- Vulnerable U
- Posts
- 🎓️ Vulnerable U | #153
🎓️ Vulnerable U | #153
Moltbot mania, Sandworm nearly knocks out Polish power grid, MongoDB ransom hacks and much more!
Read Time: 5 minutes

Brought to you by:
Howdy friends!
What a decade this month has been, eh? I’m in a few group chats that have just absolutely going bananas on AI agents lately. Moltbot is just the latest iteration of this, but people are really worked up.
I’m making some pretty massive moves in my personal and professional life right now. Like a lot of built up potential energy is turning kinetic and honestly it’s super stressful. It’s really easy to not do much, but there is something energizing about the dam breaking.
There is a chance some of these moves don’t work out the way I’m hoping, and I had to actually say out loud to myself in the car today: “So what? The worst that happens is you’re really sad about this. You’ve been really sad before.” - this might sound dumb but its a pretty big deal for someone who historically has struggled a lot with mental health issues. - It reminds me of something I say to my daughter when she’s scared to do something new: “But what if its awesome?”
So that’s my challenge to you this week, what potential energy are you building up that really could be kinetic by now? What’s stopping you? And what if its awesome?
ICYMI
🖊️ Something I wrote: Actual encryption expert weighs in on the WhatsApp lawsuit
🎧️ Something I heard: This guy is the Moltbot biggest fan. I’m not going full out like him, but it’s important to keep track of how people are using these tools as security teams.
🎤 Something I said: The Sloppocolypse has arrived! A metric ton of newly vibecoded mobile apps are leaking millions of people’s data.
🔖 Something I read: Brandon Sanderson just sold his Cosmere universe to Apple TV - I’m a huge Cosmere fan, and have read nearly all of it. This is extremely exciting news for me.
Vulnerable News

Moltbot, formerly known as Clawdbot, is the first AI agent I’ve seen go this viral since ChatGPT, and that hype comes with real security consequences. It’s a one-person, open source project that people are treating like a 24/7 employee, installing it on Mac minis, VPSes, wiring it into email, local file systems, browsers, SaaS tools, and even messaging apps like Telegram, WhatsApp, Signal, and iMessage. The big selling point is its long-term memory, which means it happily remembers all your API keys, OAuth tokens, bot tokens, and secrets. That’s powerful - and terrifying - especially when you remember we still don’t have a good answer to prompt injection.
A lot of the noise around Moltbot, like “hundreds of critical vulnerabilities” and scary SHODAN screenshots, has been exaggerated or misunderstood. Yes, there are real issues: plain-text secret storage, misconfigured admin UIs on the open internet, and a skills ecosystem where people blindly install untrusted code. A security researcher proved how fragile that trust is by creating a fake “What Would Elon Do?” skill, gaming the download counter, and showing how easily a malicious skill could exfiltrate everything from SSH keys to entire codebases. On top of that, malware authors are already piggybacking on the hype with fake VS Code extensions. My stance isn’t “never touch this”; it’s that we, as security people, must take this seriously, understand the threat model - especially prompt injection - and help users set this up safely instead of just screaming “no” from the sidelines. (read more)

We took five SAST tools that claim “AI” and ran them stock on intentionally vulnerable apps across Ruby, Python, C#, and Java. Then we manually verified every finding. DryRun Security found 23 of 26 seeded vulnerabilities (88%) and nailed most logic flaws, while the nearest competitor landed under half. (read more)
*Sponsored
Advertising from PacketSDK, part of the IPIDEA proxy network
Google’s Threat Intelligence Group and partners just delivered a major blow to one of the largest residential proxy networks in the world, IPIDEA, by seizing control of critical domains and disrupting its command-and-control infrastructure, significantly reducing the pool of hijacked devices available for misuse. The operation controlled millions of consumer devices through SDKs embedded in over 600 Android apps and thousands of Windows programs. They were powering botnets and providing cover for threat actors from China, North Korea, Iran, and Russia to launch espionage campaigns and cyberattacks.
Google went after the command-and-control domains, coordinated with Cloudflare to mess with their DNS resolution, and got Google Play Protect to automatically nuke any apps with IPIDEA code. The network operated under a dozen different brands like Luna Proxy, PIA S5 Proxy, and ABC Proxy to hide its true scope. Most users had no idea their devices were being used as exit nodes for criminal activity - they just downloaded what looked like legitimate VPN apps or games that happened to have the malicious SDK baked in. (read more)
When the CISA chief becomes the cautionary tale: What a public ChatGPT upload teaches security teams

Well, this is awkward. The acting head of CISA uploaded sensitive government documents to public ChatGPT last summer. Madhu Gottumukkala had specifically requested permission to use the AI tool when it was blocked for most DHS employees, then apparently went ahead and fed it "for official use only" documents. Cybersecurity sensors caught the uploads and triggered multiple alerts, leading to a DHS-level review.
While the documents weren't classified, they were marked sensitive for a reason - the kind of stuff that could create security or operational risks if it gets out. The irony here is pretty thick. CISA disputes some details and says he had "authorized temporary exception," but this adds to a string of controversies during his tenure, including that whole failed polygraph situation. Not exactly the steady leadership you'd want at the cybersecurity helm. (read more)
Google is going after Lighthouse, a Chinese phishing-as-a-service platform that's popped over 1 million victims across 120 countries. 25,000+ active phishing domains at any given time, 600+ templates spoofing 400+ brands, and they claim to have "300+ front desk staff worldwide." This is the crew behind those USPS and toll road SMS phishing waves that hit basically everyone's phone last year.
You get an SMS about a missed package or unpaid toll, enter your card on their site, and they immediately try to enroll it in Apple Pay or Google Pay on their device. Then they wait 7-10 days (so you forget about the weird text) and drain your account. Google is using RICO …the mob law… to argue Lighthouse operates as an organized criminal enterprise with specialized teams: developers, data brokers, spammers, theft operators, and Telegram-based admin support. Most of their infrastructure sits on Tencent and Alibaba in China, which makes enforcement tricky, but a default judgment could pressure those providers. (Krebs has more technical details)
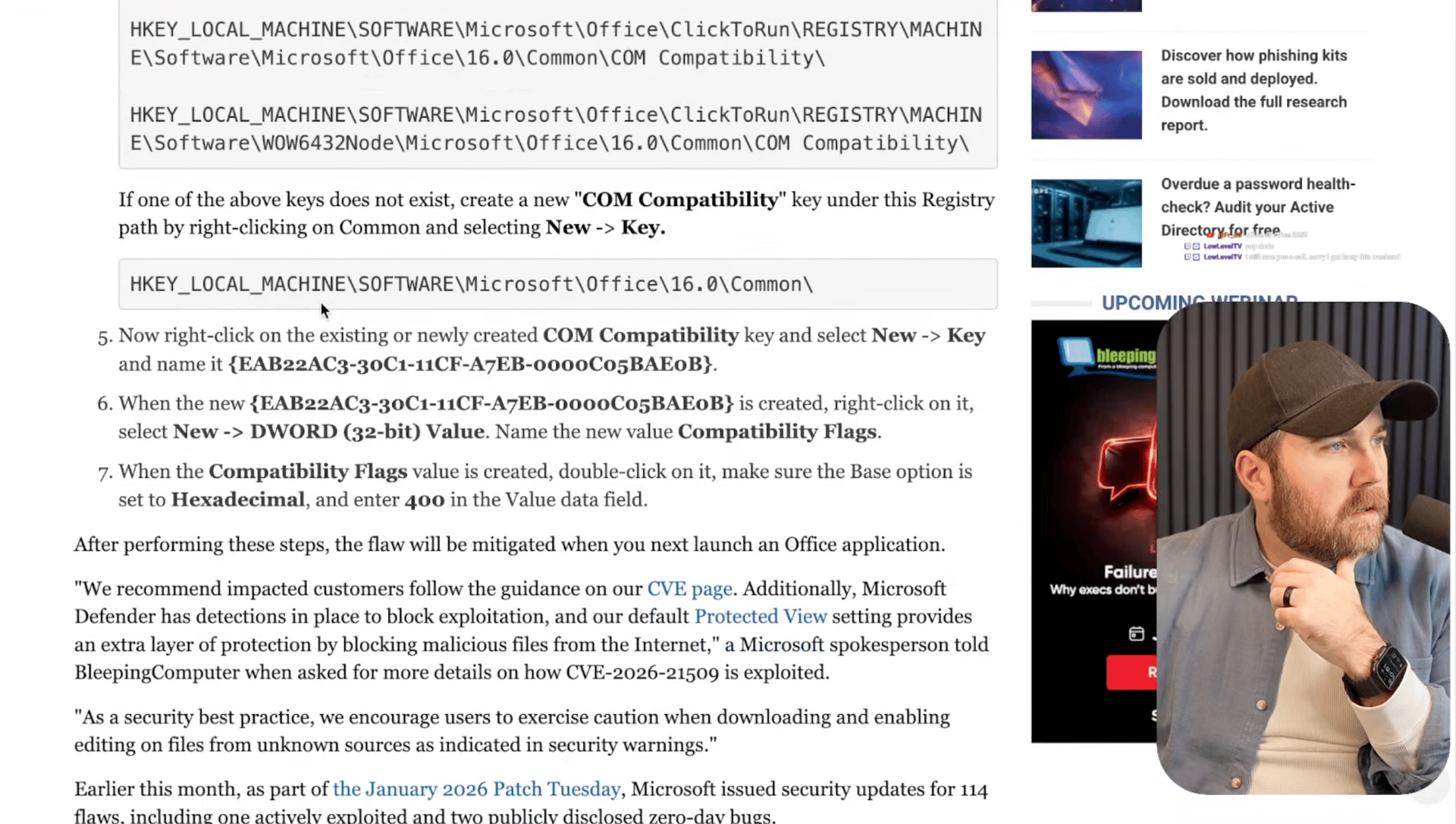
Microsoft just dropped an emergency patch for a nasty Office zero-day (CVE-2026-21509) that's actively being exploited in the wild. This one's a security feature bypass that lets attackers dodge OLE mitigations by sending malicious Office files and convincing users to open them. The vulnerability hits pretty much every Office version from 2016 onwards, including the cloud-based Microsoft 365 Apps for Enterprise.
The good news is that if you're running Office 2021 or newer, you're getting automatically protected via a service-side update - just restart your Office apps to activate it. For everyone else stuck on older versions, Microsoft provided some weird registry tweaks as a workaround that involve creating specific COM compatibility keys. It's part of a busy patch cycle - January 2026 Patch Tuesday already fixed 114 flaws including three zero-days, so this emergency update shows they're taking active exploitation seriously. (read more)
Threat actors don't break in — they log in. Download the Workforce IDV checklist for seven must-have features to defend against credential attacks and make identity your first line of defense. Download now.
*Sponsored
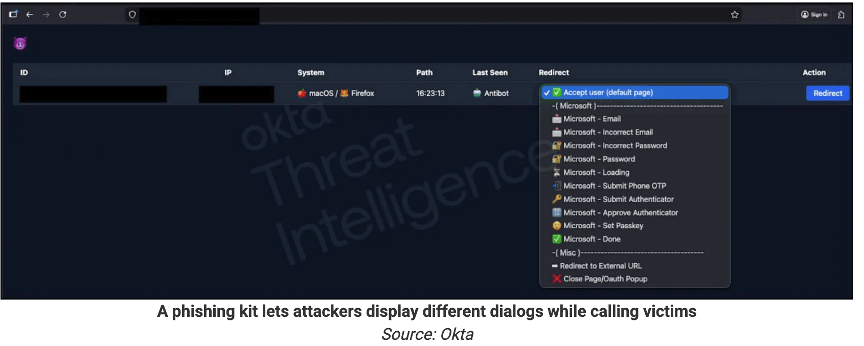
ShinyHunters just confirmed they're behind a wave of voice phishing attacks targeting SSO accounts at Okta, Microsoft, and Google. They’ve been screaming their playbook from the rooftops. This should literally be a “don’t solve anything else until you solve this” kind of issue. They call employees pretending to be IT support, walk them through "logging in" to fake company portals, and harvest their credentials plus MFA codes in real time. Once they compromise that SSO account, they've got keys to the kingdom since most companies connect everything through these platforms - Salesforce, Office 365, Slack, etc. I’ve seen companies with hundreds of tiles in Okta.
The group told BleepingComputer that Salesforce remains their main target, with everything else being "benefactors." They're using data from previous breaches to make their social engineering calls more convincing, with names, phone numbers, and job titles. They've also relaunched their leak site showing off fresh victims including SoundCloud, Betterment, and Crunchbase. (read more)
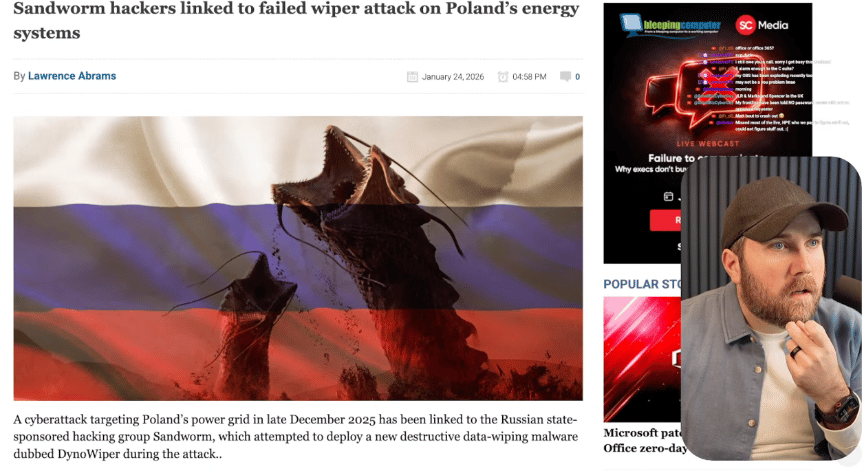
Remember those Ukraine power grid attacks from 2015 and 2016? Well, it looks like Sandworm (Russia's GRU hackers) took a swing at Poland's grid in December, but this time they went after a different target - about 30 distributed renewable energy sites instead of big centralized facilities. They managed to brick the communication devices (RTUs) at these locations, but didn't actually cause any blackouts. Dragos, who investigated one of the hit entities, says the attack felt "opportunistic" rather than a well-orchestrated operation.
What's interesting here is this marks the first major cyberattack specifically targeting distributed energy resources - all those smaller wind, solar, and combined heat-and-power facilities that are becoming a bigger part of modern grids. The attackers exploited vulnerabilities in edge systems and firewalls that had the same configurations across multiple sites, making it easy to hit them all at once. They also deployed wiper malware on IT systems, going for that IT/OT combo punch we saw in Ukraine. Polish authorities say if they'd pulled it off completely, it could have taken out power for 500,000 people. (read more)
Marquis, a fintech that helps banks visualize customer data, is pointing fingers at SonicWall after getting hit with ransomware in August. They're claiming the attack happened because SonicWall's own breach earlier in the year exposed firewall configuration files that Marquis had stored in SonicWall's cloud backup service. Now Marquis is eyeing legal action and wants SonicWall to cover the costs of dealing with this mess.
The timeline here is pretty damning for SonicWall - they initially said only 5% of customers were affected by their breach, then quietly admitted in October that actually all customers using their cloud backup got their firewall configs stolen. That's a pretty significant "oops.” SonicWall's asking Marquis for proof, but given hundreds of thousands of people had their personal and financial data stolen, this blame game is about to get expensive for someone. (read more)

Here's a nasty one that should have every developer double-checking their VS Code extensions. Extension security expert, John Tuckner, found a malicious extension on Open VSX that racked up over 5,000 downloads while masquerading as the legitimate Angular Language Service. The thing is sophisticated as hell - it bundles real Angular dependencies to look legit, then drops encrypted payloads that use Solana blockchain transactions for command and control. That's some next-level "etherhiding" right there.
The malware specifically targets developers for supply chain attacks, stealing NPM tokens, GitHub credentials, and crypto wallets. It even geofences itself to avoid Russian systems. What's concerning is the persistence mechanisms and the fact that it sat in the marketplace for two weeks accumulating downloads. Given how many Angular devs are out there with privileged access to repos and packages, this could be the setup for something much bigger. The researchers are warning this might be another "Shai Halud" situation - a dormant worm just waiting for the right trigger to go off. (read more)
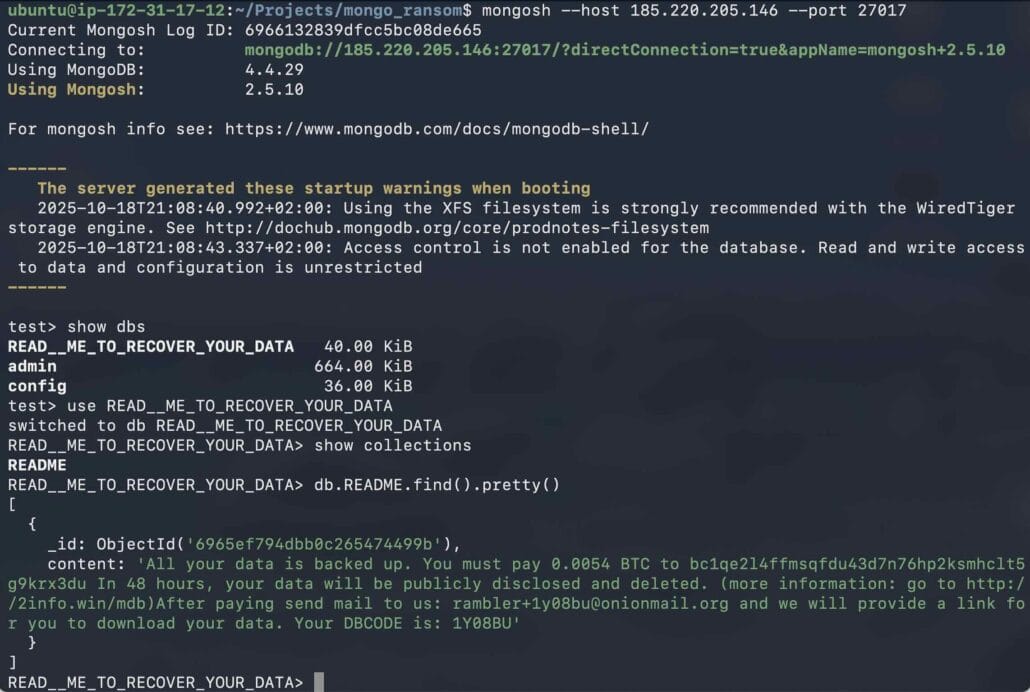
MongoDB ransom attacks never actually went away - they just got quieter. Flare's research team set up some honeypots and got hit within days, which led them down a rabbit hole of discovering this threat is still very much alive. The attack pattern is simple: find MongoDB instances exposed to the internet without authentication, copy or delete everything, leave a ransom note demanding around $500 in Bitcoin. No fancy exploits needed, just basic scanning and capitalizing on terrible deployment practices.
Out of 200,000+ MongoDB instances they found online, about 3,100 were completely exposed, and nearly half of those had already been wiped with ransom notes left behind. Most attacks trace back to just five Bitcoin wallets, suggesting one dominant actor is running this as a profitable side hustle. They even found tutorials on dark web forums teaching people how to do this stuff - complete with step-by-step instructions and Telegram support channels. They discovered 763 Docker images on Docker Hub with the exact insecure configurations that make these attacks possible, showing how copy-paste infrastructure is perpetuating the problem. (read more)
I’ve been live streaming a few times a week recently. Tuesday Thursday mornings will be my usual schedule unless I’m traveling (which I am this upcoming Tuesday) - but if you’re this far in the newsletter, you’re probably into my yapping about the news, come hang out.
Miscellaneous mattjay
How'd I do this edition?It's hard doing this in a vacuum. Screaming into a void. Feedback is incredibly valuable to make sure I'm making a newsletter you love getting every week. |
Parting Thoughts:
Community was foundational in launching and propelling my career. Community is the only reason I can stand being in Texas during the summer months. Community is the point. Today, I invite you to embrace discomfort on the road to a more vulnerable you.
Stay safe, Matt Johansen
@mattjay