- Vulnerable U
- Posts
- ShinyHunters Launches Leak Site for Stolen Salesforce Customer Data
ShinyHunters Launches Leak Site for Stolen Salesforce Customer Data
Dozens of companies report Salesforce-linked data theft. Investigators cite OAuth abuse and social engineering, not a core platform flaw.

A hacking crew operating under the banner “Scattered LAPSUS$ Hunters” has launched a data-leak site to extort companies whose customer records were stolen from cloud databases hosted on Salesforce. The site, which went live Friday, lists dozens of alleged victims and publishes sample datasets while threatening full releases if targets don’t enter negotiations.
The extortion portal is the latest escalation in a months-long campaign that security firms and government agencies say targeted Salesforce customer environments—often via social engineering or compromised third-party integrations—rather than Salesforce’s core platform. In a FLASH alert last month, the FBI warned that two clusters tracked as UNC6040 and UNC6395 have been stealing data from organizations’ Salesforce instances for extortion.
On the new site, the group claims it can leak “~1 billion records” if Salesforce itself refuses to negotiate, and it names 39 organizations it says are under active pressure, including major brands across tech, retail, media, and logistics. BleepingComputer, which reviewed the portal, reports the gang is publishing samples tied to companies such as Google, Cisco, TransUnion, and others.
Separately, posts advertising data linked to the same campaign are circulating on BreachForums, a long-running cybercrime forum whose infrastructure has reappeared repeatedly this year on clearnet and .onion addresses. (Vulnu is not linking to criminal marketplaces.)
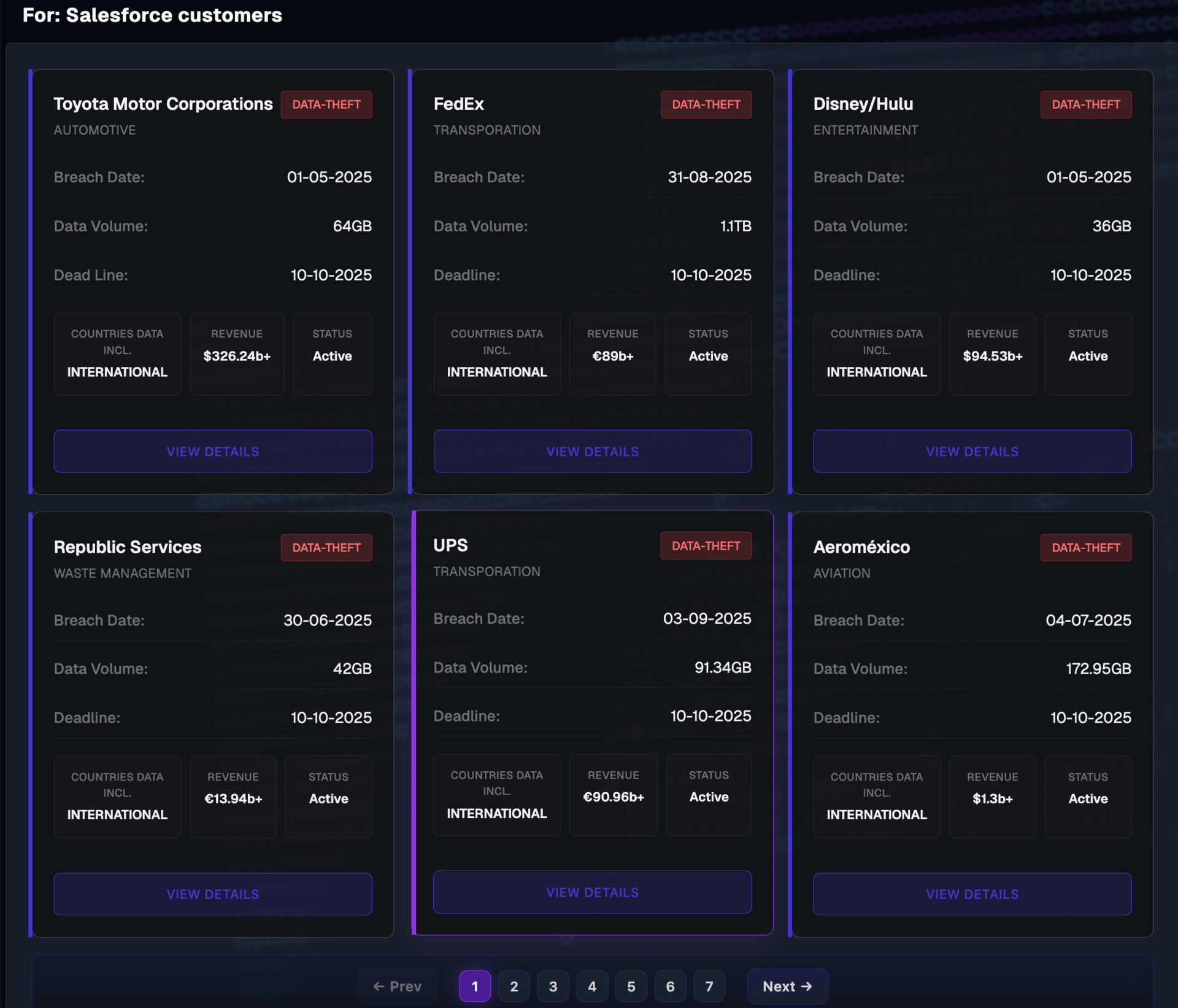
A number of large organizations have already disclosed theft of customer or business-contact data from Salesforce-hosted systems in recent weeks:
Google stated that the attackers accessed a Salesforce database containing SMB contact information, which it tracks as ShinyHunters/UNC6040. TechCrunch reported at the time that Google believed a leak site was being readied.
Allianz Life confirmed that data theft has affected 1.1 million customers in a Salesforce-hosted environment.
Stellantis disclosed theft of customer contact information tied to a third-party platform; subsequent reporting linked the compromise to the Salesforce campaign.
Other companies, including Kering (Gucci, Balenciaga), Qantas, and Workday, have acknowledged related incidents or investigations into data theft linked to Salesforce.
Today’s leak-site launch follows earlier claims by the same crew that they stole up to 1.5 billion Salesforce records across hundreds of companies—figures that remain unverified by independent forensics.
Public advisories describe two primary tracks:
UNC6040 (vishing + malicious tooling): Attackers impersonated IT staff by phone and tricked employees into authorizing access or installing a modified Salesforce Data Loader, then ran automated queries to mass-exfiltrate objects (Accounts, Contacts, Cases, etc.).
UNC6395 (OAuth token abuse via Salesloft Drift): Attackers leveraged compromised OAuth and refresh tokens from the Drift integration to pull data from multiple Salesforce orgs between Aug. 8–18.
Salesforce says the activity does not stem from a vulnerability in its platform. In comments previously provided to news outlets amid the ongoing incidents, the company said there is “no indication the issue stems from any vulnerability inherent in our platform,” characterizing the attacks as targeted social-engineering and third-party integration abuse.
Extortion portals have become the preferred pressure tactic for data-theft crews, even when no ransomware is deployed. By publishing samples and naming companies, threat actors raise legal, regulatory, and reputational stakes to force negotiations. Google Threat Intelligence foreshadowed this exact move in June, warning that actors using the ShinyHunters branding were preparing a leak site to amplify pressure on Salesforce victims.
What’s next
Expect more disclosures. The FBI’s FLASH suggests a broad victim set; today’s leak site names only a fraction.
Data validation will lag. As with prior mega-breaches, verifying the scope and authenticity of each dataset will take time, especially where third-party integrations commingled records from multiple subsidiaries or brands.
Civil litigation is rising. Salesforce and impacted brands already face a wave of lawsuits over customer data exposure, and today’s publication will likely add pressure.
If your organization uses Salesforce
While investigators work to contain the leak, teams should assume compromise if they integrated Drift/Salesloft or observed anomalous SOQL activity in August–September:
Revoke tokens & connected apps; rotate API keys and secrets linked to Drift or other high-privilege apps.
Audit for malicious Data Loader/CLI usage; review logs for unusual User-Agent strings and high-volume exports.
Hunt for credential artifacts in Salesforce records; several victims reported secondary exposure of cloud keys stored in Cases/Attachments.
Follow the FBI’s IOCs and guidance from FLASH-20250912-001.
Follow the Google Threat Intel Remediation Guide
Editor’s note: Vulnerable U does not link to criminal marketplaces. We reviewed the leak-site details and victim list through reputable reporting and official advisories cited above. BreachForums’ role here is referenced only to note wider dissemination of claims; the forum’s domain history is documented in public records.
Further reading:
Salesloft/Salesforce mega-breach roundup: https://www.vulnu.com/p/vulnerable-u-132
Google GTIG + Salesforce campaign coverage: https://www.vulnu.com/p/vulnerable-u-131
ShinyHunters targets Salesforce (context + infra clues): https://www.vulnu.com/p/vulnerable-u-129
Scattered Spider enforcement updates: https://www.vulnu.com/p/vulnerable-u-135
GTIG explainer on vishing/Data Loader abuse: https://www.vulnu.com/p/vulnerable-u-119