- Vulnerable U
- Posts
- 🎓️ Vulnerable U | #154
🎓️ Vulnerable U | #154
WhatsApp encryption debate, Notepad++ exposes nation state supply chain hack, AI powered kids toy nightmares, and much more!
Read Time: 9 minutes
Brought to you by:
Howdy friends!
Crazy week! Flew out to Palo Alto Networks office to film for the better part of 2 days about Quantum Computing and how it’s going to impact security over the next decade. I considered myself on the dumber side of the spectrum on that topic, and now I really feel a whole lot better about it. They even made me get sat for hair and make-up for this level of production, I’ll share when its out.
Spoiler alert: getting ready for Quantum feels a whole lot like other problems we’ve faced in infosec forever. There is a mega complicated layer of physics, qubits, and entanglement on top of the topic, but when it comes to what we have to do to get ready to protect ourselves? We already have the muscles there.
I’ve been battling some MAJOR anxiety attacks lately which isn’t usually my battle, but all my hot buttons have been pressed at the same time. Need to find some time to deal with it, but for now its a one foot in front of the other get through it kind of time.
ICYMI
🖊️ Something I wrote: This skills issue is massively important to understand
🎧️ Something I heard: I’ve honestly been doom consuming a lot of the Epstein content and analysis this week. How about instead I share the new Noah Kahan song that came out.
🎤 Something I said: Ran through the AI kids toy nightmare
🔖 Something I read: Bill Brenner wrote about a topic I’ve been yapping about for a few weeks.
Vulnerable News
It’s amazing how quickly encryption conversations get derailed: a lawsuit or a viral claim hits, “end-to-end encryption is broken” trends, and nuance disappears. This week, a technical breakdown from cryptographer Matthew Green of the WhatsApp lawsuit chatter does something valuable, reminds us what we know and what we don’t here. There are some MEGA claims about Meta employees being able to read any uses’s chats in WhatsApp going all the way back to 2016.
Just a ton of fear mongering this week about Signal and WhatsApp chats being able to be read by companies or the government. The reason I’m picking a real bone with this one is that it is potentially scaring people off of these to less secure options. Elon is screaming about X chat and Telegram founder is popping up to seize on these headlines - both of those options are worse encryption and worse for users.
Matthew does a good job pointing out what we can verify, and what we have to take WhatsApp’s word on, and what we can assume would’ve been found if that claim was true. - He’s betting it’s not true, but still recommends Signal. (read more)

A lot of teams are using AI to write code now. It’s fast, it helps move things along, and once you start, it’s hard not to rely on it a bit. But there are some tradeoffs that aren’t always obvious at first.
AI tools are great at understanding intent, but they don’t really understand your security requirements the same way a human does. That shows up over time. Roughly a third of AI-generated code has vulnerabilities, and as more of it makes its way into production, security teams end up with bigger backlogs and less visibility into what’s running.
This executive guide from Palo Alto Networks walks through how to keep using AI without letting those gaps quietly pile up. It covers things like:
Spotting risky dependencies
Managing AI agent access
Staying aligned with newer regulations like NIS2 and the Cyber Resilience Act
*Sponsored
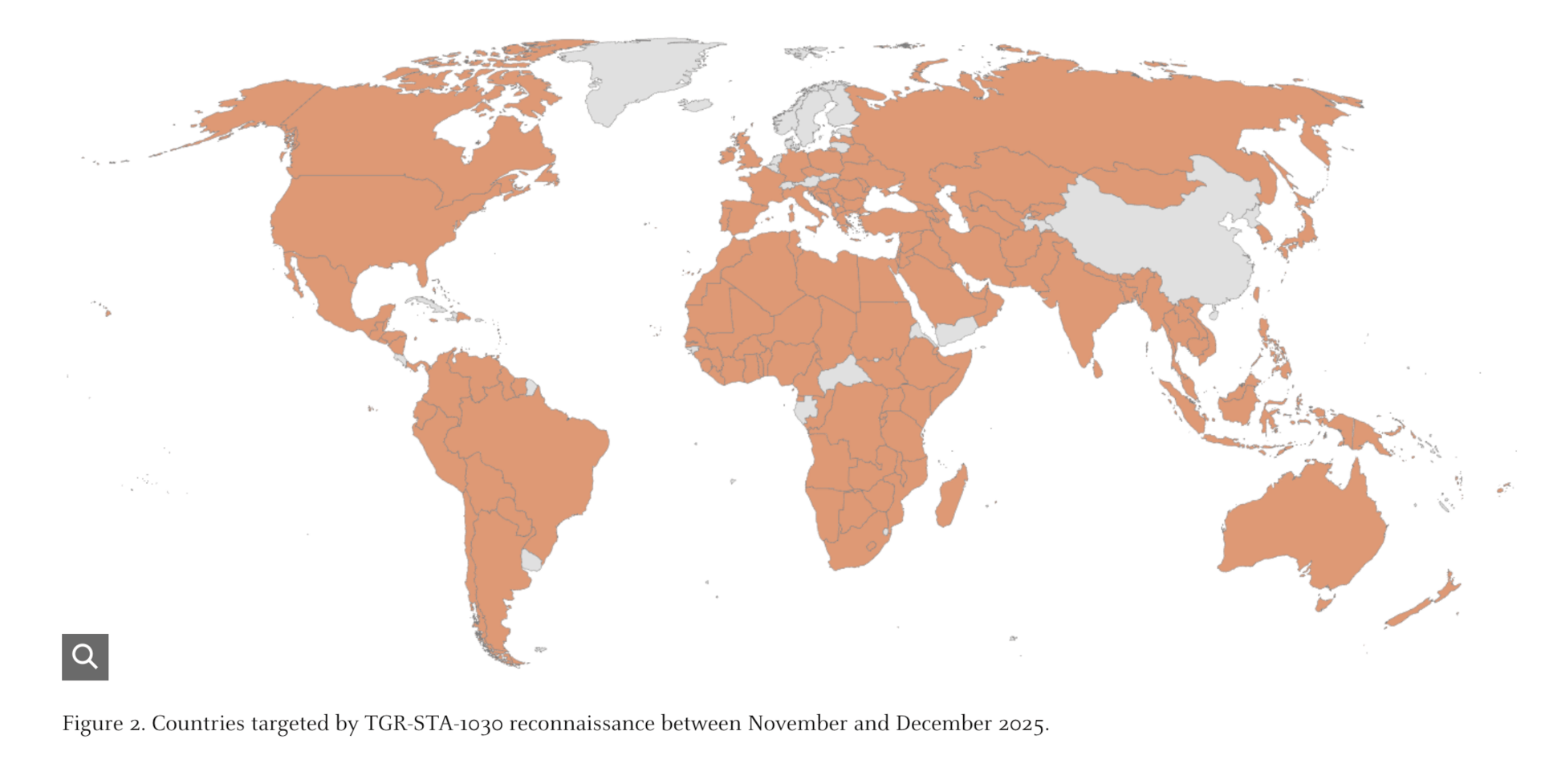
This is a fantastic and thorough threat intel report on a crazy wide spread attack going on right now. It looks like sustained compromise across many countries, aligned with strategic priorities and economic leverage. I scrolled the report while live streaming today and it just. kept. going. A section for every country impacted and why. - The technical deep dives are worth looking at. Their new eBPF rootkit called "ShadowGuard" that operates entirely in kernel space, making it incredibly difficult to detect. They're also using a custom loader dubbed "Diaoyu" with some clever sandbox evasion tricks.
Recon and compromise focused on government and critical infrastructure and a strong emphasis on geopolitical and economic interests, including mining-related targeting across parts of Africa. It also consistently coincided with political activity going on within a few days of the cyber component spinning up. Oh you just made some statement about Taiwan? Or you just imposed some new trade agreements/tariffs? Boom - a flurry of activity out of this group coming your way. (read more)
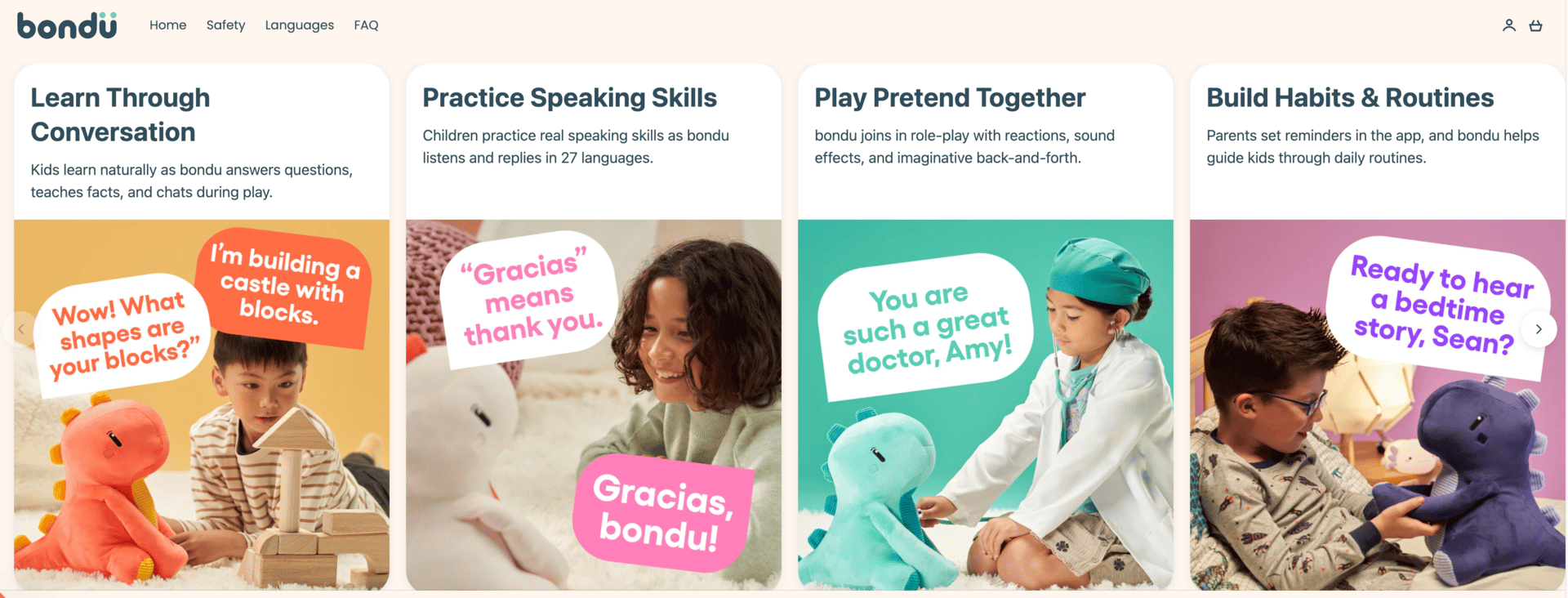
A recent investigation by bug bounty researchers Joseph Thacker and Joel revealed that an internet-connected, microphone-enabled stuffed toy from Bondu exposed deeply sensitive data about children, including full conversation transcripts and personal profiles. The toy functions as a wrapper around large language models like ChatGPT and Gemini, feeding them children’s personal information to generate “personalized” interactions.
Bondu responded quickly and responsibly once notified. But, even when vulnerabilities are fixed, parents are still trusting that employees, and future attackers, won’t misuse or gain access to an internet connected microphone in a child’s private space. Forget about safeguarding it, should this even exist at all? (read more)
AI agents are changing how we think about dev environment security. Package installs, build scripts, toolchain changes, all happening faster than anyone can review. At Minimal, they're rethinking how dev environments should be securely built. Before launch, they want to understand what matters to you, to get you the product that you need. 5-minute survey, results shared.
You even get the chance to to win a gift card from them for submitting!
*Sponsored

Developers behind the open-source text editor Notepad++ say attackers tied to the Chinese government compromised the project’s update infrastructure, allowing malicious updates to be delivered to select users over several months. The attackers didn’t exploit a vulnerability in the application itself. Instead, they breached the hosting environment responsible for serving updates and used it to redirect targeted users to attacker-controlled servers.
The whole thing gives off serious SolarWinds vibes, except this time it's China instead of Russia pulling the supply chain attack. They’ve fixed the vulnerability and terminated the attackers' access, but with tens of millions of Notepad++ downloads out there, this probably hit way more people than we'll ever know. Time to update if you haven't already. (read more)
Last week I discussed the rapid rise of Clawdbot and why its popularity should make security teams uneasy. OpenClaw (the AI assistant formerly known as MoltBot and ClawdBot) just became GitHub's fastest-growing project, jumping from 7,800 to 113,000 stars in a week. It's basically Claude with superpowers - can execute terminal commands, control browsers, access files, and act autonomously on your behalf. Sounds cool until you realize what that actually means from a security perspective.
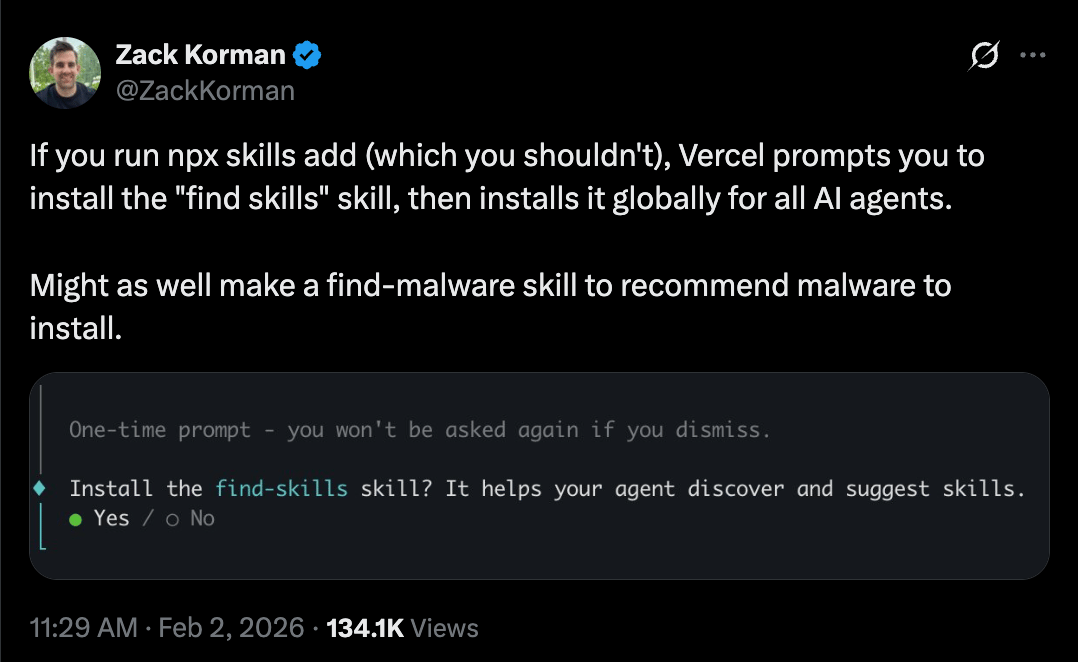
Security researchers are sounding alarms about this "lethal trifecta" - an AI that has access to sensitive data, processes untrusted content, and communicates externally. Token Security found that 22% of employees at their client companies are already using it. With 300+ contributors submitting code daily, which makes for rapid development but also opens the door for supply chain attacks.
The running untrusted skills is one of the scarier parts for me personally. It’s the main way people are interacting and giving this thing “tools” and it also has the chance to just go and do this itself. Oh and prompt injection is a serious concern. (read more)
Russian hackers are getting scary fast at weaponizing patches. APT28 (aka Fancy Bear) managed to reverse-engineer Microsoft's urgent Office patch for CVE-2026-21509 and had working exploits hitting targets within 48 hours of release. That's an impressively short turnaround, even for these guys. They hit diplomatic, maritime, and transport organizations across nine countries with a 72-hour spear phishing blitz, dropping two brand-new backdoors called BeardShell and NotDoor.
If you’re into it, read the whole malware analysis from Trellix, DLL sideloading, memory-based payloads, encrypted everything, and they used legitimate cloud services for command and control to stay under the radar. NotDoor was monitoring email folders and automatically forwarding sensitive messages while covering its tracks by purging sent items. If you weren’t already considering an out of band Microsoft security patch high priority, nows the time to do that. (read more)
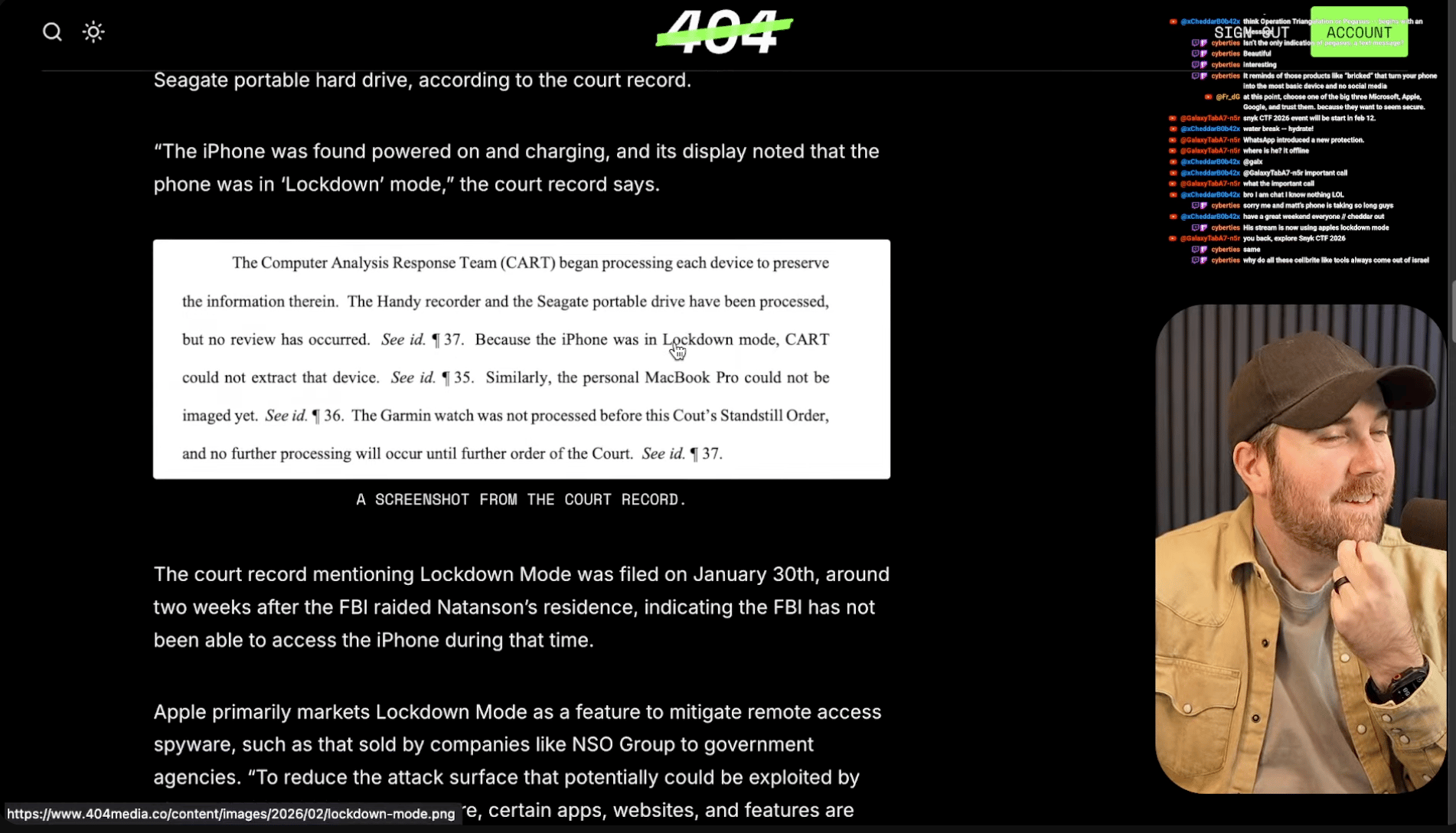
Here's a fun win for privacy advocates - the FBI just admitted in court filings that they can't crack a Washington Post reporter's iPhone because she had Lockdown Mode enabled. Hannah Natanson's device was seized during a leak investigation, but the FBI's Computer Analysis Response Team struck out completely. Lockdown Mode, which Apple markets mainly as protection against fancy government spyware like NSO Group's tools, apparently works just as well against the FBI's mobile forensics gear like Graykey and Cellebrite.
While the FBI couldn't touch her secured iPhone, they easily got into her MacBook Pro when she unlocked it with her fingerprint after agents asked her to "try it." This is probably the clearest real-world evidence we've seen that Lockdown Mode actually delivers on its security promises, at least for now. The cat-and-mouse game between Apple and law enforcement tools continues. (read more)
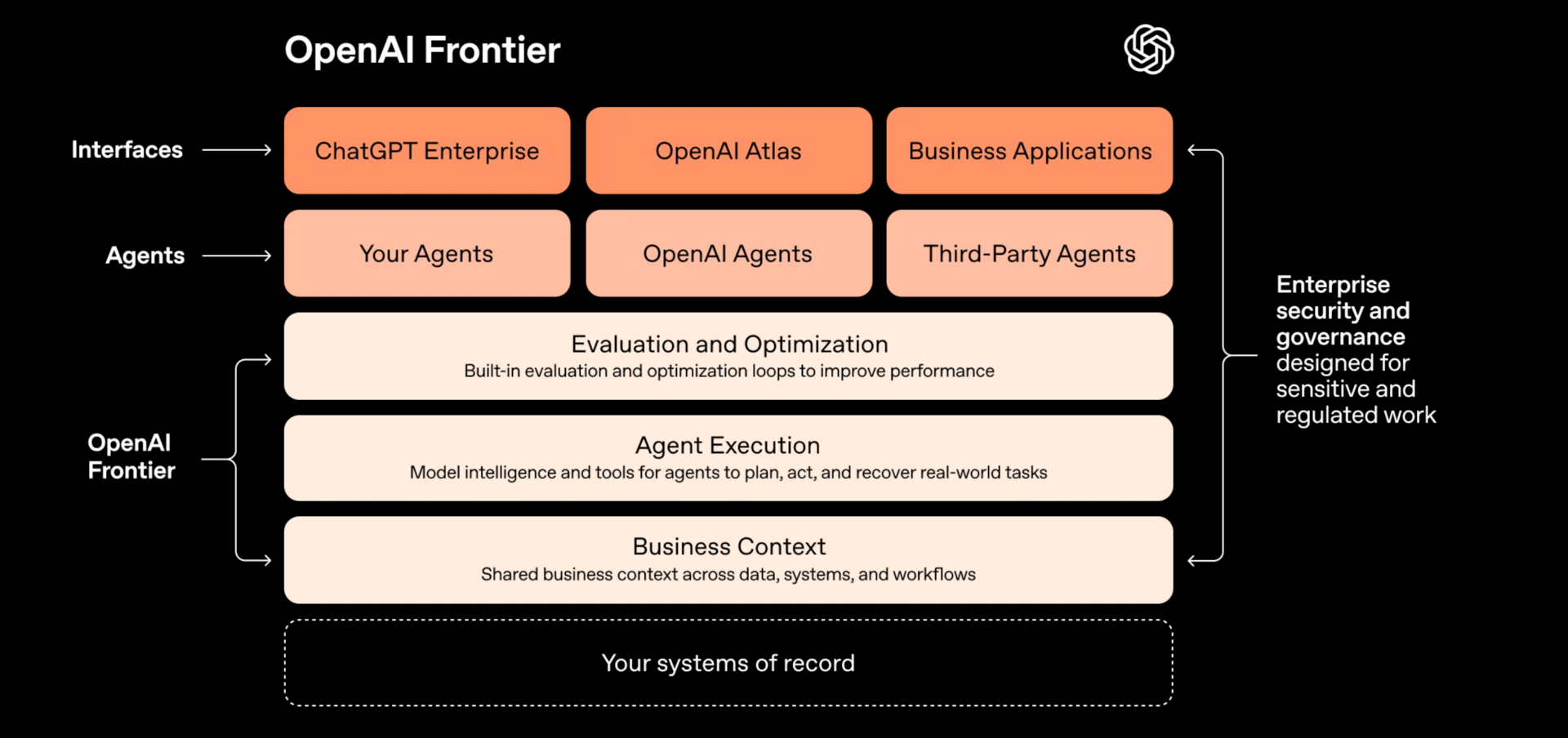
This feels like the Dell vs Apple commercials. Anthropic vs OpenAI on who can put the same features out fastest but focus them towards devs vs enterprises. Last week, I flagged how quickly “AI coworkers” are shifting from novelty to reality for enterprises. This week, OpenAI’s Frontier announcement makes that direction explicit: it’s positioning an enterprise layer that connects business systems, data, permissions, and agent execution so AI agents can function as dependable teammates across real workflows.
The key takeaway isn’t “another agent platform.” It’s the framing: AI systems need shared business context, identity and boundaries, and built-in evaluation and optimization to improve on real work, mirroring how companies onboard and manage people. Frontier also emphasizes interoperability (“open standards,” existing systems, and third-party agents), suggesting OpenAI wants to be the connective tissue between enterprise data and agent execution, rather than forcing a full re-platform. (read more)
Two Chinese APT groups got busy in 2025. First up is Amaranth-Dragon, which Check Point links to the APT41 ecosystem. These folks went after Southeast Asian governments with precision - geo-blocking their infrastructure so only victims in target countries could even reach it. They jumped on a WinRAR vulnerability (CVE-2025-8088) just eight days after it went public. Their toolkit included the usual DLL side-loading tricks and even a custom RAT that uses Telegram bots for command and control.
Meanwhile, Mustang Panda was running their own show called "PlugX Diplomacy," targeting diplomatic officials with fake policy documents. No vulnerability exploitation needed here - just good old social engineering with ZIP files containing malicious LNK shortcuts. Both groups are sticking to proven tactics like DLL hijacking with legitimate signed executables, but the geo-blocking and timing campaigns around political events were interesting to me. (read more)
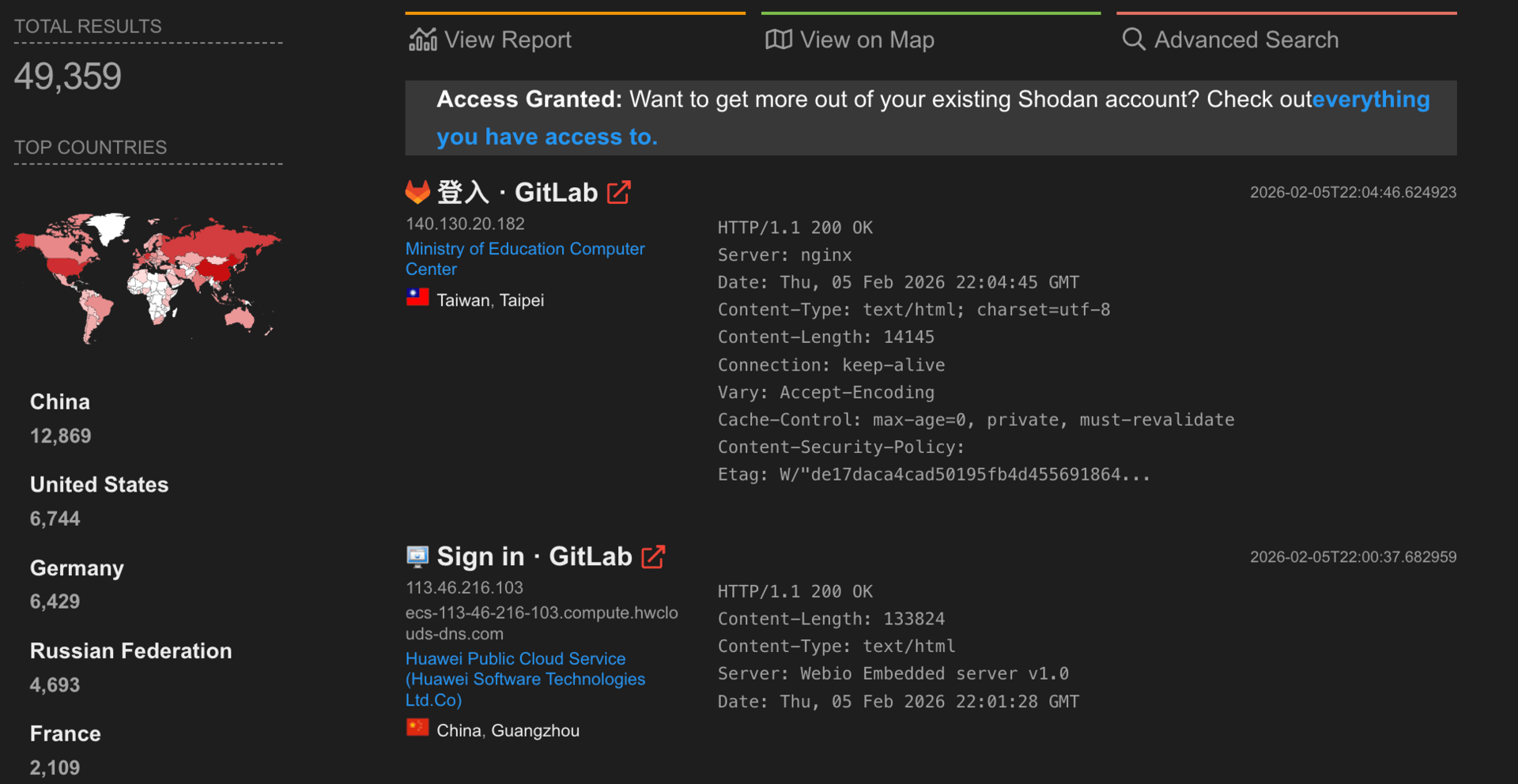
CVE-2021-39935 is an SSRF flaw that GitLab patched way back in December 2021, but it's now being actively exploited in the wild. The bug lets unauthenticated attackers mess with the CI Lint API, which is supposed to be restricted when user registration is limited.
Shodan is tracking over 49,000 GitLab instances still exposed online. Federal agencies now have three weeks to get their act together, but given GitLab's massive footprint (30 million users, half the Fortune 100), this affects way more than just government systems. (read more)
Ukraine just rolled out a whitelist system for Starlink terminals after catching Russian forces slapping the satellite internet gear onto their attack drones. Now only verified and registered devices will work - everyone else gets the boot. The problem is these Starlink-equipped drones are harder to jam and can be controlled in real time from long distances, making them nastier to deal with.
The fix involves citizens registering their terminals at local government offices, while businesses can do it online through e-government services. Military units get their own secure registration channel. As an extra safeguard, they're also implementing a speed limit of around 75 km/h for the terminals - since Russian strike drones typically fly faster, this should cut off real-time control. With over 50,000 Starlink terminals currently operating in Ukraine, this whitelist approach seems like the only practical solution to stop Russia from hijacking the same tech that's been keeping Ukrainian communications alive. (read more)
Developers are catching a nasty React Native Metro vulnerability that's been going around. CVE-2025-11953 lets attackers execute arbitrary commands on Windows and run executables on Linux/macOS through the Metro server's /open-url endpoint. JFrog found this back in November, but VulnCheck spotted active exploitation starting December 21st, with the same PowerShell payloads being dropped consistently across multiple attack waves.
There are roughly 3,500 exposed Metro servers sitting online right now, and this thing still has a low EPSS score despite being actively exploited for over a month. The attackers are being pretty systematic about it - disable Windows Defender, establish TCP connections to their infrastructure, and drop platform-specific Rust binaries for both Windows and Linux. (read more)
Miscellaneous mattjay
How'd I do this edition?It's hard doing this in a vacuum. Screaming into a void. Feedback is incredibly valuable to make sure I'm making a newsletter you love getting every week. |
Parting Thoughts:
Community was foundational in launching and propelling my career. Community is the only reason I can stand being in Texas during the summer months. Community is the point. Today, I invite you to embrace discomfort on the road to a more vulnerable you.
Stay safe, Matt Johansen
@mattjay