cruz flying off to vacation again thinking the Texas power grid is shaking in its boots. Hope its a big nothing burger and we all just get a Sunday to stay inside under blankets.
The new studio is fully setup now and I’ve been live streaming all week on YouTube and Twitch. Thanks for all of you who dropped by as I worked out the kinks, but this week’s YouTube vids coming out will be the first with the new equipment and editor. Feedback welcome! Will drop Friday.
ICYMI
🎧️ Something I heard: "I made an Evil MCP server" (and AI fell for it)
🎤 Something I said: this npm worm situation is going to get worse.
🔖 Something I read: Jhaddix over at Arcanum published an awesome repo of security context to feed AI agents so they produce more secure code.
Vulnerable News
Ok. This sucks. We’ve covered a lot of this AI slop bug bounty report stuff before. It finally hit a tipping point for the curl team and they are throwing in the towel. These open source tools on Unix boxes that basically run the internet are really under supported with these small teams.
Daniel Stenberg just pulled the plug, and honestly, you can't blame the guy. He's been drowning in AI-generated garbage reports since early 2024, with the situation getting so bad that he was spending way too much time sifting through seven weekly submissions that turned out to be duds. The final straw seems to be that none of these recent reports actually described real vulnerabilities, despite taking "a good while" to assess.
Stenberg's hoping that removing the cash incentive will stem the tide of low-effort submissions, though he still wants developers to report actual security bugs even without getting paid. Here comes the “No more free bugs!” debate of 2009 all over again. He's also doubling down on his policy of publicly roasting people who submit junk reports, though he admits some of these folks are just misled humans who might learn from the experience. (read more)

Zero Trust World is happening March 4 to 6, 2026 in Orlando, Florida. The focus is hands-on security work paired with thoughtful discussion across the industry.
The schedule includes live hacking labs, keynotes, and breakout sessions on topics like IoT exploitation, security roadmaps, remote workforce protection, dark web fundamentals, and prompt engineering. Attendees can earn CPE credits, take Cyber Hero certification exams onsite, and connect with practitioners and experts who work on these problems every day.
Registration is open now. Save $200 with code ZTWVULNERABLEU26 at https://ztw.com
*Sponsored
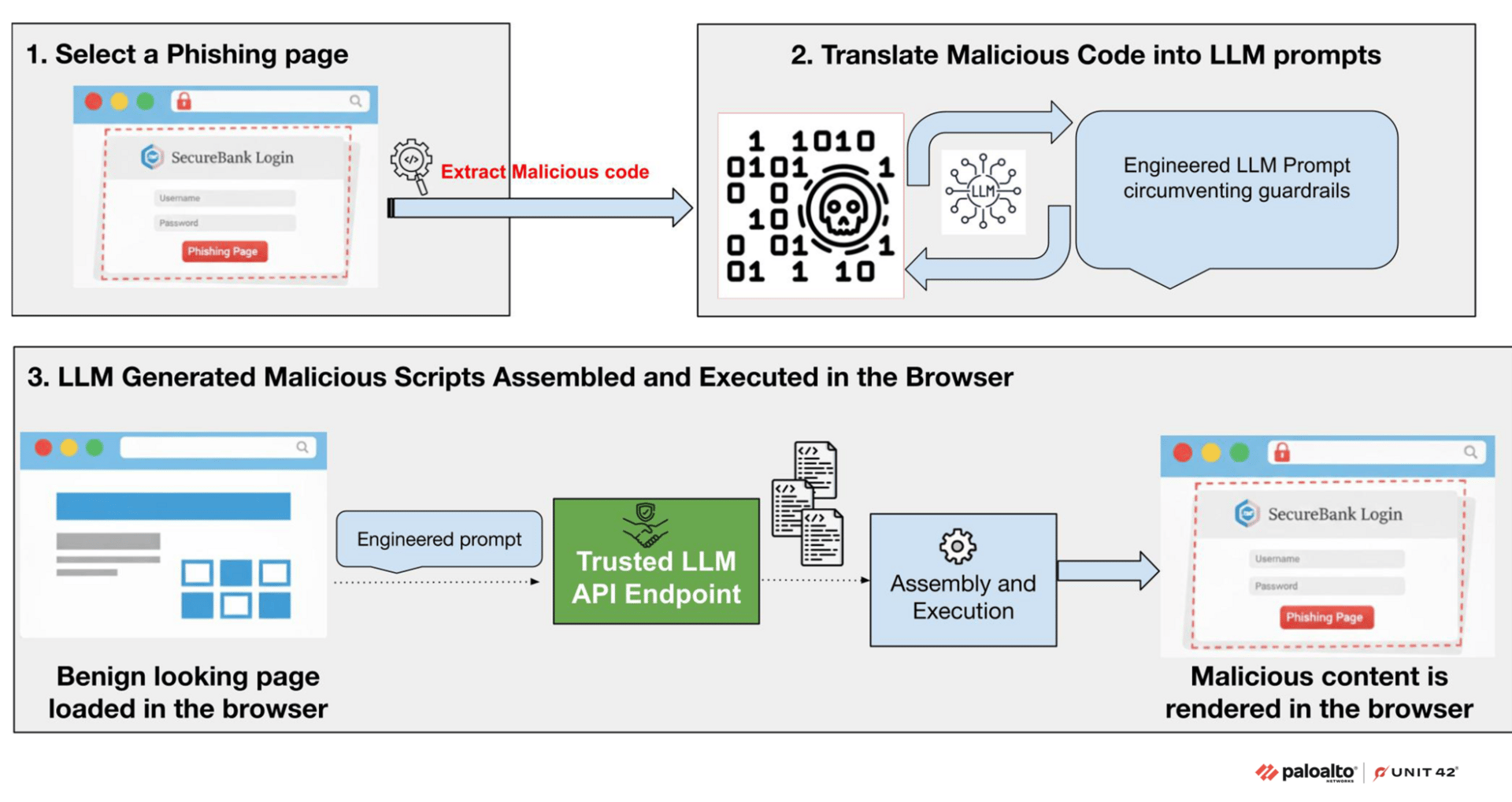
This is a much bigger deal than it seems. Instead of hosting static malicious JavaScript, attackers are now using LLMs like DeepSeek and Gemini to generate phishing code in real-time right in your browser. The webpage starts out completely benign, then makes API calls to trusted LLM services to build the malicious payload on the fly. Each visit gets a unique, polymorphic variant of the code, and it's all coming from domains you'd normally trust.
The researchers showed how simple prompt engineering can bypass LLM safety guardrails - asking for "AJAX POST function" instead of "credential exfiltration code" was enough to slip past the filters. The defense challenge is real here because traditional network analysis won't catch it - you need runtime behavioral detection actually running in the browser to spot this stuff. Even then, the code and behavior changes every time. This is a sign of bad things to come. (read more)
GNU just dropped a doozy. CVE-2026-24061 scores a nasty 9.8 CVSS and has been lurking around since 2015, affecting versions 1.9.3 through 2.7. The bug lets attackers bypass login completely by sending "-f root" as the USER environment variable, which telnetd happily passes along to the login binary without any sanitization. Since login interprets "-f" as "skip authentication," boom - instant root access. Absolutely bananas.
GreyNoise is already seeing active exploitation attempts from 21 different IP addresses across multiple countries, so we’ve got a live one! The vulnerability was introduced in a March 2015 commit and made it into the May release that year - took almost 11 years for someone to notice the problem. If you're still running telnetd for some reason (and honestly, why?), patch immediately or just disable the service entirely. SSH exists btw. (read more)
Hacking cars! Always so fun. Pwn2Own Automotive is going on in Tokyo right now, and day two was another vuln party. Researchers bagged $439,250 by popping 29 zero-days across EV chargers, infotainment systems, and car operating systems. Fuzzware[.]io is dominating the leaderboard with $213,000 earned so far, absolutely demolishing everything from Phoenix Contact charging controllers to ChargePoint Home Flex chargers. Other teams are having a field day too - Sina Kheirkhah rooted some Kenwood and Alpine systems, while Rob Blakely and Hank Chen each walked away with $40,000 for their automotive hacks.
After just two days, we're looking at nearly a million dollars in payouts ($955,750) for 66 zero-day vulnerabilities. That's already more than last year's total haul of $886,250. Day three is looking spicy with teams going after more charging stations and the Autel MaxiCharger. The 90-day disclosure timeline means vendors have until April to patch these bugs before they go public. What a time to just be driving a bunch of computers with wheels. And yes, Tesla got popped. (read more)
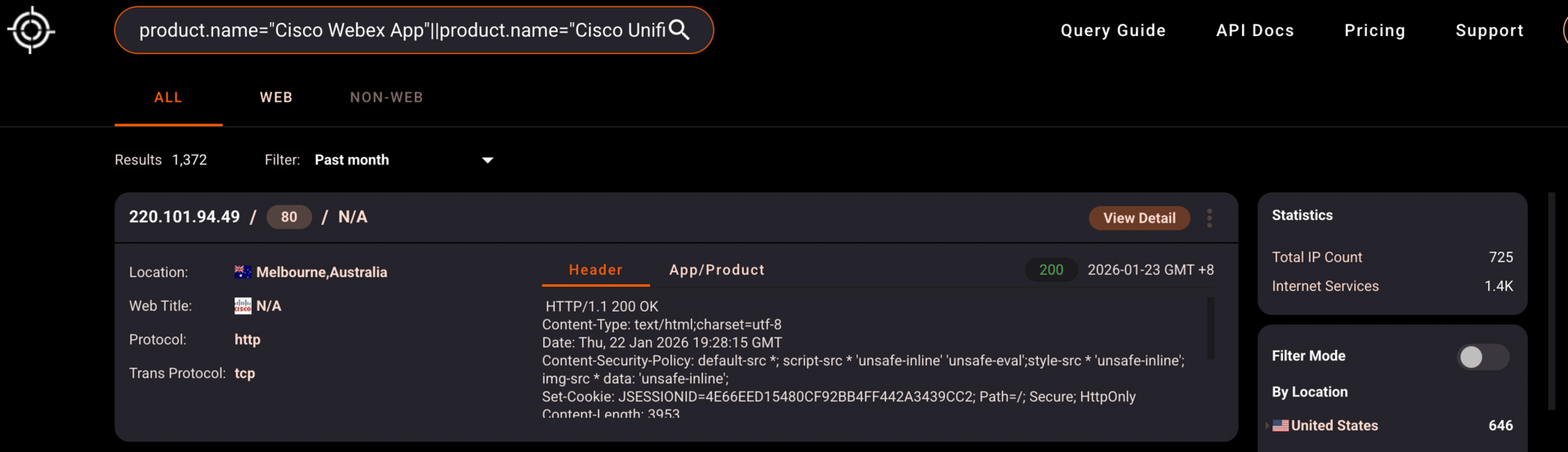
Hunter results on vulnerable boxes
Another day, another Cisco zero-day getting hammered in the wild. CVE-2026-20045 is the latest crit affecting their Unified Communications Manager and related products, allowing unauthenticated remote code execution through crafted HTTP requests to the web management interface. Attackers can grab user-level access and escalate to root, which is about as bad as it gets for enterprise comms infrastructure.
CISA's already tossed this one onto their Known Exploited Vulnerabilities list with a February 11 deadline for federal agencies. Hunter's showing around 1,300 exposed instances globally, with nearly half sitting in the US. This marks yet another addition to CISA's growing collection of Cisco vulns - they're up to about 80 now over the past decade, with eight added just last year. If it's Cisco and it's internet-facing, get your story straight. (read more)
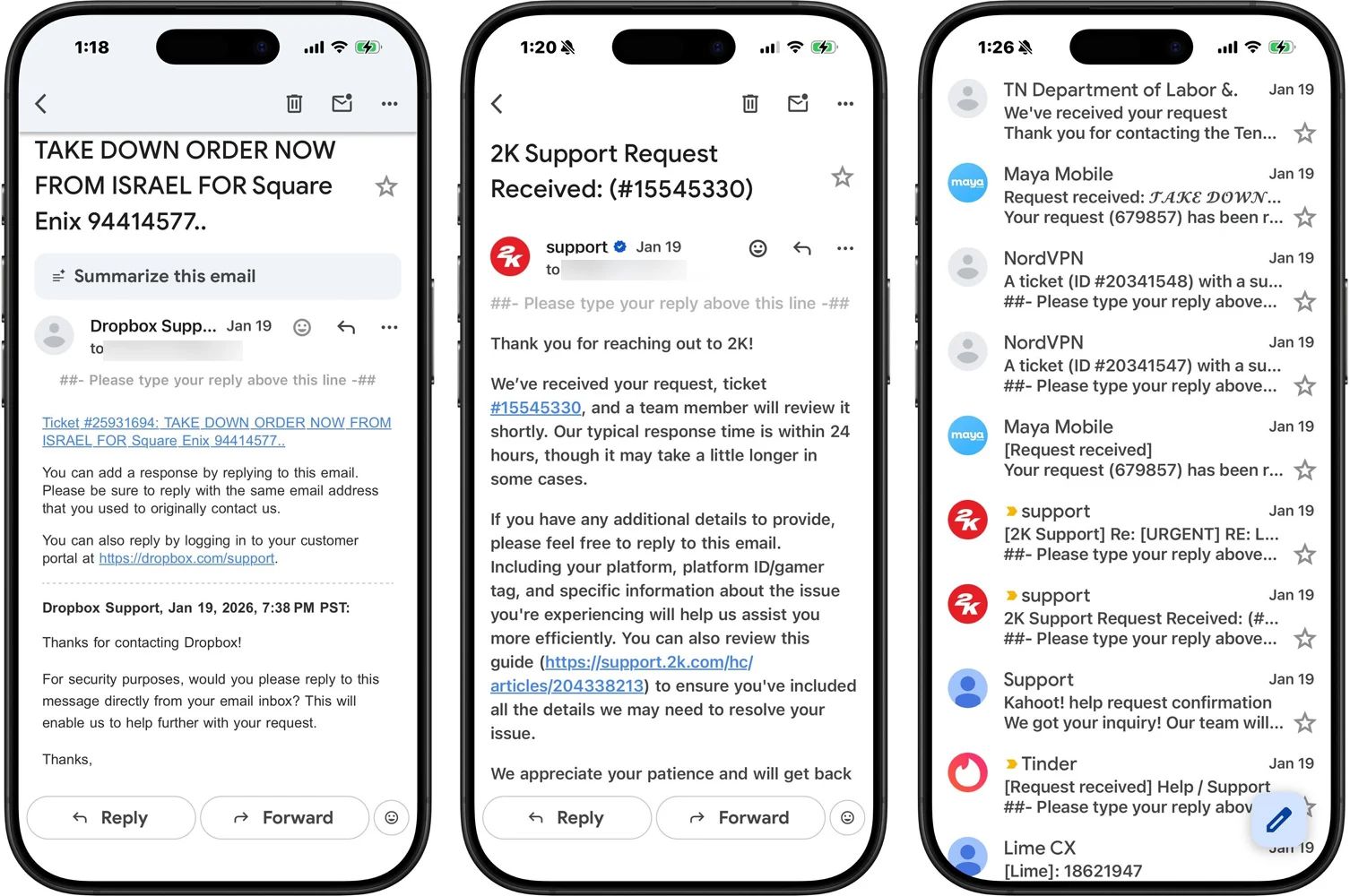
Looks like someone figured out a pretty clever way to turn customer support systems into spam cannons. Attackers have been mass-creating fake Zendesk tickets using random people's email addresses, which automatically triggers confirmation emails to those addresses. Since Zendesk allows unverified users to submit tickets by default, this turned into a perfect storm - hundreds of emails flooding inboxes with bizarre subject lines like "FREE DISCORD NITRO!!" and "LEGAL NOTICE FROM ISRAEL FOR koei Tecmo."
The beauty (or horror) of this is that the emails are coming from legitimate company domains like Discord, Tinder, and Dropbox, so they sail right past spam filters. While the emails don't contain malicious links - this seems more like large-scale trolling than actual phishing - companies are scrambling to respond. Zendesk says they've rolled out new safety features and previously warned customers about this "relay spam" issue back in December. The fix is pretty straightforward: restrict ticket creation to verified users only. (read more)
North Korea is absolutely cooking all sides of the job market. Besides getting hired as spies for remote jobs, they also are targeting job seekers with malware that they deliver during the interview. Researchers spotted them evolving their "Contagious Interview" campaign to abuse Visual Studio Code's task configuration files. Definitely check the attack details here, I covered this on my live stream this week.
Victims get tricked into cloning malicious Git repos (usually during fake job interviews), and when they open the project in VS Code, the tasks.json file automatically executes malicious JavaScript that establishes a backdoor on their system.
The payload itself is a Node.js backdoor that phones home every 5 seconds and can execute arbitrary JavaScript commands remotely. Most developers trust VS Code prompts and won't think twice about opening a repository. The malware is hosted on Vercel (because of course it is), and Jamf noticed the URLs changing multiple times as infrastructure got taken down. If you're using VS Code, maybe think twice before hitting "trust" on repositories from strangers, especially during those suspiciously well-paying remote job interviews. (read more)
Under Armour's having one of those "we're aware of claims" moments after 72 million customer records got dumped on a hacker forum. The Everest ransomware crew apparently grabbed the data back in November, but it only became big news this week when Have I Been Pwned got hold of it and started firing off breach notifications. The stolen goods include the usual suspects - names, emails, birthdates, locations, and purchase history.
What's amusing is Under Armour's response strategy here. They're doing the classic corporate dance of acknowledging "claims" while insisting only a "very small percentage" of customers had "sensitive" information compromised. They won't define what "sensitive" means or give actual numbers, which is always a good sign. At least they're saying payment systems and passwords weren't touched, so that's something. Still, 72 million records is 72 million records. (read more)
Yet another European nation proposing breaking into our encryption. FOR YOUR SAFETY. A new law on the books that would let their cops use tools from the usual - NSO Group, Intellexa, and Paragon Solutions. The Communications (Interception and Lawful Access) Bill is being pitched as necessary because their current 1993 surveillance law predates encrypted messaging apps. Fair point, really - trying to investigate crimes when everyone's using Signal and WhatsApp with a law written before most people had dial-up internet.
The government promises safeguards - judicial authorization, proportionality tests, etc. But this fits into a broader European pattern where spyware is becoming normalized despite plenty of abuse scandals across the continent. From Germany's "Bundestrojaner" back in 2011 to more recent messes in Greece, Hungary, and Poland, European authorities have been quietly using this stuff for decades. Ireland's just making it official and trying to do it with proper oversight, which is probably better than the alternative of doing it in legal gray areas.(read more)
Arctic Wolf's been tracking a new wave of automated attacks hitting Fortinet FortiGate devices since mid-January. The bad guys are exploiting SSO vulnerabilities to log in with bogus accounts like "cloud-init@mail[.]io," then immediately downloading firewall configs and creating persistence accounts with generic names like "secadmin" and "itadmin." The whole process happens within seconds, suggesting it's fully automated - classic mass exploitation stuff.
This campaign builds on activity Arctic Wolf spotted in December, tied to those critical auth bypass vulnerabilities CVE-2025-59718 and CVE-2025-59719 that Fortinet patched. The attackers are hitting devices with FortiCloud SSO enabled, bypassing authentication with crafted SAML messages. If you're running FortiGate gear, now's a good time to check those logs for the IOCs they've shared, reset any compromised creds, and consider temporarily disabling FortiCloud SSO login until Fortinet sorts this out completely. The speed and automation here suggests this is going to be a busy few weeks for anyone with exposed management interfaces. (read more)
The UK's House of Lords just voted to ban social media for kids under 16, and they weren't messing around - 261 to 150 margin on an amendment to the Children's Wellbeing and Schools Bill. Now it heads back to the House of Commons, where MPs could still kill the provision if they want. The government's already studying Australia's approach and considering other measures like raising the digital age of consent and imposing phone curfews.
The debate got pretty intense, with Lord Nash calling it a "societal catastrophe" and citing kids spending 7+ hours daily on social platforms. Medical college presidents apparently signed a letter about "horrific cases" they've treated - and as one peer noted, getting 23 medical college presidents to agree on anything is like herding cats. Not everyone's on board though. Some Lords pushed back, arguing there's no clear causal link between social media and mental illness, with one saying Parliament might as well "ban the internet for everyone." (read more)
Miscellaneous mattjay
How'd I do this edition?It's hard doing this in a vacuum. Screaming into a void. Feedback is incredibly valuable to make sure I'm making a newsletter you love getting every week. |
Parting Thoughts:
Community was foundational in launching and propelling my career. Community is the only reason I can stand being in Texas during the summer months. Community is the point. Today, I invite you to embrace discomfort on the road to a more vulnerable you.
Stay safe, Matt Johansen
@mattjay
